Welcome to the ‘Cyber Anti-Sec’ security report covering the year 2024, in which the most relevant data, trends and data breaches will be analysed.
Introduction
Author’s note
Dear readers, this year the customary annual cybersecurity report will not be published in PDF format, but directly online on this site. This is an important change brought about by the desire to ensure greater usability, also in connection with the fact that the PDF version can still be obtained by saving this article.
The year 2024 was an important year, which confirmed the persistence of the ransomware threat, but also some upward and downward trends in attacks that need to be properly analysed.
It was also the year of the Equalize case, which was widely debated on social networks and in the media, and the Piracy Shield case, which caused a stir due to the almost total inefficiency of the anti-piracy system. Let us therefore try to examine these aspects with the usual ‘data in hand’ to better learn how to defend our companies.
Data, sources and certainties
As usual, the Anti-Sec report refers to reliable data accumulated through official releases, press notes, institutional notices and specific portals. Special thanks go to the Ransomfeed system and staff, widely known in Italy for the quality of the data captured, analysed and published. The platform automatically captures information on ransomware attacks published by more than 160 cybergangs. Every piece of information captured and published by Ransomfeed is checked repeatedly by the staff, which makes the results reliable and of high quality (this work is carried out obsessively by the staff and guarantees unparalleled results).
It is important to point out that Ransomfeed‘s data does not take into account those attacks which, although reported by newspapers and by the ransomware victim companies themselves, have not been officially claimed by the malicious actors. Instead, this report will contain statistics that also include verified but not officially claimed offences.
All cited data will have the reference source for transparency towards the Reader.
Trend of attacks
Overall trend
Let’s start at the beginning: Italy continues to be the target of numerous hacker attacks using ransomware, with a constant number of offensives compared to the past. Many will note a slight decrease compared to the previous year, but this decrease is not yet symptomatic of an improvement: we must wait at least another year before we can assess it as such.
| 2021 | 2022 | 2023 | 2024 |
|---|---|---|---|
| 79 | 132 | 175 | 163 |
This decrease, however, is objective and has resulted in a reduction of the ‘pressure’ on certain regions; it is therefore necessary to investigate the regional distribution of hacker attacks in order to better understand how the phenomenon has developed.
It should be borne in mind that more than 30 Tb of data were exfiltrated in Italy in 2024, and this information, provided by Ransomfeed, conveys the gravity of the situation.
Trends on a regional basis
As predicted, there is a novelty in the regional attack statistics: since 2021, attacks in Italy have concentrated on the richest regions such as Lombardy, Veneto and Emilia-Romagna. Lazio, an institutional region par excellence and therefore a target of interest for hackers, has also been added to these. If Lombardy alone, in terms of profit, is understood as‘the tenth country in the EU‘, it is also true that Lazio is the hub of Italy’s political and institutional activity, but it is Lazio that is the exception.

Lombardy grows, Lazio and Veneto decline
2024 saw a turnaround for regions such as Lazio and Veneto, which recorded a decrease in ransomware attacks, while Lombardy and Emilia-Romagna saw an increase. The data in the table were cross-checked with the Ransomfeed platform.
| Region | 2021 | 2022 | 2023 | 2024 |
|---|---|---|---|---|
| Lombardy | 20 | 26 | 43 | 50 |
| Lazio | 11 | 20 | 24 | 17 |
| Veneto | 6 | 17 | 20 | 14 |
| Emilia-Romagna | 5 | 8 | 17 | 21 |
Other regions (e.g. Piedmont) also recorded a decrease in attacks.
| Region | 2021 | 2022 | 2023 | 2024 |
|---|---|---|---|---|
| Piedmont | 7 | 10 | 13 | 10 |
Ultimately, the hackers’ preference to target the richest regions is confirmed, without clearly disdaining the others, which, however, have much lower numbers at the moment.
Attacks on P.A. and Private Individuals
In the case of Italy, the distinction between private and public administration can be particularly subtle: bear in mind that many rules dedicated to the P.A. also apply to private persons. The Digital Administration Code, for example, also applies to private persons when they become managers of public services (Art. 2(2)(b)).
