It is since Obama’s presidential election that Americans have started to report an increase in hacker attacks against the US and private companies, but the last few years have made it obvious to everyone what was previously noticed by insiders. now it is a question of how to deal with the new frontier of hacking, what many call hybrid warfare.
We are not the centre of the world
It is believed that the West is the ‘master’ of technology and, consequently, of all forms related to it. Nothing could be more wrong. Read the following:

Cyber war and cybersecurity are perceived as Western notions, the Russian equivalent of which is infowar and information security.
Source: ‘Brigate Russe’, M. Ottaviani, Ledizioni 2022
The choice of terminology adopted by some countries, radically different from our own, has an effect on the way technology and its effects are perceived. To think that we are the ‘centre of the world’ is objectively a mistake, especially when countries of the calibre of Russia, China and, above all, Iran, are acquiring a great offensive cyber capacity.
The Russian model
It will not have escaped the notice of the most observant that Russia has, over the years, welcomed most of the hacker teams that have threatened the US and Europe. The REvil group, the Conti group, the LockBit group, etc. In the war between Russia and Ukraine, the Conti team was quite clear in its message of solidarity with Russia.
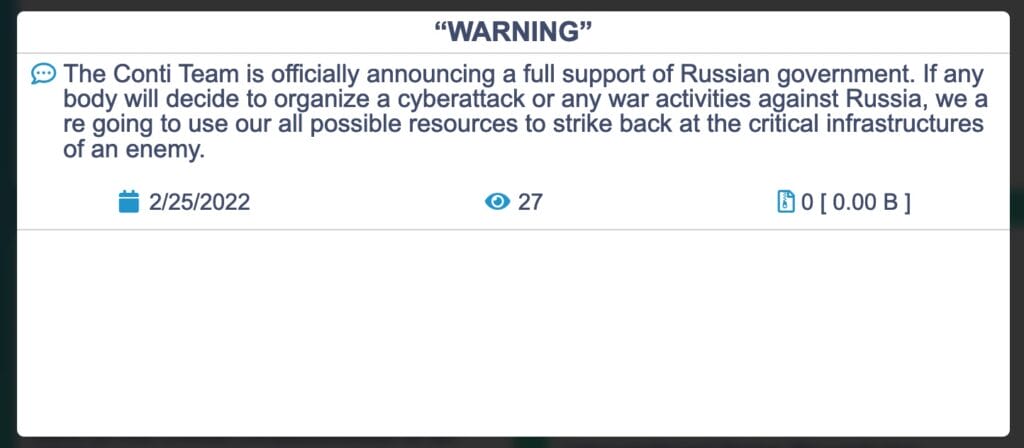
Russia has so exasperated this pattern that one of the most notable results was achieved in November 2021 at the GoldDust Operaio in which members of the REvil hacker team were arrested, but only after the joint intervention of Interpol, Europol, Eurojust and only after Biden had excluded Russia and China from the meeting on the growing ransomware threat.
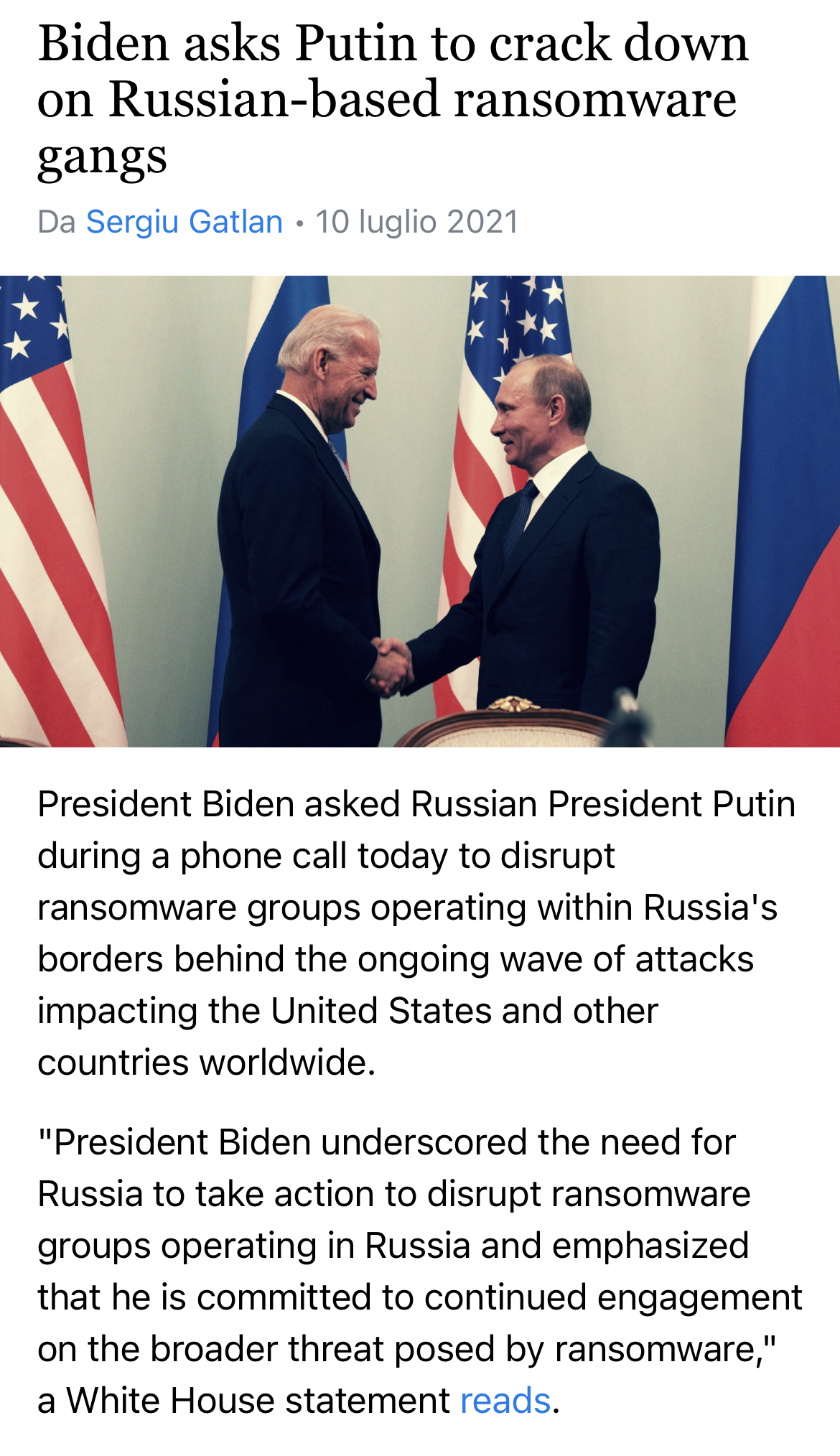
The escalation provoked by Russia subsequently hit Europe with numerous ransomware attacks that had a very precise purpose both in their targets and consequences. On the one hand, the resilience of the affected country and its cyber perimeter is being tested, on the other hand, the demand for profit of the team acting as an ‘armed wing’ is being met. There is also to be considered the high number of cyber threats that originated within Russian territory or were directly related to state interests.
The case of the Isaac Wiper
