In Italy, there is a major problem in restoring health services following a computer incident, and it matters little whether the incident is caused by negligence or malicious intent. In the health sector, this can make the difference between the provision of essential services and their non-delivery to the detriment of patients.
Digital health
The term digital health encompasses all the information systems deputed to the operation of healthcare services: think of document management systems, server systems for holding files, communication and data transmission services, patient management systems, and so on. Digital health is a delicate web of systems, services, networks, infrastructures that animate hospitals, ASLs, emergency rooms, etc.
The occurrence of an IT incident in a sensitive context such as healthcare must be seen as critical. The closure of an emergency room, for instance, is equivalent to the interruption of care provision and the transfer of patients to different and sometimes more distant facilities. It is worth remembering that phenomena of this kind, in Germany, contributed to the death of a woman, and that any attempt to dismiss the phenomenon is tantamount to demonstrating one’s ignorance of the subject of computer security and disregard for the treatment of patients.
In Italy, the situation regarding the restoration of healthcare services is taking on truly worrying contours: as of 12 July 2024, the ranking shown in the graph below can be deduced, a ranking that sees ASST Rhodense rising rapidly to the top. It has been mentioned on many occasions on this portal that the maximum return to operation time (RTO) of ASLs, for example, should be 4 days (3.7 to be exact).
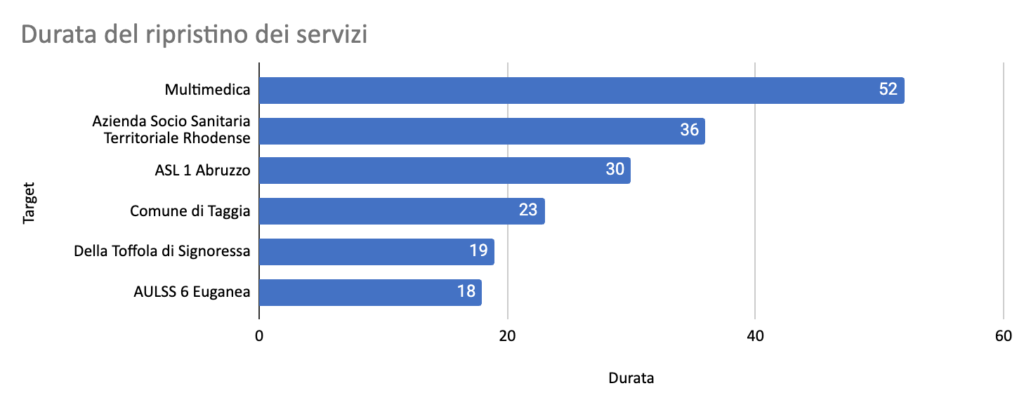
It is therefore embarrassing, to say the least, if not worrying, to see that over the years (more than 10 since AgID’s survey), the situation has not only not improved but, if possible, worsened. Bear in mind, for instance, that the data in the graph refer to the years indicated in the table:
| Year | Target | Duration |
|---|---|---|
| 2021 | AULSS 6 Euganea | 18 |
| 2023 | ASL 1 Abruzzo | 30 |
| 2023 | Multimedica | 52 |
| 2024 | ASST Rhodense | 36⇪ |
It should also be noted that the data presented here take into account only those targets that have had a restoration period of more than 10 days (and not 4 as reported in the AgID document). The arrow next to ASST Rhodense means that the health authority, at the time of writing this article, is busy restoring its digital services, including the official web portal, which is presented in its temporary guise as shown below. It will certainly not escape the reader’s notice that the further one goes, the more the days of restoration increase instead of decreasing. The more technological progress increases, the more the possibility of restoring services on time decreases.
The culture of ignorance
The first publication of the GDPR dates back to 27 April 2016, 8 years have now passed and still many healthcare facilities continue to handle and hold personal health data improperly. Precisely those data that we remember are special category personal data and for that reason would need greater security measures because they are more sensitive:“Special categories of personal data that deserve greater protection should only be processed for health-related purposes…” (GDPR-Consideration 53). Clearly this is not only a problem for healthcare facilities, but in this article we will focus on this area because it is considered the most important. It is astonishing how carelessly the law is violated, starting with the much-discussed GDPR that prescribes:
It is in the legitimate interest of the data controller concerned to process personal traffic data to the extent strictly necessary and proportionate to ensure network and information security, i.e. the ability of a network or an information system to resist, at a given level of security, unforeseen events or unlawful or malicious acts that compromise the protection of personal data the availability, authenticity, integrity and confidentiality of personal data stored or transmitted...