The provisions of this Code apply […] to public service operators, including listed companies, in relation to services of public interest;
The entrepreneurial fabric of Italy is structured by small and medium-sized enterprises that feed the territory and support the local public administration in various capacities; it is therefore clear that an attack on a private individual could have consequences in the public sphere. Nevertheless, it is interesting to observe the trend data of these offensives.
| Attacks | 2023 | 2024 |
|---|---|---|
| Public Administration | 29 | 12 |
| Private | 146 | 152 |
In this sense, the role of in-house companies that are responsible for the active management and maintenance of public information systems is relevant. Their task puts them directly in contact with public data and infrastructures while often maintaining a private legal form. This is also in the light of the complex regulatory framework that, just to mention the main regulations, includes:
- The Data Protection Regulation (GDPR) EU Reg. 2016/679
- Provisions on strengthening national cybersecurity and cybercrime. Law 90/2024
- NIS 2 Directive with Italian transposition through Legislative Decree 138/2024
Main causes of violations
Lack of adequate procedures
Compared to previous years, there remains a state of widespread neglect in the adoption of policies, strategies and plans to protect data and infrastructure. Companies, even those with certifications such as ISO 27001, 27005, 9001, persist in ignoring data protection and management procedures. There is no problem with software supply or hardware supply, thanks also to tools such as those made available by Consip, about which it is good to provide some certain data. In 2021, Istat surveyed 7,904 Italian municipalities in the document‘ITALIAN STATISTICAL ANNUARY 2021‘.
There are currently 7,904 municipalities in Italy and 70 per cent of the total have fewer than 5,000 inhabitants. The average municipalities, which have between 5,000 and 250,000 inhabitants, total 2,357 and correspond to 30 per cent of the total number of Italian municipalities: 68.3 per cent of the country’s population resides in them. There are only twelve municipalities with more than 250 thousand inhabitants, in which 15.2 per cent of the residents reside.
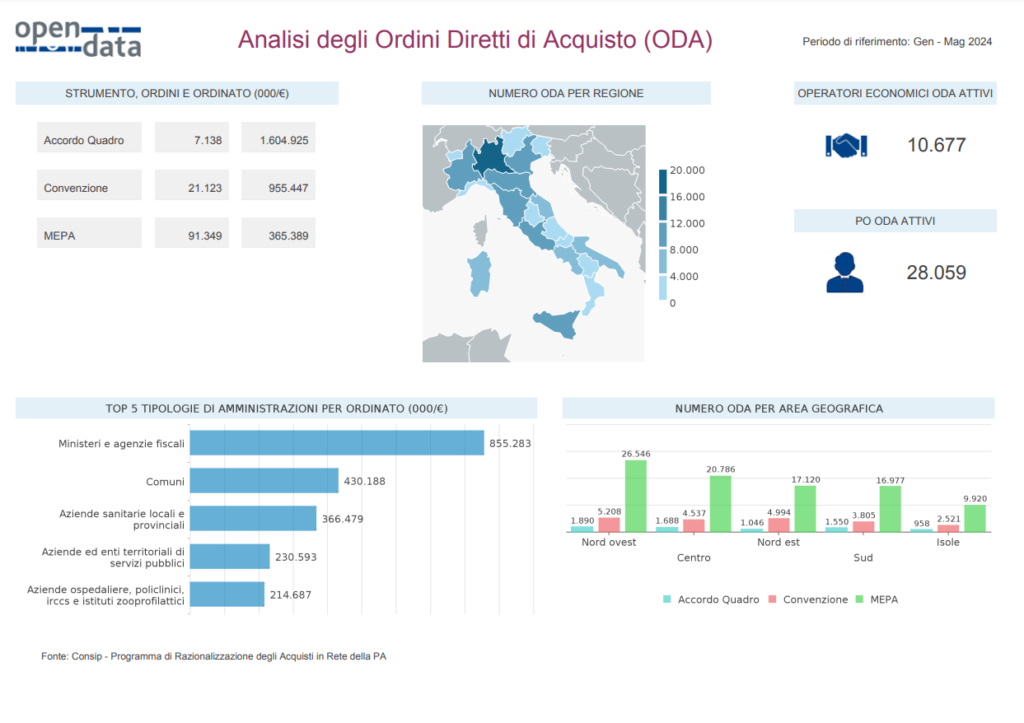
According to statistics provided by CONSIP on Direct Purchase Orders (ODA) in the period January-May 2024, there would have been over 28,000 active ODA ordering points. The ordering point (or PO) is“the user of the Public Administration that is enabled to operate on the e-Procurement platform through the P.A. Network Procurement Portal. It has power of signature and can commit expenditure.” The problem of data breaches lies in the lack of basic procedures such as:
- Backup and restore.
