The European Union has an IT incident analysis tool called CIRAS. Let’s take a look at this not always well known tool.
What is CIRAS
CIRAS (Cybersecurity Incident Report and Analysis System) is a tool managed by ENISA that aims to collect, catalogue and analyse cyber incidents occurring in European countries. The tool’s official page reads:
In the EU, critical service providers have to report cyber security incidents with a significant impact to the national authorities in their country. At the end of each year, summary reports on these incidents are collected, anonymised, aggregated and analysed by ENISA. The visualisation tool shows the overall EU statistics. (Source: CIRAS)
Thus, CIRAS is fed by the anonymised data that each authority in each European country sends to ENISA. CIRAS is then responsible for representing cyber security incidents through graphs, statistics and summary views. The sectors under analysis are: energy, transport, banking, finance, health, drinking water supply and distribution, digital communications infrastructure, trust and identification services, digital services, government services, other.
According to CIRAS, the computer incidents over the years reported were as follows:
| YEAR | REPORTS |
|---|---|
| 2012 | 77 |
| 2013 | 95 |
| 2014 | 146 |
| 2015 | 138 |
| 2016 | 159 |
| 2017 | 183 |
| 2018 | 175 |
| 2019 | 185 |
| 2020 | 495 |
| 2021 | 559 |
| 2022 | 1083 |
| 2023 | 1271 |
| 2024 | 11 |
What the data tell us
Two interesting phenomena can be seen from this table: the first concerns the transition from 2021 to 2022, when reports almost doubled from 559 to 1083. The second phenomenon is the 11 reports received in 2024. To give a graphic idea of the trend, the situation is as follows. Explaining this phenomenon is important.
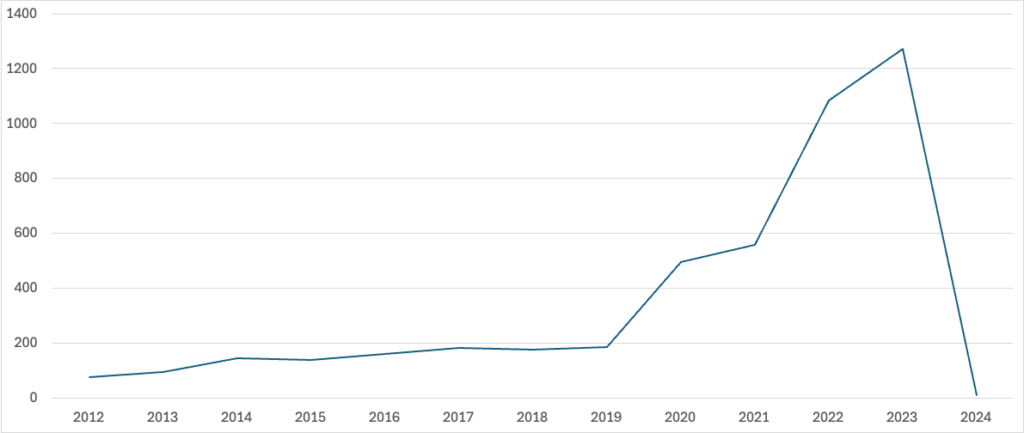
The 2024 data is being updated: on the date this article was started (14 January), there were 11 reports. On 17 January (3 days later), the figure had risen to 34.
The year 2024
Concerning the 11 accidents reported during 2024, CIRAS offers some rather interesting statistics.
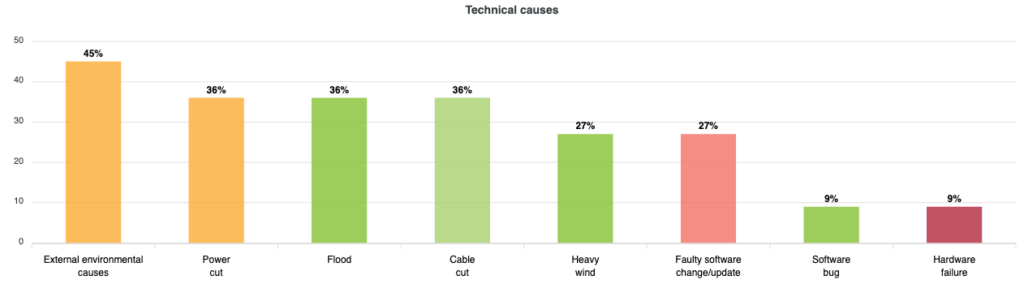
It is clear that the main technical causes attributable to the accident are:
- For 45% external causes.
- For 36% energy losses, flooding/flooding, interruptions in wiring.
- For 27% strong wind, problematic updates
An interesting aspect that can be observed is that among the most recurring reasons are environmental causes, which, for more than a decade, have prompted ISO 27005 to include them as risk factors. If you want to learn more about this topic, we recommend reading this article on environmental risk.
The year 2023
Due to the update status of 2024, it is important to consider more comprehensive data: 2023 is an ideal year. If we try to compare the data with previous years, we learn that in 2023, 459 incidents were reported in Europe from malicious actions (i.e. 36 per cent of the total).
