The company INPS Servizi S.p.A. was the subject of a data breach by the LYNX collective, with data exfiltration and interruption of services. Let’s find out more.
A lot of information is still to be verified: there is no certainty that it was the Lynx collective, the portal of INPS Servizi S.p.A. is still not working, there are some points to be clarified, but in the meantime we try to make some reflections.
What happened
It would appear that on 18 November 2024, the Lynx collective attacked and exfiltrated the data of the company INPS Servizi S.p.A., causing, among other things, the unavailability of the data in the infrastructure.
About INPS Servizi S.p.A.
On LinkedIn we read that
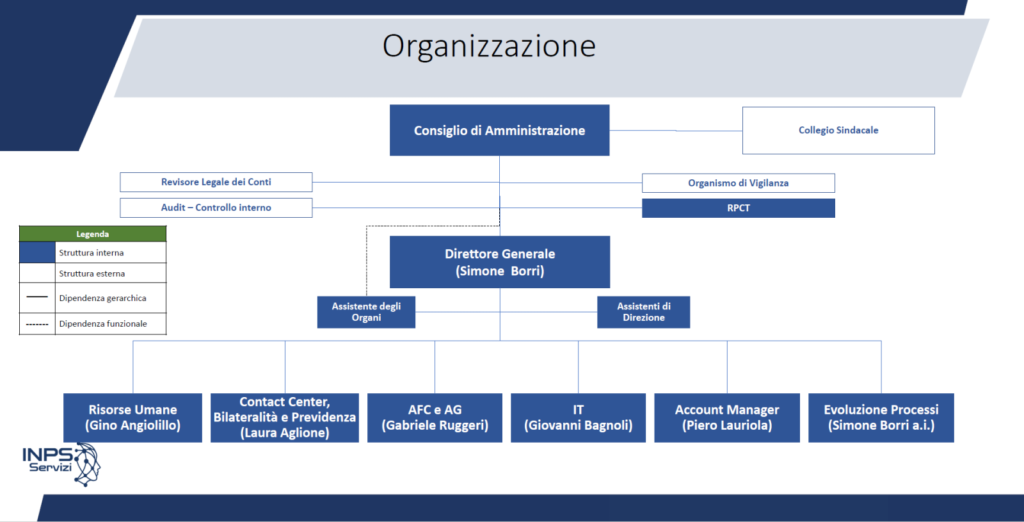
INPS Servizi SpA is an in-house providing joint-stock company wholly owned by INPS, established on 11 June 2021. INPS Servizi manages the Multichannel Contact Centre service for the Institute’s users. It provides administrative and accounting services to public and private social security and welfare institutions and funds, and to bilateral bodies, as well as services related to INPS’s institutional tasks.
With regard to the IT infrastructure disruptions, it should be noted that on 20 November 2024 at 14:20, the company’s official portal(https://www.inpsservizi.it/) was not reachable. However, it was possible to obtain a more extensive description of INPS Servizi S.p.A. from an old version of the portal thanks to the Way Back Machine.
NPS Servizi S.p.a. is an in-house providing joint-stock company wholly owned by INPS, which came into existence on 11 June 2021 following the amendment of the name, corporate purpose and bylaws of Italia Previdenza SISPI S.p.a.. These amendments were arranged on the basis of the provisions contained in Article 5bis of Decree-Law 101/2019, converted with amendments by Law 128/2019, which provided for the entrusting to INPS Servizi S.p.a. of the multi-channel contact centre (CCM) activities towards the Social Security Institute’s users and the continuation of the activities that already constituted the corporate purpose of Italia Previdenza SISPI S.p.a, which had been set up in 2001, with the task of providing administrative/accounting products/services, in particular for the collection of contributions and the payment of benefits for complementary and supplementary pension funds, and research and advisory services for the market in the area of social security and assistance in general. Until the date of its transformation into INPS Servizi S.p.a., the company was involved in the following activities and services, which will continue to be performed in conjunction with the multi-channel contact centre service:
- activities aimed at settling, in favour of Poste Spa employees, the severance indemnities accrued up to 28 February 1998, the date of transformation of Ente Poste into a joint-stock company, which are materially disbursed by the Gestione Commissariale Fondo Buonuscita for Poste Italiane S.p.a. employees;
- Provision of the data contained in F24 and Uniemens flows, together with other administrative services, required by the bilateral bodies for the acquisition of contributions and for other institutional purposes provided for by collective bargaining in favour of workers employed by companies applying the collective bargaining agreements;
As stipulated in its statutes, INPS Servizi can provide administrative accounting services to public and private social security and welfare institutions and funds. Until 2020, the company also handled the following activities:
- Administrative service in favour of FONDINPS, a residual supplementary pension fund set up at INPS under Legislative Decree No 252\2005 and intended for employees of companies without a contractual fund and who have not made explicit the destination of their TFR. In accordance with the law, since 2020 the Fund has been placed in liquidation and the positions of its members have been transferred to the COMETA Pension Fund, which now manages the residual complementary pension form in place of FONDINPS.