Given the results, one would argue that such a legitimate interest does not really exist and that data controllers do not care about this interest but do something else. This is because what is lacking in digital health is not only technology, but above all strategies, documentation, planning, and all that is needed to design an adequate, though clearly not infallible, information ecosystem over time.
It could be clarified to many managers of facilities affected by data breaches that the return to operations expressed by the RTO (Recovery Time Objective) service level refers to the complete restoration of all the organisation’s services, and not only of a part, the one that is obviously considered most relevant. No, the recovery must be total, from the first to the last element compromised during the incident: otherwise the recovery, logically, cannot be considered complete and is partial. Yet much controversy has been raised on this point: a restoration is considered complete if, for example, it does not include the reactivation of a website, or of a portal for booking healthcare services, which, prior to the computer incident, was present and fully functional.
There is also another problem to be analysed: regulatory ignorance. In the last few hours, discussions are taking place on Twitter about a data breach involving Prof. Burioni and the signatories of a complaint against him. It is a much-discussed controversy and was discussed by DPO Christian Bernieri in this article. The discussion was in itself very interesting, not so much because of the central fact, but because there was evidence on Twitter that many people, even insiders, still do not understand what a data breach is. The following is a shining example of ignorance on the subject in question.
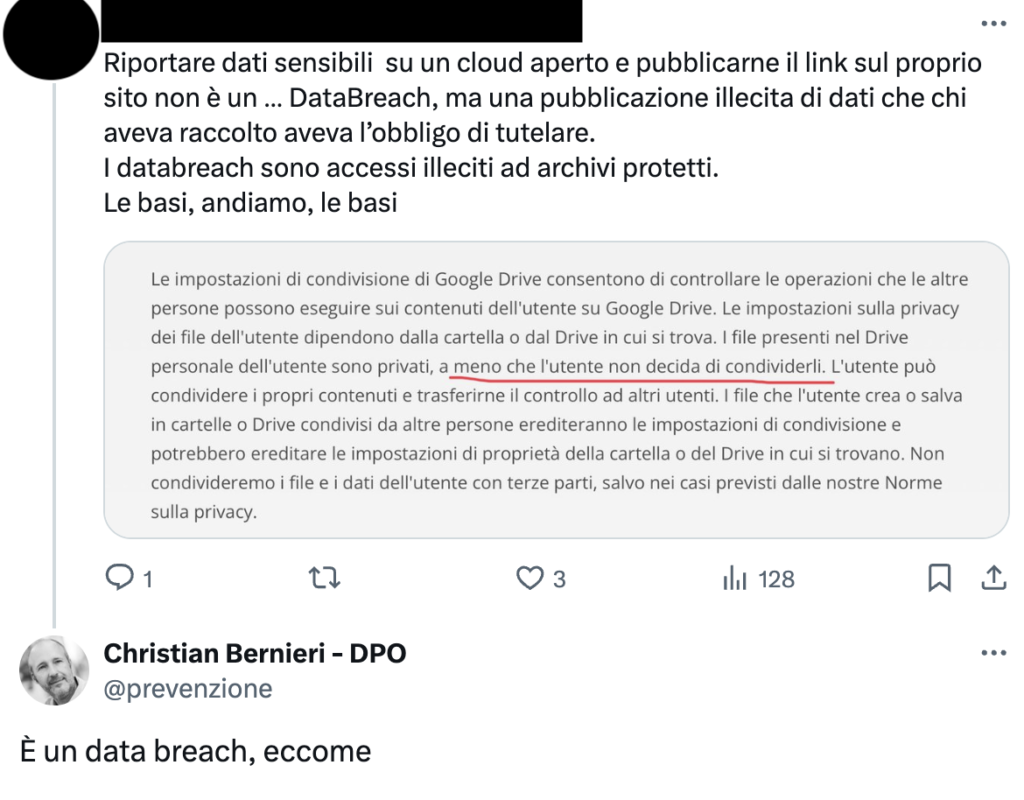
The censured user, who, by the way, is not a jurist or an insider, claims that what happened in the Burioni case is not a data breach. However, the user ignores the fact that the complaint was signed by individuals who only gave their consent for the document to be signed and not for their personal data to be disclosed on the internet. The user also ignores the fact that a piece of data, even if public, must be processed according to the specific and intended purposes of processing, and in the present case the dissemination of personal data and photocopies of identity documents is neither intended nor authorised. The problem, however, is not so much in the answers given by non-practitioners; it explodes when it is self-styled insiders who give these answers. Eight years have passed, and lawyers, computer technicians, and so-called ‘experts’ have still not understood what a security breach is and what the law prescribes in this regard. This is a problem and it is caused by the lack of proper training and the complete sloppiness with which some topics that should actually be very important are often treated.