- Operational Continuity
- Disaster recovery
- Management of culpable/dolicious accidents
- Management of relations with suppliers
Many actors do not formalise plans, policies and strategies on the above points, finding themselves disoriented at the time of an incident and unable to react effectively and efficiently.
Overlapping roles
Technical staff often complain that they are unable to actively devote themselves to the systems activity for which they were hired. This consequently leads to a decrease in knowledge of the status of the information system and the need to outsource projects, activities and infrastructure to third parties. This phenomenon can easily be observed since the information systems office, today more than yesterday, is called upon to participate in projects, calls for tenders, and activities of transversal interest. On the one hand, this is physiological: the globalised market has created more opportunities but also more complexity. On the other hand, all this has resulted in a reduction in the time that the subject can devote to technical and systems activities.
Inadequate training
There are still major gaps in both the technical and legal spheres on proper data management, incident reporting, and security policies to be adopted, and in general this can be attributed to two factors:
- There is too little training, often the IT departments are not adequately trained despite having to coordinate infrastructure.
- The training offered is of poor quality.
With regard to the first point, the situation is slightly more complicated: technical IT staff must be kept constantly up-to-date through training courses provided by qualified and competent subjects in the various spheres of interest. These courses could be provided by the vendors themselves or, in the case of IT security, by entities such as CERTs whose activities include specialised training. If technical personnel are not aware of the latest cyber threats, for instance, they will hardly be able to plan the harmonious development of the IT infrastructure or develop and implement an appropriate defence strategy.
Contracts not always complete
The state of contracts for the supply of ICT goods and services contributes to the severity of an IT incident: contracts with inadequate service levels are still found today, preventing a prompt response by suppliers in the event of a data breach. The same applies to the choice of services, which do not always live up to expectations in the event of extraordinary operations with the consequent failure of recovery activities. Clauses are not always included in the formalisation of the relationship with suppliers:
- the management of communication in the event of computer incidents where the supplier or customer is affected;
- the definition of specific procedures to be implemented in the event of a data breach;
- the definition of specific timeframes and modes of intervention.
This is another reason why the NIS 2 directive was relevant, even though these arguments have been addressed by the main international standards for more than a decade(to read more click here).
Inadequacy of credentials