- Horizontal Secretariat and Component activities, within the European Cooperation Project called “EU-China – Social Protection Reform Project SPRP”, which from 2016 to 2019 had the task of providing the Chinese government authorities with expert support for the revision of the social protection system.
History of events
- 18/11/2024-Presumed date of infection of INPS Servizi S.p.A.
- 19/11/2024-INPS Servizi S.p.A. communicated the data breach to suppliers (e.g. QuAS)
- 22/11/2025-INPS Servizi S.p.A. activates temporary portal
Lynx ransomware: historical traits and spread
About the Lynx collective, however, a few things are known thanks to the Ransomfeed project: the collective was the author of 49 attacks in 2024, but never against Italy. The countries affected so far included Australia, Canada, Costa Rica, Guatemala, Luxembourg, the Netherlands, the Republic of Cape Verde, Singapore, Spain, Great Britain and the United States of America. Now Lynx can also include Italy in its list.
From the PaloAlto researchers, however, we learn something different:
In July 2024, researchers at Palo Alto Networks discovered a successor to the INC ransomware called Lynx. Since its emergence, the group behind this ransomware has actively targeted organisations in various sectors such as retail, real estate, architecture, and financial and environmental services in the US and UK. Lynx ransomware shares a significant part of its source code with INC ransomware. The INC ransomware initially emerged in August 2023 and had variants compatible with both Windows and Linux. Although we have not yet confirmed any Linux samples for Lynx ransomware, we have noticed Windows samples. This ransomware operates using a ransomware-as-a-service (RaaS) model.
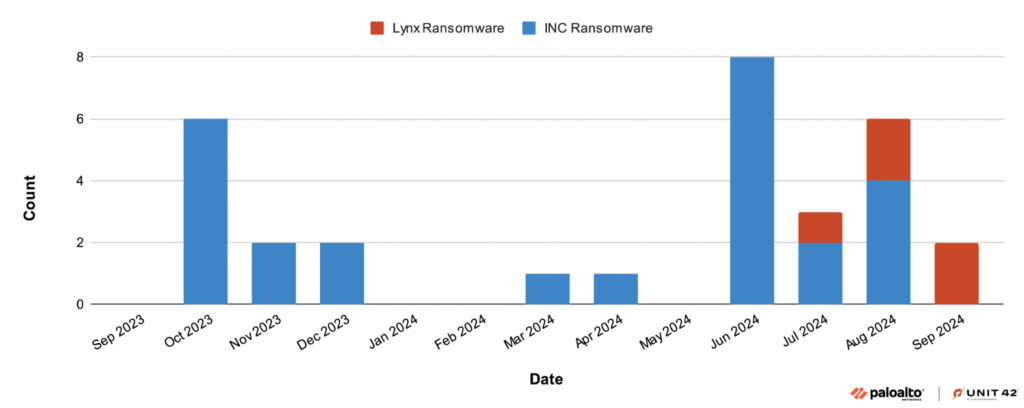
Lynx’s activity has been tracked by PaloAlto over time and encapsulated in a graph below.
The group’s official portal clearly states the motivations of the Lynx group.