On 1 March 2022, information was circulated about the Isaac Wiper, which was discovered by ESET and documented very carefully. The malware aims to destroy data and information on infected computers and was built with an anti-forensic mechanism that prevents its action from being traced after deletion. The mechanism is based on self-subscription: the malware self-subscribes in order to prevent the reconstruction of evidence, and this is a practice that has been known for a long time. It has also been equipped with a ransomware mechanism used as much to damage as to distract from the real use of the virus. To better understand how these attacks work, one must look at the context. Close to the start of the war between Russia and Ukraine, Russia attacked its adversary in four different ways:
- A DDoS attack to block the reaction of systems
- An attack with the malware Hermetic Wiper
- A Hermetic Wizard attack to spread the threat on the local network
- An attack with Hermetic Ransomware to simulate a typical ransomware attack
In the excitement of the moment, with a DDoS gone wrong and ransomware in the network, it would have been difficult to understand the entire scheme. This articulated form of attack is also found in the Isaac Wiper and is the reason why Jean-Ian Boutin, Head of Threat Research at ESET, is linking the Isaac Wiper with the Hermetic Wiper.
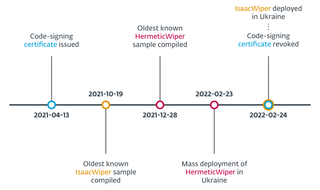
The Isaac malware first showed itself in October 2021 in its most complex form, soon after which the Hermetic Wiper was detected. You can therefore understand the logic why Hermetic is a descendant version of Isaac and better functioning. The Hermetic was adopted against the Ukraine as of 23 February 2022, but practically together with the release of the Isaac Wiper. For it to have been recognised months later (from 19 October 2021 to 24 October 2022) means that the virus was not modified in its composition, and this is also an important factor because it suggests that the Isaac Wiper may also have been used months earlier, in other operations. It is ESET itself that says so, by the way.
IsaacWiper appeared in ESET telemetry on February 24. The oldest PE compilation timestamp found was October 19, 2021, meaning that if its PE compilation timestamp was not tampered with, IsaacWiper might have been used in previous operations months earlier.
Source: ESET
There is, however, the certainty that it is not currently possible to trace this complex threat back to a specific group. One hypothesis is that the attack, in its complexity, could have been planned, carried out and executed by one of the numerous hacker groups ‘hosted’ by Russia in recent years.
The Chinese model
China, just like Russia, took part in numerous attacks on American institutions. By excluding it from the famous meeting, America had alerted other countries to the damage it had suffered, especially to the Microsoft systems that had been attacked.