2024 is still the year that marks the misuse and mismanagement of credentials for access to systems and services. During the data breach at the Synlab healthcare facility (May 2024), multiple credential files were exposed that were inadequate to contain the type of data. The passwords themselves were inadequate to secure access to systems and services.
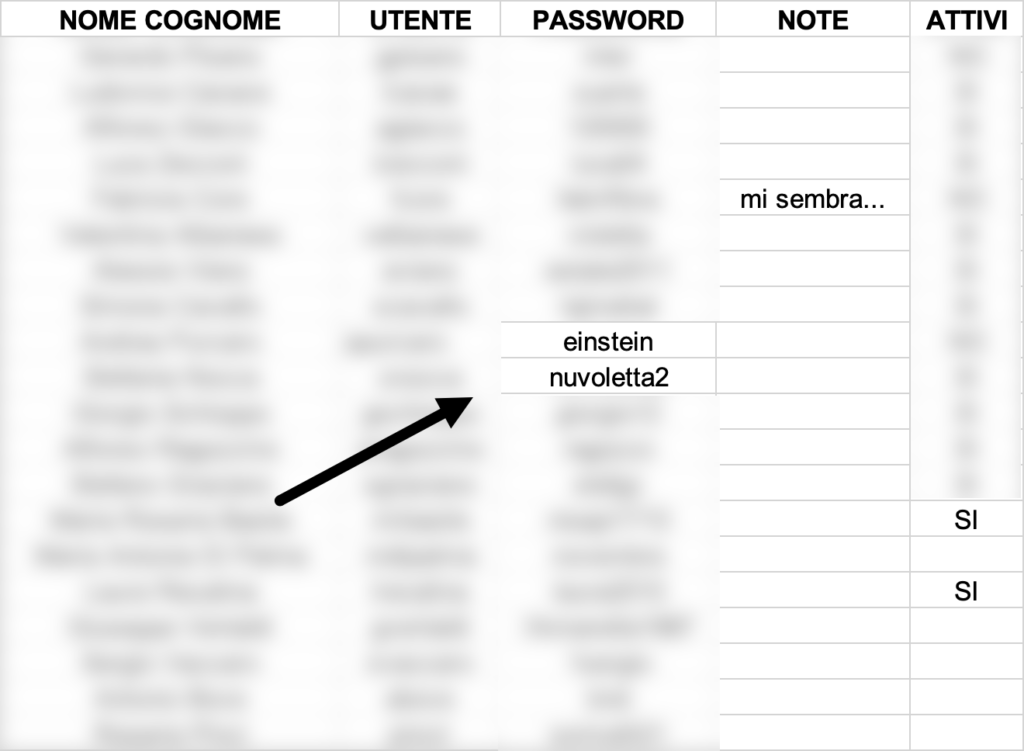
Synlab is not the only case of mismanagement of credentials: it is so common to find credential files within the findings of data breaches that one no longer pays attention to them. The adoption of password managers, nowadays also free of charge, is not adopted as a mere matter of convenience and thus negligence.
Inadequate management for some documents
Medical records, reports, diagnostic analyses, identity documents (even of minors), are often stolen and displayed on the Internet because they are stored without the appropriate security criteria and in violation of the laws in force.

One example among many was the attack on ATOS (July 2024) that exposed dozens and dozens of identity cards including those of a minor. There are driving licences, health cards, identity cards, passports, all stored and managed without the appropriate protection criteria.
The case of the University of Siena
In May 2024, the University of Siena (UNISI) suffered a data breach via LockBit ransomware. The communication, promptly published on the university’s portal, says the following:
Last weekend, the University of Siena suffered an attack on its network infrastructure by a group of international hackers. On the morning of Monday, 6 May, it was therefore necessary to shut down the incoming and outgoing University network and to start operations to verify and clean up the integrity of the infrastructure, with the simultaneous assessment of any damage caused. The University’s IT contact persons immediately reported the attack to the National Cybersecurity Agency, with which they are in continuous contact; they are also preparing the documents to file a complaint with the Postal Police and to report to the Italian Data Protection Authority. The network infrastructure will be gradually restored and will return to normal operation once full security conditions are ensured.
LockBit exfiltrated more than 305 Gb of data to UNISI, with considerable exposure of important files including research papers, examination reports and whatnot.
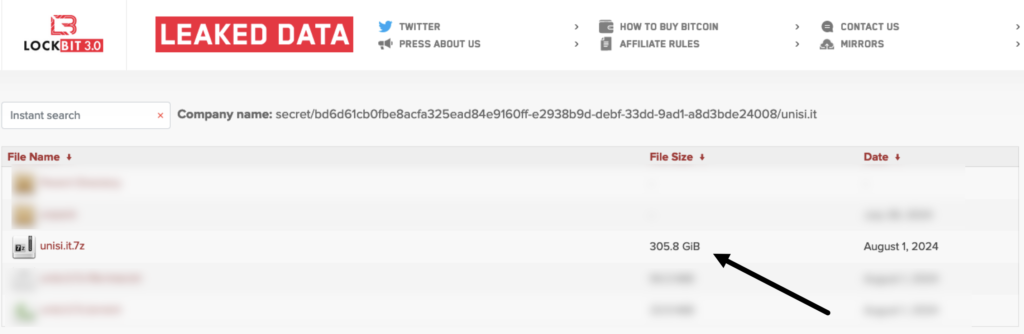
Perhaps many readers will not remember, but UNISI was repeatedly the target of hacker attacks, albeit of a different nature and minimal size. At the time, these were attacks aimed at denigrating the security status of the IT infrastructure, which was considered to be underperforming and lacking in minimum security requirements.
| Date | Actor |
|---|---|
| 06/07/2011 | LulzStorm |
| 22/12/2019 | Anonymous Italy |
| 02/04/2020 | LulzSec_ITA |
| 04/05/2024 | LockBit |
In particular, for the attack on 22 December 2019, the department of GeoTechnology(https://geotecnologie.unisi.it/) was involved. In the most recent attack in May 2024 by LockBit, it was learned that the university’s files were littered with credentials held within files. A brief statistic was attempted on the list of stolen files: certain words such as passwords or credentials were searched in order to count their occurrences.