Lynx Ransomware’s core motivation is grounded in financial incentives, with a clear intention to avoid undue harm to organisations. We recognise the importance of ethical considerations in the pursuit of financial gain and maintain a strict policy against targeting governmental institutions, hospitals, or non-profit organisations, as these sectors play vital roles in society. Our operational model encourages dialogue and resolution rather than chaos and destruction. We believe that fostering an environment where businesses can engage in constructive problem-solving can lead to better outcomes for all parties involved. This perspective allows us to engage with organisations in a manner that emphasises negotiation and mutual understanding, generating economic activity while minimising disruption to the essential functions of society. In pursuing these goals, our commitment is to uphold professional standards that prioritise transparency in communication and targeted interactions, thus reinforcing a framework where commerce and cybersecurity can coexist without spilling into unnecessary conflict or harm.
The main motivation for Lynx ransomware is based on financial incentives, with a clear intention to avoid unnecessary damage to organisations. We recognise the importance of ethical considerations in the pursuit of financial gain and maintain a strict policy that excludes the targeting of government institutions, hospitals or non-profit organisations, as these sectors play vital roles in society. Our operating model encourages dialogue and resolution rather than chaos and destruction. We believe that fostering an environment where companies can address problems constructively can lead to better outcomes for all parties involved. This perspective allows us to interact with organisations by emphasising negotiation and mutual understanding, generating economic activity and minimising disruption to the essential functions of society. In pursuit of these goals, our commitment is to maintain professional standards that prioritise transparency in communication and targeted interactions, thereby reinforcing a framework in which commerce and cybersecurity can coexist without resulting in unnecessary conflict or damage.
Lynx ransomware: the manifesto
A short message is available on the official Lynx blog that should summarise the ‘principles’ on offensives.
Lynx Ransomware’s core motivation is grounded in financial incentives, with a clear intention to avoid undue harm to organisations. We recognise the importance of ethical considerations in the pursuit of financial gain and maintain a strict policy against targeting governmental institutions, hospitals, or non-profit organisations, as these sectors play vital roles in society. Our operational model encourages dialogue and resolution rather than chaos and destruction. We believe that fostering an environment where businesses can engage in constructive problem-solving can lead to better outcomes for all parties involved. This perspective allows us to engage with organisations in a manner that emphasises negotiation and mutual understanding, generating economic activity while minimising disruption to the essential functions of society. In pursuing these goals, our commitment is to uphold professional standards that prioritise transparency in communication and targeted interactions, thus reinforcing a framework where commerce and cybersecurity can coexist without spilling into unnecessary conflict or harm.
The main motivation for Lynx ransomware is based on financial incentives, with the clear intention of avoiding excessive damage to organisations. We recognise the importance of ethical considerations in the pursuit of financial gain and maintain a strict policy against targeting government institutions, hospitals or non-profit organisations, as these sectors play vital roles in society. Our operating model encourages dialogue and resolution rather than chaos and destruction. We believe that fostering an environment where companies can address problems constructively can lead to better outcomes for all parties involved. This perspective allows us to interact with organisations in a way that emphasises negotiation and mutual understanding, generating economic activity and minimising disruption to essential societal functions. In pursuit of these goals, our commitment is to maintain professional standards that emphasise transparent communication and purposeful interactions, thus reinforcing a framework in which commerce and cybersecurity can coexist without degenerating into unnecessary conflict or damage.
Lynx ransomware: the blog
Lynx’s blog can currently be found at http://lynxblog.net/leaks and points to the address: 88.151.117.237:
inetnum: 88.151.117.0 - 88.151.117.254
netname: RU-DLINE-20220513
country: RU
org: ORG-DLM6-RIPE
admin-c: DLM62-RIPE
tech-c: DLM62-RIPE
status: ASSIGNED PA
mnt-by: IP-RIPE
created: 2022-05-12T23:16:20Z
last-modified: 2022-05-12T23:16:23Z
source: RIPE
organisation: ORG-DLM6-RIPE
org-name: Goroshko Evgeniy Andreevich
country: RU
org-type: OTHER
address: mkr. Rostoshi, ul. Sadovoe Koltso, d. 116
address: 460008 Orenburg
address: Russia
abuse-c: DLM62-RIPE
mnt-ref: IP-RIPE
mnt-by: IP-RIPE
created: 2020-11-01T11:16:28Z
last-modified: 2024-04-23T10:52:04Z
source: RIPE # Filtered
role: DLine Media
address: mkr. Rostoshi, ul. Sadovoe Koltso, d. 116
address: 460008 Orenburg
address: Russia
abuse-mailbox: info@dline-media.com
phone: +7 985 6640514
nic-hdl: DLM62-RIPE
mnt-by: IP-RIPE
created: 2020-11-01T11:15:36Z
last-modified: 2020-11-01T11:15:36Z
source: RIPE # Filtered
We are therefore talking about Russian-hosted hosting.