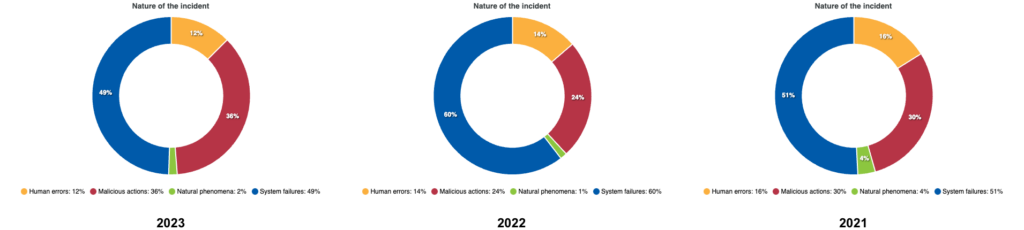
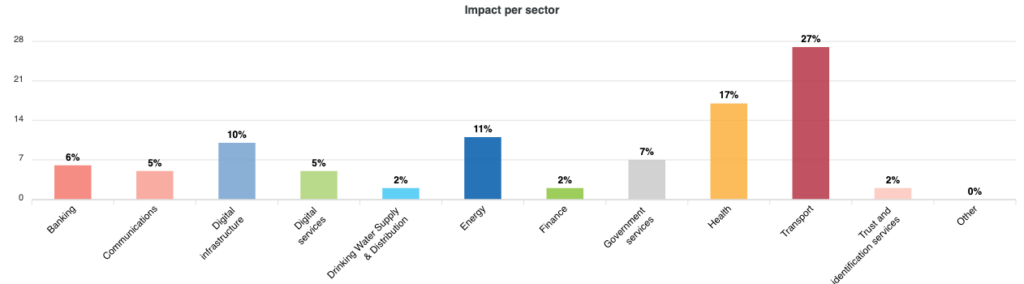
Looking in more detail at arson accidents in 2023, we learn that the greatest impact of these actions was on the transport sector (27 per cent), followed immediately by the health sector (17 per cent), with only the energy sector in third place (11 per cent).
There is one aspect that may come as a surprise to many insiders: the most frequent causes of computer incidents are to be found in phenomena other than malware and ransomware. Of the 1271 total incidents, 459 are attributable to technical causes( culpable and malicious), broken down as follows.
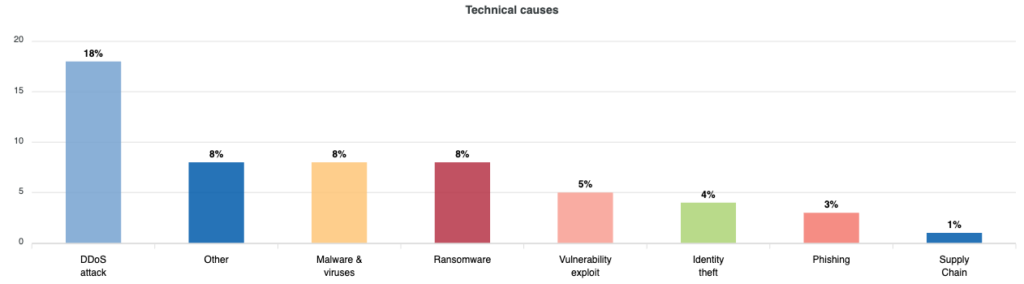
| Type | Percentage |
|---|---|
| DDoS | 18% |
| More | 8% |
| Viruses & Malware | 8% |
| Ransomware | 8% |
| Vulnerability exploit | 5% |
| Identity theft | 4% |
| Phishing | 3% |
| Supply Chain | 1% |
It should be noted that CIRAS makes a distinction between‘malware & viruses‘ and‘ransomware‘ that really should not be there. In fact, ransomware is a type of malware and should therefore be included under‘malware & viruses‘. The government agency CISA (Cybersecurity and Infrastructure Security Agency) writes about this.
Ransomware is a form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable.
Ransomware is a form of malware designed to encrypt files on a device, rendering all files and systems that rely on them unusable
Clearly, the CIRAS decision is necessary to give relevance to a particularly widespread threat. Finally, it should be borne in mind that 10 per cent of all such incidents (1271 occurrences) would hit the following technical targets:
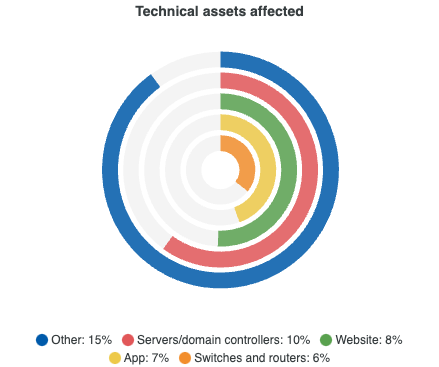
| Asset | Percentage |
|---|---|
| More | 15% |
| Servers and Domain Controllers | 10% |
| Websites | 8% |
| App | 7% |
| Switches and Routers | 6% |
Correspondence between CIRAS and NIS 2
The data collected within CIRAS have an almost complete correspondence with those of the highly critical sectors of NIS 2, here is a table for comparison.