| File name | Occurrences |
|---|---|
| password.doc(x) | 8 |
| password.txt | 0 |
| password.xls(x) | 1 |
| credentials.doc(x) | 7 |
| credentials.txt | 0 |
| credentials.xls(x) | 0 |
| Total | 16 |
Clearly, each of those files could contain information that is as relevant as it is irrelevant, but assuming that they contain information consistent with the file name, the damage would be substantial.
As written above, universities have always been an object of interest for hackers, both because of the content of the documents produced within universities and research laboratories, and because of the uproar that news of possible data breaches may cause. One example is certainly the one reported by La Nazione in its article of 20 November 2024 on the hacker attacks against the University of Pisa.
The sanction at the Alessandria ASL
On 17 October 2024, the Garante della Protezione dei Dati Personali sanctioned the Azienda Ospedaliero-Universitaria SS. Antonio e Biagio e Cesare Arrigo, of Alessandria for 25,000 euro. Among the reasons taken up and cited by the newspapers was the obsolescence of some software and more; in fact, the segregation and segmentation of the network was missing.
During the investigation it emerged that the company had not taken adequate measures to segregate and segregate the networks on which its employees’ workstations and the systems (servers) used for processing were located.
Among the various irregularities, there was one that did not arouse the curiosity of the newspapers, due to its unintuitive technical level. The company was still using the Server Message Block version 1 (SMBv1) communication protocol.
In relation to the vulnerability found downstream of the attack, consisting of the fact that outdated communication protocols, including smbv1 and NTLMv1, were ‘still active
According to the Authority, the Alessandria ASL had no monitoring of the events that occurred within the ICT infrastructure.
From the above reconstruction, the point of origin, although there is no certain evidence as the company did not have a log management system
But above all, it was revealed that the healthcare company had several suppliers in charge of, among other things, network management.
…initiated joint analysis with the antivirus vendor and the partner operating the network and its active equipment to check for potential vulnerabilities within their competence or containment actions
It is therefore worth reflecting on the fact that the SMB communication protocol in version 1 has been considered obsolete for years. In this regard, Microsoft writes:
Instead of reinstalling SMB 1.0, it is advisable to upgrade the SMB server that still requires it.
Other companies, such as Synology, for instance, advise against the use of this version of the protocol, clearly statingthat ‘enabling SMB1 is not secure and could make the Synology NAS vulnerable to attacks‘, so the question that should be asked is why a healthcare company, which is, moreover, followed by an experienced network management vendor, continues to use a communication protocol that has been discontinued since 2014. This means that a healthcare company has been using an insecure protocol to manage the transmission of the data it holds for ten years. To provide further information on the decommissioning of the SMBv1 protocol, it is worth mentioning that:
- Windows 10 Fall Creators Update (version 1709): SMB1 was disabled by default on new Windows 10 systems, but it was still possible to manually re-enable it.
- Windows Server 2016: SMB1 was disabled by default.
- From 2020: Microsoft has started to completely remove support for SMB1 in some editions of Windows 10
Therefore, the problem is not only software obsolescence, but the lack of attention to the phenomenon of computer security as pointed out directly by the inspectors of the Garante.
The InfoCert case

On 27 December 2024 at 13:47, a message appeared in a popular forum dedicated to the publication and sale of illicit material:‘Italy – Customers of the digital trust solutions operator InfoCert (2024) (5.5 million)‘. Claudio Sono, one of the first to publish the screenshot you see below, commented extensively on the news on X at this link.