One would think, therefore, that in recent years a culture of ignorance has been cultivated based on approximation, on waffling, on the downplaying of phenomena that are much bigger and more relevant than they appear on social media, with the consequent increase in the time it takes to restore digital services. And yet it is strange: in addition to GDPR, there are standards such as ISO 27001, ISO 27005, Critical Security Controls that establish the need to govern recovery activities, and in a few months’ time (from 17 October 2024) there will also be NIS2 to insist on this. It almost makes one smile bitterly to see this regulatory turnover on so many important and regularly disregarded points.
Artificial intelligence could not miss
In this absolutely discouraging scenario, which shows all the ignorance on a subject that is as basic as it is fundamental for the rights of the individual, there is much talk of artificial intelligence applied to various fields, including healthcare. One would be forgiven for thinking that in order to apply even the slightest algorithm, the most elementary and harmless one, technical, organisational and methodological prerequisites are required, which are constantly ignored today.
It should be noted that the director of one of the ASLs listed above was outraged, because after the security breach, the newspapers were talking about the inefficiencies and the deficient state in which the computer systems were found, while lawyers (rightly) filed claims for compensation for their clients. In essence, instead of apologising and working promptly to restore services, the director of this health facility complained to journalists who were doing their job and denouncing the absurd conditions of data management and processing. In such a scenario, of absolute technical and organisational incapacity (more or less intentional), one would like to drop one of the most complex, articulated and therefore difficult-to-manage technologies in the world. A technology that could improve the lives of a great many people provided, however, that it is properly introduced into healthcare facilities and does not itself become an object or cause of vulnerability. Faced with such a topic, therefore, all that remains is a bitter smile and a slight shudder of fear that even this aspect could be rendered superficial in its implementation; the damage would be considerable, to say the least.
There is no simple solution but…
A thought has to be made: in a private company, if a project manager commits blatant and repeated errors that cause severe damage to the organisation and its customers in the event of an accident, you can be sure that that manager will at least be relieved of his or her duties.
After the security breaches and exposure of data by hackers, macroscopic errors were revealed in the management and holding of data by many healthcare facilities. These errors were the result of an IT strategy aimed at ‘convenience’ and not at security, or at least recklessness or negligence. If the manager(s) responsible for these choices were to be held accountable, there would undoubtedly be more attention: especially if he/she had to answer not only before the law but also by paying any fines. This is important to understand and is the fundamental difference between the public and the private sphere. In a private context, the liable party is jointly and severally liable for the damage caused to the organisation and its customers. In the public context, we are at an embarrassing level, where technicians who have facilitated data breaches have not only not even suffered disciplinary action but in some cases have even been ‘promoted’ to different tasks with a corresponding increase in salary.
Data breaches show years of neglect, of violation of regulations (such as AgID Circular 2/2017), and if a data breach happens, for example, after ten years of neglect, the question is no longer about the IT incident but about why for ten years the regulations were not complied with. It is possible to determine the condition of a computer system very precisely, to establish its limits and fundamental breaches without any problems whatsoever. For instance, it is possible to determine whether, at the time of the incident, the organisation was taking the security measures required by law, whether they were in possession of properly implemented backups, whether they had properly digitally signed plans and strategies. In short, if one wanted to, it would be possible to make all the necessary findings to enforce the law and restore dignity to the processing of citizens’ data.
Conclusion
It should all be very important but, as the comedian Luca Bizzarri would say, we are in Italy and we like to do things our own way. So we wait for months and months for the health services to be fully operational again, and in the meantime top experts in technology, law, cybersecurity, artificial intelligence, come and go in round tables and webinars and online meetings denouncing their great preparation. With all this widespread knowledge, Italy should be at the top in terms of technological performance, cybersecurity and personal data processing culture. Strangely enough, this is not the case, but it is holiday time and so everything will be conveniently forgotten under a beach umbrella between a spritz and a Settimana Enigmistica. Hackers, security breaches, data protection will be forgotten, and the dignity of the citizen’s rights will also be forgotten, but who cares, tomorrow is another day and the dignity of the citizen’s rights we have long since forgotten.

