Control 14 of CSCs is based on ‘Security Awareness and Competence Training’, an undoubtedly important but also surprising topic to find within documents of this type. Let us delve into its contents.
Control #14: Training and Security Skills
It is extremely interesting to see security control based on the training and competence of users. All too often, training is relegated to a marginal role when, in reality, it enables accidents to be prevented and problems to be dealt with almost as effectively as technical tools. Sometimes, in fact, the ‘human component’ even succeeds in making up for technical deficiencies by achieving extraordinary results; the CSCs make this concept very clear.
Users themselves, more or less intentionally, can cause incidents by not handling sensitive data properly, by sending an e-mail with sensitive data to the wrong recipient, by taking away a portable device, by using weak passwords or by using the same password they use on public sites. No security programme can effectively tackle cyber risk without addressing this fundamental human vulnerability. Business users at every level have different risks: for example, executives handle more sensitive data, system administrators have the ability to control access to systems and applications, and users in finance, human resources and contracts all have access to different types of confidential information that can make them targets.
Control 14 therefore makes more than valid arguments and proposes nine safeguards, essentially all of which are of interest to organisations.
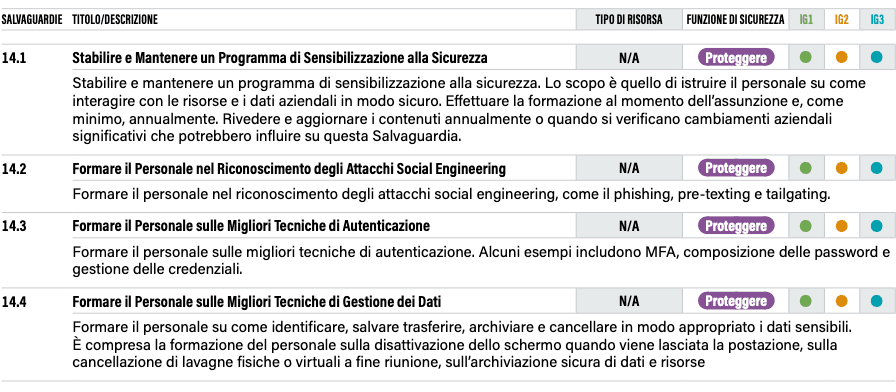
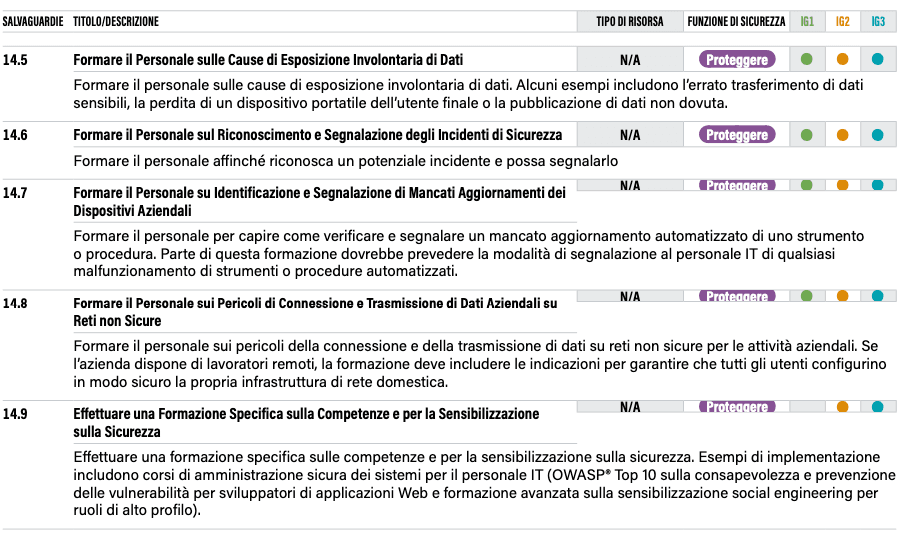
Training and Security Awareness programmes
The above-mentioned safeguards can be particularly useful in designing training courses for staff, which, as can be seen, cover topics of absolute topicality and complexity. Consider safeguard 14.2, i.e. training on Social Engineering. These are attacks that are growing in number and complexity and about which little is known: this is demonstrated by the attacks on Twitter in 2020, on the MGM casinos in Las Vegas, but also by the more recent ones that occurred in Italy to the detriment of some current account holders of major banking institutions. Training on techniques of this kind is also essential because, as is well known, there is no software that, once installed, is able to guarantee total protection against such dynamics. Raising awareness of computer security issues is part of the accountability paradigm. Point 14.9 ‘Carry out Specific Skills and Security Awareness Training’ is absolutely important and comes at the end of a series of safeguards that have revolved around concepts such as securing networks, managing corporate devices, reporting security incidents, and unintentional data exposure. In this sense, it is interesting to note how the ASCs manage to take into account incidents of both ‘malicious’ and ‘negligent’ nature and thus manage to promote comprehensive safeguards with useful indications. Reinforcing these concepts is precisely what the ASCs write:
An effective security awareness training programme should not be reduced to an annual pre-packaged training video, coupled with regular phishing tests. Although annual training is necessary, up-to-date security information and notifications should also be provided frequently.
Conclusions
The training part of the CSCs is interesting: it has a more methodological than technical approach and is more focused on the design of genuinely interesting content than on the application of sterile and unhelpful training paths. Of particular note is the component on reporting incidents, which does not only refer to the authorities, but is aimed above all at external and internal users of the company in order to avoid reputational damage and an increase in the complexity of incident management.

