CSCs pay special attention to data recovery. Let us address this topic and analyse it in the light of current risks.
Control #11: Data Recovery
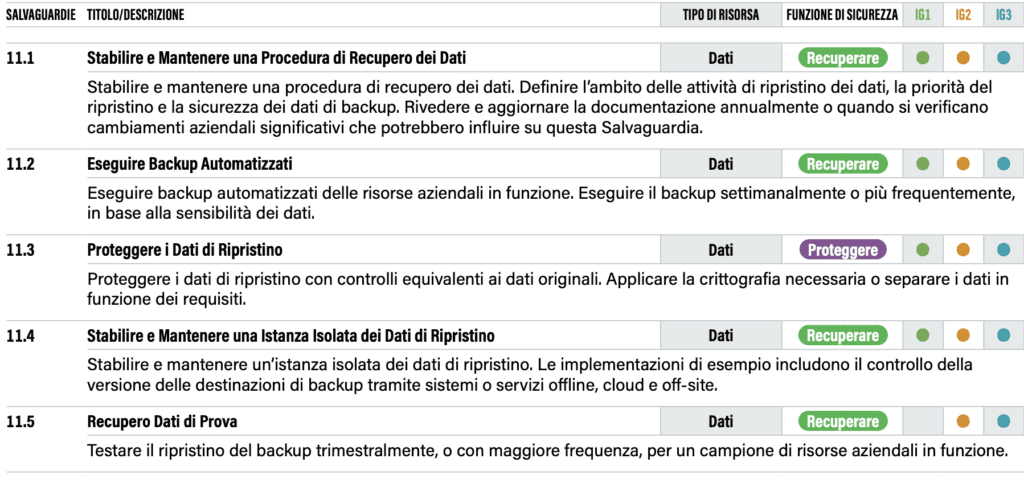
Every company, public or private, will have asked itself the question of how to deal with the loss of control and possession over its data. Once the organisation no longer has the information, how can it regain possession of it? How can it recover it? The question is not trivial because there is no one-size-fits-all solution: files are recovered differently from databases, small companies have different recovery capacities from large companies, with very different limitations and possibilities for success. It is therefore necessary to structure and understand this well, and the first thing to do is to note that the CSCs establish 5 fundamental security controls. Smaller companies should observe at least 4 of these 5 controls, which makes it clear how important they are. The safeguards that the ASC 8 provide are as follows.
Understanding backup and recovery
The first aspect of in-depth study concerns the ‘true’ understanding of the backup policy: all too often backups are copies of data made over time with few ‘pre’ and ‘post’ verifications. A backup, before being created, must be ‘reasoned’: it must be understood, depending on the type of file to be backed up, which backup mechanism to set up and which verification cycles to foresee. For example: an incremental backup, how often should it be consolidated? Have the appropriate files and folders been selected for that type of backup? This also varies depending on the restoration to be performed. It is therefore no coincidence that Safeguard 11.1 requires‘reviewing and updating documentation annually or when significant business changes occur‘.
Backup protection from oneself and others
Those who really know the world revolving around backups are well aware that the problems do not only come from outside. Certainly one must make sure that the backup copy, if stolen, is unreadable (rule 11.3) but one should also prevent illicit acquisition and thus provide for what is stipulated in safeguard 11.4 “Establish and Maintain an Isolated Room for Restore Data“. Those familiar with AgID’s Circular 2/2017 will have noticed many similarities, the most obvious being the one on offline management of backups.
| ABSC_ID | Level | Description |
|---|---|---|
| 3.3.1 | Minimum | Installation images must be stored offline. |
| 10.3.1 | Minimum | Ensuring the confidentiality of the information contained in the backup copies through adequate physical protection of the media or through encryption. Encryption prior to transmission allows the backup to be remoteised even in the cloud. |
The above are just some of the rules set out in Circular 2/2017, and it is possible to appreciate the level of technical detail that correctly differentiates between backups and installation images. Images, as technicians are well aware, aid recovery times and greatly facilitate the process of getting back up and running. The criterion behind the backup methodology is the observance of the ‘3…2…1…Backup!’ rule, already discussed at length in other articles.
Make at least three copies of the same file, on at least two different storage media, and keep at least one device offline.
The ‘3…2…1…Backup!’ policy is important, but deserves some clarification: the two different media should be technically different (e.g. a hard disk and a cloud space), to prevent a threat from targeting both. Hopefully, the choice of different technologies will render the malicious action of a potential malicious agent useless. A second point of attention is the concept of versioning, which is particularly relevant for shortening backup times, but above all for ensuring great flexibility in file recovery. Finally, it is good to focus on the word‘at least‘, understood as the minimum level required for the ‘3…2…1…Backup!’ policy to be effective.
Restoration and testing
The backup, in itself, does not prove that the data is secure. It is true that procedures such as the consistency check are performed when a backup is performed, in particular when it is finished, but these activities do not provide all the necessary certainty. The consistency check on a ‘backup package’ certifies that it has been created and closed correctly, certainly provides an assurance of readability, but does not provide any indication that the files are all present inside the package. It depends on how the backup was configured and over the months, as explained by the CSCs themselves, it is possible that the configuration has changed quite a bit (safeguard 11.1). It is essential, on a cyclical basis, to verify the content of backups but it is also necessary to attest to their outcome. There is no trace of a recovery test without a report and during inspections, claiming that backup checks are done without showing the reports is like expecting the inspector to work on trust. Each verification must therefore be accompanied by a concise report certifying the outcome and the main information. Incidentally, it is worth noting that standards such as ISO/IEC 27001:2022 provide for rules compatible with such safeguards: refer, specifically, to measure 8.13 contained in Annex 1 of the standard and reproduced in full below.
| ID | Title | Description |
|---|---|---|
| 8.13 | Information Backup | Backup copies of information, software, and systems shall be maintained and regularly tested in accordance with the agreed topic-specific policy on backup. Backup copies of information, software, and systems shall be maintained and regularly tested in accordance with the agreed topic-specific policy on backup. |
Conclusions
The establishment of the backup process is therefore not exclusively linked to the software that performs it, nor even to the automatic check performed at the end of the process. Back-up is a complex activity that must provide for different backup and recovery methods depending on the type of data handled. The periodic review is not only aimed at a formal check of the process and the data package, but also at understanding whether further optimisations can be made to both the saving and the recovery phase. The recovery time affects, for instance, the service levels that the organisation has contracted users to provide. Having adequate recovery times means having the peace of mind of not having to deal with legal as well as reputational consequences.