Lynx ransomware: some technical information
The activity carried out by Lynx ransomware is known as a variant of the previous INC Ransomware, about which PaloAlto Network states:
The Lynx ransomware samples we analysed used AES-128 encryption algorithms in CTR mode and Curve25519 Woman. All files are encrypted and have the extension .lynx added. This version of the malware is designed for the Windows platform and is written in the C++ programming language.
Regarding the type of encryption used, we learn from Google Code that:
curve25519 is an elliptic curve, developed by Dan Bernstein , for a fast Diffie-Hellman key agreement. The original implementation of DJB was written in a language of his own devising called qhasm . The original source code of qhasm is not available, only the 32-bit x86 assembly output. Since many x86 systems are now 64-bit and portability is important, this project provides alternative implementations for other platforms.
The Blackpointcyber portal reports that the ransomware encrypts 1 MB of every 6 MB of the file; files smaller than 1 MB are fully encrypted. This differs from INC Ransom in that INC Ransom also offers a ‘fast’ and a ‘slow’ encryption mode. Furthermore, we learn that both Lynx and INC Ransom use the DeviceIoControl function to control devices and delete backup copies. In the Lynx ransomware variant, the DeviceIoControl function only works when both the ‘-file’ and ‘-dir’ arguments are not used.
DeviceIoControl is a function of the Windows API that allows applications to communicate directly with device drivers. It is designed to send specific commands or control requests to hardware devices, file systems or drivers, allowing detailed control at the operating system level. The main areas of application include:
- Device management: control of specific hardware (such as hard disks, USB devices, or virtual devices).
- Advanced file system access: operations requiring elevated privileges, such as queries on volumes or partitions.
- Driver development: testing and debugging of customised drivers.
Since DeviceIoControl allows privileged access, it can be misused for malicious purposes, such as bypassing system protections. It is therefore essential to carefully manage permissions and verify calls. For more information, please refer to Microsoft’s official documentation.
We also learn from the Blackpoint portal that in May 2024, INC Ransom operators offered their source code for sale on a dark web forum for USD 300,000. BlackBerry researchers reported that Lynx and INC Ransom used the same email address, gansbronz{at}gmail{.}com, within specialised web portals.
In an interview with RedHotCyber, the collective behind the Lynx ransonware explained that:
The group describes its activities as exclusively ‘financially motivated’ and a policy that does not allow attacks against critical, government and healthcare facilities
Data information
INPS Servizi S.p.A. is a remarkable reality: it has more than 2,800 professionals spread over 5 Directorates and 12 operational sites: Bari, Catania, Cosenza, Crotone, Ivrea, L’Aquila, Lecce, Milan, Naples, Olbia, Rome and Terni. The amount of data stolen is therefore potentially considerable.
INPS Servizi S.p.A.’s maintenance of the data, had to meet the minimum security requirements of AgID Circular 2/2017, as well as Legislative Decree 138/2024 (the transposition of the NIS 2 Directive). It appears from the Health Insurance Fund for Managers, for which INPS Servizi S.p.A. was the supplier, that the data concerning them was aggregated.
We would like to point out that the data that Inps Servizi manages for QuAS only relate to the total contributions paid by each company, without any details concerning individual members.
This reduces the impact of the data breach as far as QuAS is concerned, but the other exfiltrated information remains, which, given the extent of INPS Servizi S.p.A., may not be small.
Updates on events
22/11/2024-22:32-The INPS Services portal is back online
The INPS servizi S.p.A. portal went back online at around 22:32 on 26 November 2024.