| CIRAS | NIS2 |
|---|---|
| More | Space1 |
| Banking sector | Banking sector |
| Energy sector | Energy sector |
| Financial sector | Financial Market Infrastructures |
| Supply and distribution of drinking water | Supply and distribution of drinking water |
| Digital infrastructure and communication | Digital infrastructure and communication |
| Health | Health sector |
| Digital Services | Management of ICT2 services |
| Trust and identification services | Digital infrastructures3 |
| Government Services | Public administration |
| Transport | Transport |
A few aspects should be noted:
Conclusions
Before proceeding to conclusions, the reader should be informed about the 2024 dataset. Since the cause of this incomplete data set is not known precisely, an e-mail was sent to the CIRAS Working Group on 14 January 2025, but as of 17 January 2025 no response had been received. It was therefore not possible to establish why the 2024 data is so out of date, but it was possible to establish the Working Group’s conduct regarding the request for information.
A first point is the real usefulness of these data. CIRAS is certainly an excellent tool, interesting for its potential comprehensiveness. It is perplexing that in mid-January 2025, one cannot have complete data for 2024. Timeliness in data is important, as well as their fundamental quality. In the context of cybersecurity, the data provided by systems such as CIRAS offer important suggestions on how to direct one’s investments, but if this data were incorrect or arrived late, it could simply be considered less useful, if not completely useless.
A second point concerns reliability. As of the year 2023, the ransomware threat would only be a problem in 8% of the reports.
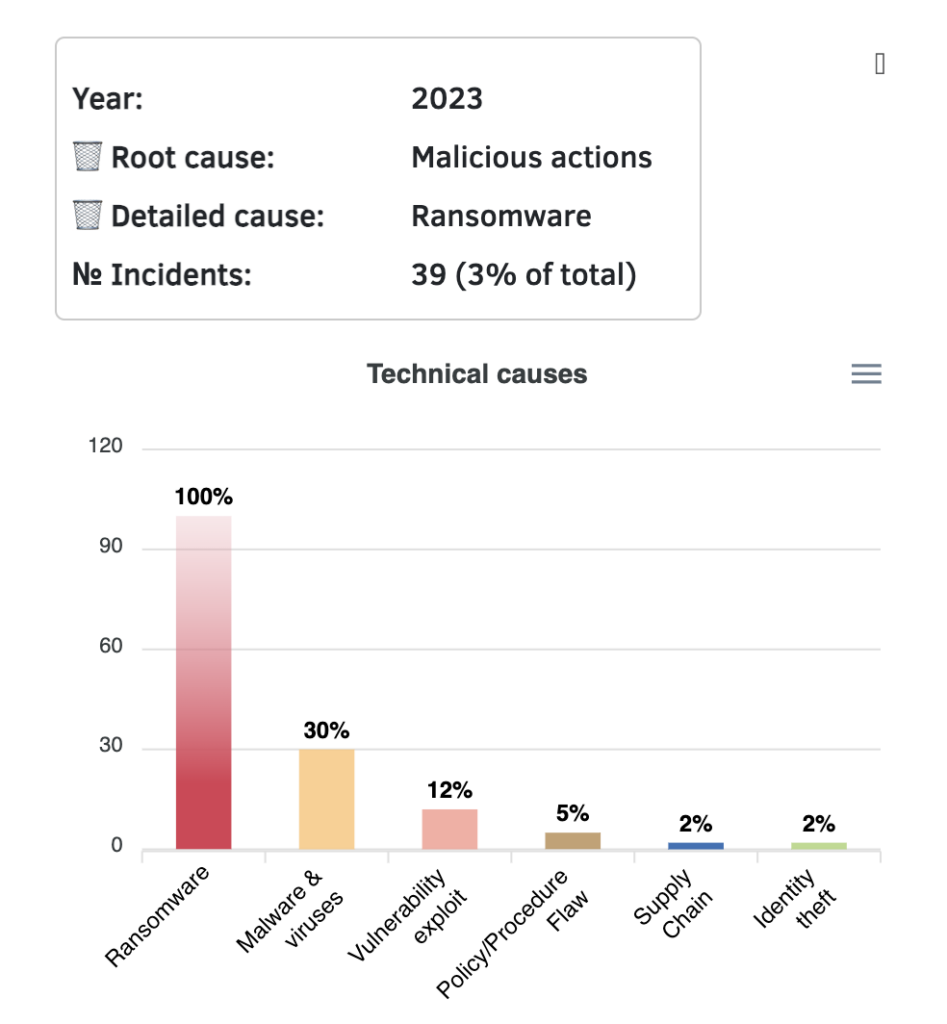
According to CIRAS, there were 39 reports of incidents caused by ransomware in 2023. This is clearly impossible and opens up a front for discussion about the reliability of a European tool that provides critically important data but may be partially incomplete and thus almost meaningless.
A third point concerns traceability. If incidents follow a rigorous process of acquisition, classification and publication, their traceability will be of quality and the data will have value (we speak of data quality management not by chance). Otherwise, this tool will be of little use, if not confusing.
So the question remains: what is the use of a statistical tool that is based on incomplete and late data? To the readers the answer.