The Microsoft hack affected at least 30,000 US organisations including local governments as well as entities worldwide and was disclosed in March.
Antony Blinken, the secretary of state, accused China of being responsible and said it was part of a ‘pattern of irresponsible, disruptive and destabilising behaviour in cyberspace, which poses a major threat to our economic and national security’.
Source: The Guardian
The Chinese response to these accusations was not long in coming: China replied that these accusations were fabricated by the US itself and its allies. This is a particularly strong, relevant statement coming from a country with very measured but not unimpressive responses. China’s orientation is reminiscent of Russia’s in terms of propaganda, but not only. The considerations made in the book Russian Brigades are very realistic: what for us is cybersecurity for China and Russia is information security. A substantial difference, not just a formal one, which translates into the way in which the actions under discussion are ‘weighed’.
The Iranian model
The reality of Iran is also very similar to that of Russia and China: the MuddyWater group has infected numerous nations with malware and intelligence has shown how this collective is ‘government-sponsored’. MuddyWater is known to have attacked Turkey.
MuddyWater, a hacker group linked to Iran’s Ministry of Intelligence and Security, is allegedly behind these cyber attacks, which involve infection vectors such as malicious PDF attachments and Microsoft Office documents embedded in phishing emails. These malicious documents were titled in the Turkish language so they would present as legitimate texts coming from the Turkish health and interior ministries.
Source: ArabNews(LINK)
The Iranian situation was further made known during the Russian-Ukrainian conflict when the US and UK made a joint communication:
As the Russian invasion of Ukraine spilled over into the cyber realm, Iranian hackers affiliated with the country’s military intelligence have launched a global cyber espionage campaign, the U.S. and the U.K. said in a rare warning issued over the weekend.
Source: Haaretz(LINK)
The problem of the Italian press
On more than one occasion, the news has been reported in a sensationalist tone and with an approximation that does not give a clear idea of what is happening. Let’s take the Isaac Wiper threat: ESET confirmed that the threat was first seen in October 2021, but ANSA breaks the news on 3 March like this.
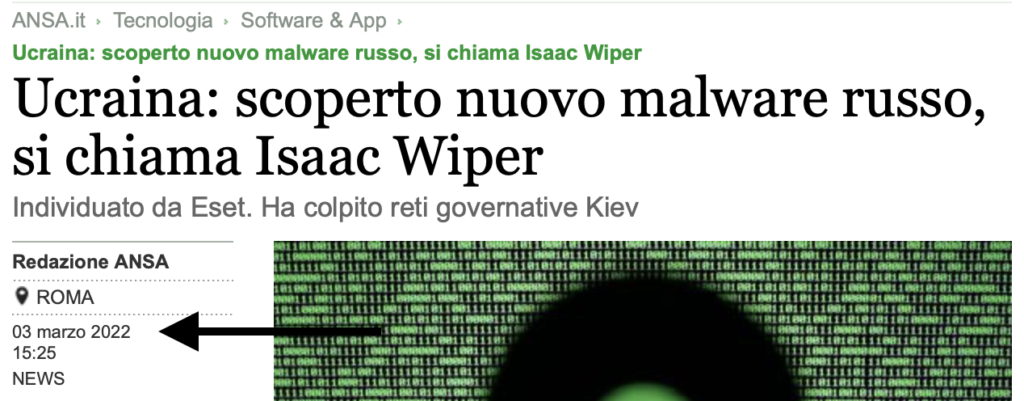
The news was picked up by so many editorial publications, completely ignoring the dates, the history of the virus and, as a result, changing the perception and the actual importance of this in the Russia-Ukraine conflict. The superficiality in many editorials is such that it verges on embarrassment and prevents an intelligent reconstruction of the events that, instead, paint a much more interesting picture of war strategy. The PDF of the ANSA article can be downloaded below. The origin of the title derives solely from the fact that ESET published the news about the Isaac Wiper on 1 March 2022, and the Italian news headline was affected by this because there is actually nothing too new in the Russian malware. As of 3 March, Ukraine is bowed down by shelling, the outskirts of Kiev are almost completely destroyed, tanks are now at the gates of the centre, and there is talk of evacuating civilians with humanitarian corridors (a signal, generally, of the final offensive). One would not intelligently explain the introduction of a new malware at this point in the offensive. Instead, on investigating ESET’s own site, it turns out that Isaac Wiper was the subject of attacks well before March 2022 and contributed to inflicting not inconsiderable cyber damage on Ukraine.
Conclusions
The Russian model with regard to info security and info war denotes a relevant cultural aspect that extends to the whole area of propaganda and complication. There is, in fact, a different cultural conception as to how the offensive and defensive side of information technology is managed, and this conception certainly conditions the actions but, above all, the way of understanding the actions of other countries. It is therefore not only a question of favouring a modus operandi in relation to threats, but also of compromising or making dialogue with other nations more complex. In relation to war, we had looked at some formal and substantive aspects of war in this blog (I recommend reading it).