22/11/2024-20:25-The temporary portal of INPS Servizi is online
At around 20:25 on 22/11/2024, the temporary portal of INPS Servizi S.p.A. came back online with a message confirming that a cyber attack had taken place and that recovery actions were in progress.
InpsServizi S.P.A. suffered an IT attack that rendered temporarily unavailable the functions of the Institutional Portal and some management applications. Ongoing actions are focused on restoring the compromised infrastructure in a timely and secure manner.
At about 9.40 p.m. the work was in progress, the screen below shows an error which is probably only the temporary result of the restoration work.
The full message on the page is:
Fastly error: unknown domain: inpsservizi.it. Please check that this domain has been added to a service.
Details: cache-fco2270028-FCO (151.101.131.10)
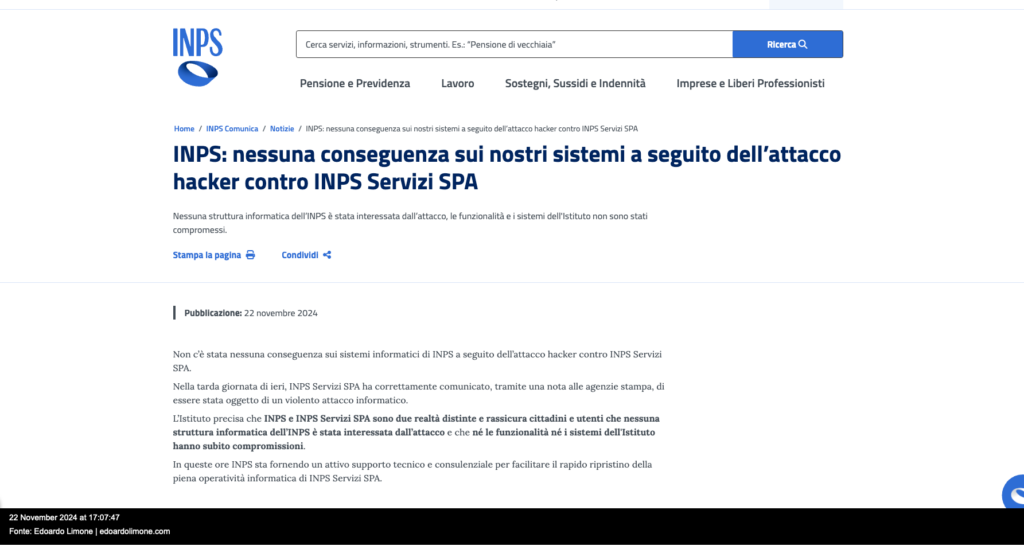
22/11/2024-17:00-INPS publishes a news item on the incident
Finally, a news item appears on the INPS portal (after about 4 days since the incident) about what happened to the company INPS Servizi S.p.A.. The full text states the following:
INPS: no consequences on our systems following the hacker attack against INPS Servizi SPA
There were no consequences on INPS’s IT systems following the hacker attack against INPS Servizi SPA. Late yesterday, INPS Servizi SPA correctly communicated, through a note to press agencies, that it had been subject to a violent computer attack. The Institute clarifies that INPS and INPS Servizi SPA are two separate entities, and reassures citizens and users that no INPS IT structure has been affected by the attack, and that neither the Institute’s functions nor systems have been compromised. INPS is currently providing active technical and consulting support to facilitate the rapid restoration of INPS Servizi SPA’s full IT operations.