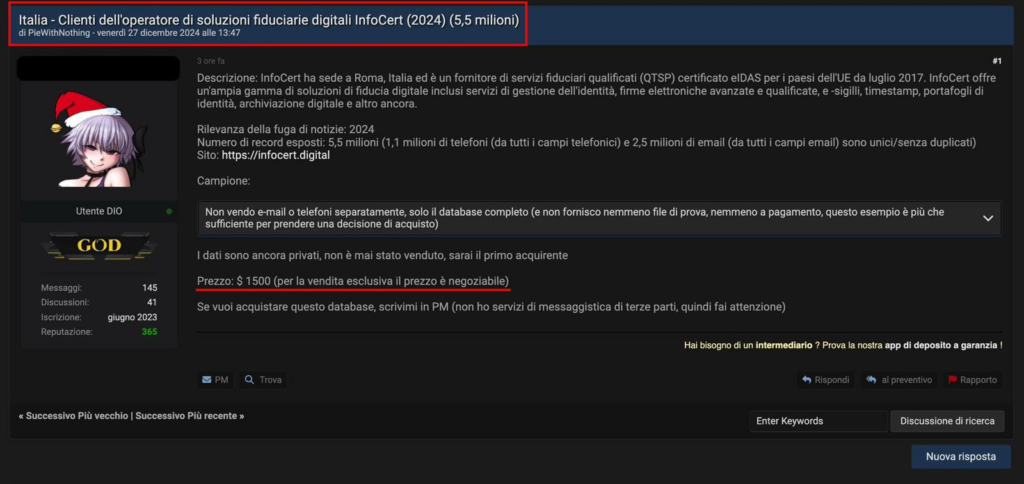
A few days later, resounding clickbait headlines appeared about the SPID digital identity system. Frightening (and false) headlines such as ‘SPID hacked…’ or ‘Data breach at SPID…’; one could talk a lot about the titling of articles, there are newspapers such as ‘Il Post’ that make a daily battle out of it.
What has been hacked is apparently a customer support system of InfoCert services, of which SPID is certainly a part, but also the cadastral view system, the Legalmail system, and so on. This database (as the author of the forum post said after all) contains customer data and not passwords or access codes, but communications concerning the handling of support requests.
Warning: this data breach is no less serious than others. First of all, it is good to remember that credentials are not just passwords; credentials are also the user name with which one logs in and which often coincides with one’s e-mail address. Moreover, it is good to remember that this database contains all the information needed by a malicious actor to set up phishing and social engineering attacks, even quite complex ones. This data breach is serious, even if it does not explicitly contain passwords, because it involves a qualified trust service provider.

Undoubtedly, the company may have contracted out the support service to an external supplier, for which, however, it must be responsible. In this sense, NIS 2 (with transposition in Legislative Decree No. 138 of 4 September 2024), in Art. 24 para. 2 (d), expresses the obligation to ensure the“security of the supply chain, including security aspects concerning the relationship between each entity and its direct suppliers or service providers“.
InfoCert’s warning came one day after the publication of the data breach, which is not the date on which the information was taken from the provider. Many did not appreciate such a delay, DPO Christian Bernieri writes clearly in this regard:
The first days are the most critical: scams are most effective. Waiting to inform means harming people
Undoubtedly, InfoCert will have to provide full information about the incident to both the Garante per la Protezione dei Dati Personali and the ACN, and the nature of the problem and the relative responsibilities to be attributed to those involved will be known in those fora.
Bernieri ends his message on Bluesky with the phrase ‘as usual: opacity and mystification’: what one really finds hard to digest (we are not just talking about InfoCert in this case) is not only the delay but the constant attempt to deregulate the incident. It is a clumsy attempt and it is surprising that the companies do not understand this: when you derubricate the incident you mystify reality by telling a false or only partially true fact. This is counterproductive. Among other things, the misrepresented communication becomes the subject of sanctions in the event of an inspection because that lack of transparency of which Bernieri speaks is not optional but is owed to customers and required by law. The Banca Sella case, the Postel case, were examples of incorrect communication with customers and are only among the most recent.
Conclusions
To put it mildly, Italy is not sailing in good waters from the point of view of IT security. There continues to be a poor culture of even the most basic information protection measures, not to mention more high-profile incidents and issues. One could cite the case of the Intesa San Paolo bank, whose official application hid the audio file of a burp (and more) without anyone noticing (how is testing done?). We could talk about the aforementioned Piracy Shield platform, which is considered problematic, if not blocking (for more on this, read Wired’s articles by clicking here and clicking here). All this also has a political dimension, both on a national and international scale (it is worth mentioning NIS 2), so it is difficult to draw concise conclusions, but perhaps we can rely on a wonderful phrase by Ennio Flaiano that evidently also applies to cybersecurity:
The political situation in Italy is serious.