21/11/2024-09:00-Repubblica publishes the news
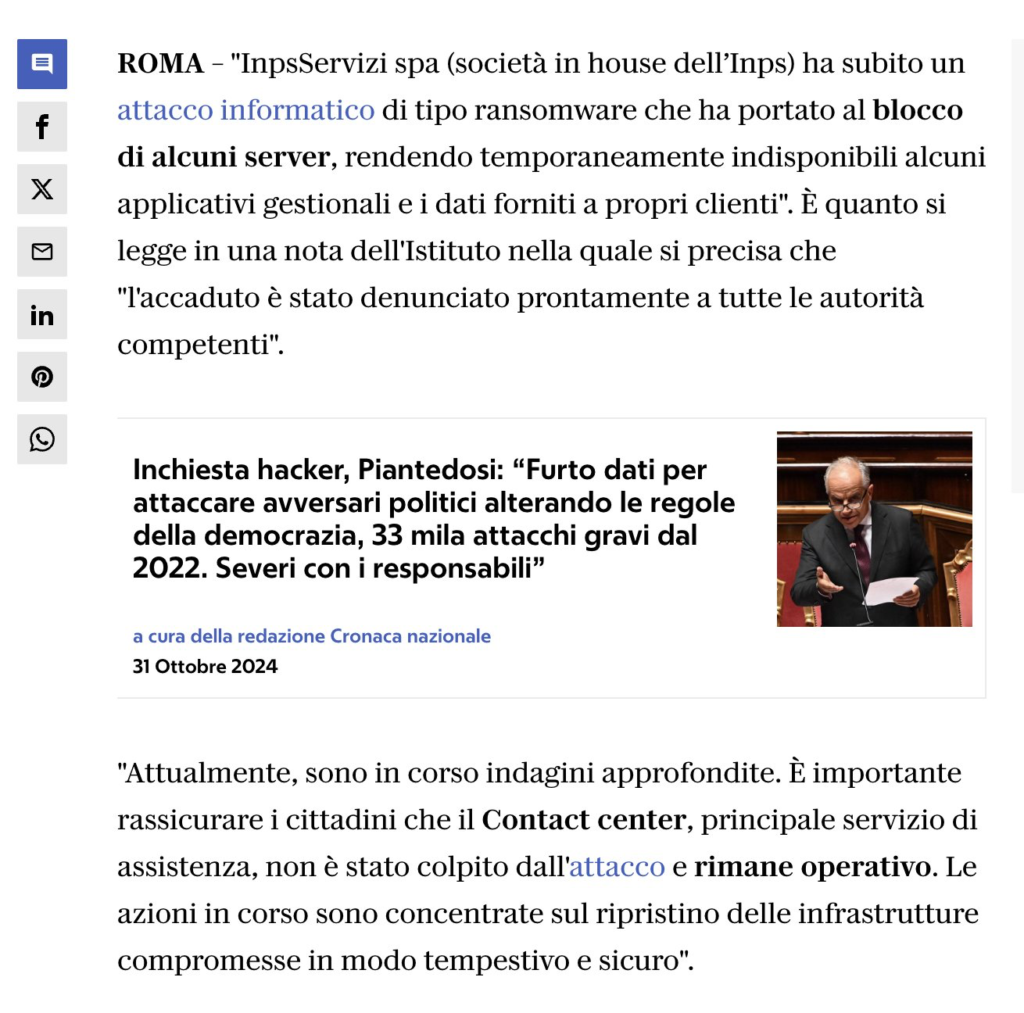
As of 09:00, there has still been no official claim of the attack against INPS Servizi S.p.A., but the news has now spread and Repubblica, on 21 November 2024 at 23:31, published a short article on the case.
ROME – “InpsServizi spa (an in-house company of the Inps) has suffered a ransomware attack that led to the blocking of some servers, making some management applications and data supplied to its customers temporarily unavailable”. This is what is stated in a note from the institute in which it is specified that ‘the incident was promptly reported to all the competent authorities’.
In the meantime (12:40 p.m.) on the official INPS website there is no news in the ‘News’ section and the INPS Servizi S.p.A. portal continues to be unreachable.
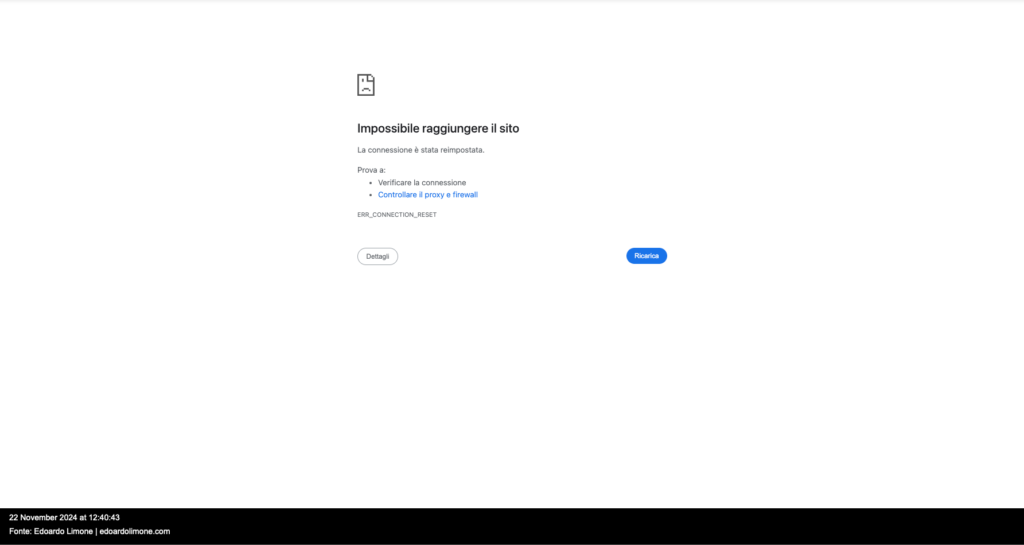
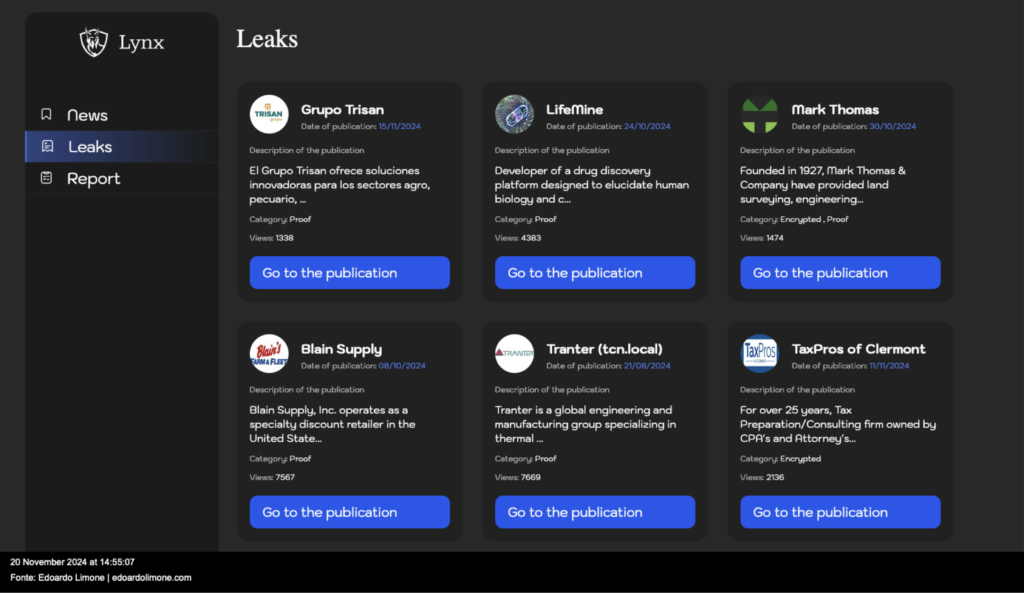
20/11/2024-14:00-no official claim yet from Lynx
At approximately 14:00 hours on 20 November 2024, Lynx had not yet published any data on INPS Servizi S.p.A., the image clearly shows this.
19/11/2024-Confirmation of data breach by QuAS
Despite the fact that no official news appears either on the INPS website or on the official portal of INPS Servizi S.p.A. (which, indeed, is not even online), a statement was published by a customer of INPS Servizi S.p.A. that confirms and circumscribes what happened.
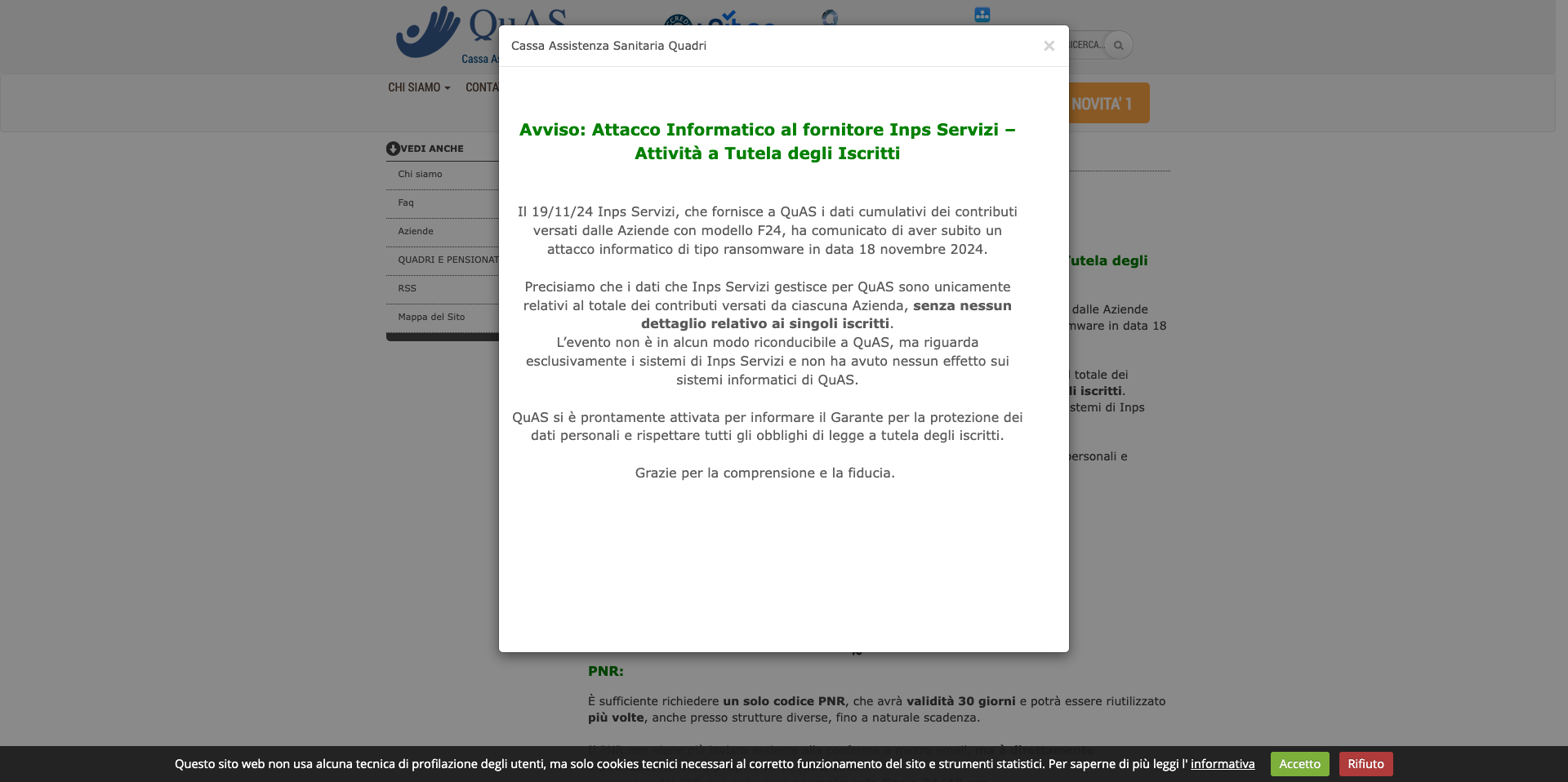
The news, in fact, was published on the QuAS portal (Cassa Assistenza Sanitaria Quadri) of which INPS Servizi S.p.A. is a supplier. The official press release reported by Ransomfeed states the following.
Warning: Computer attack on the Inps Services provider – Activities to protect members
On 19/11/24 INPS Servizi, which provides QuAS with the cumulative data on contributions paid by companies using the F24 form, announced that it had suffered a ransomware attack on 18 November 2024. We would like to clarify that the data that Inps Servizi manages for QuAS only relate to the total contributions paid by each company, without any details relating to individual members.
The event is in no way attributable to QuAS, but only affected the systems of Inps Servizi and had no effect on the IT systems of QuAS. QuAS took prompt action to inform the Garante per la protezione dei dati personali and to comply with all legal obligations to protect members. Thank you for your understanding and trust.