The war between Russia and Ukraine is undoubtedly showing itself in all its complexity, and among the various actors who are taking part in the clash, there are also hackers. It is the first war in the history of mankind that is being fought on social media and with a massive use of hackers: and perhaps it is precisely this sharing that will prevent a dangerous escalation.
How the Ukrainian front is organised from a technological point of view
It is very difficult to get a definite picture of the situation, but in an attempt to bring more clarity, it could be represented as follows.
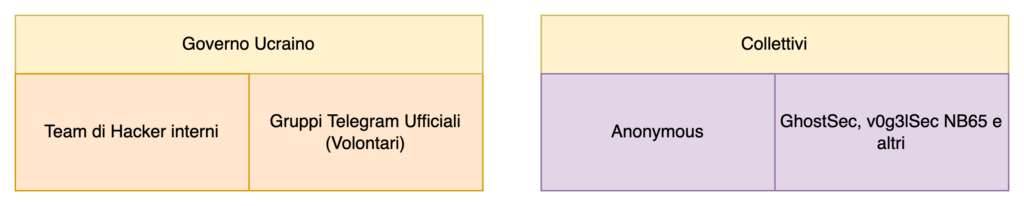
On the one hand, there is the Ukrainian government, which has its own official resources. Some 44 hackers within the government would be involved in the most relevant sabotage and propaganda actions. During the first days of the war, Minister Fedorov created several Telegram groups inviting volunteers for sabotage actions carried out with DoS attacks against Russian institutional targets (banks, government sites, etc.).
On the other hand, there are the hacker collectives, of which undoubtedly the best known are Anonymous and GhostSec, but there are others of lesser stature but of equal importance.
25 February 2022 – (2nd day)
The position of ransomware collectives
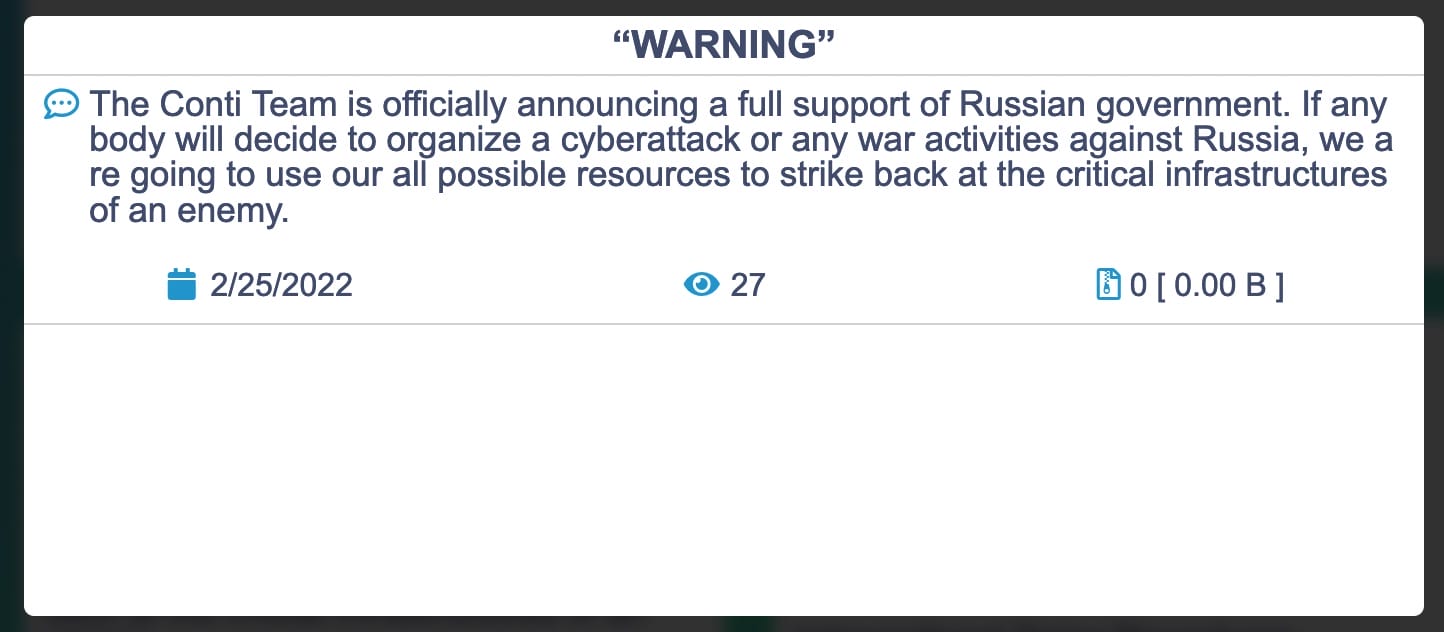
On the one hand, there are the collectives such as Conti or CoomingProject who, in Russia, have found a place of protection and from which they have launched attacks on the whole of Europe, as well as the United States.
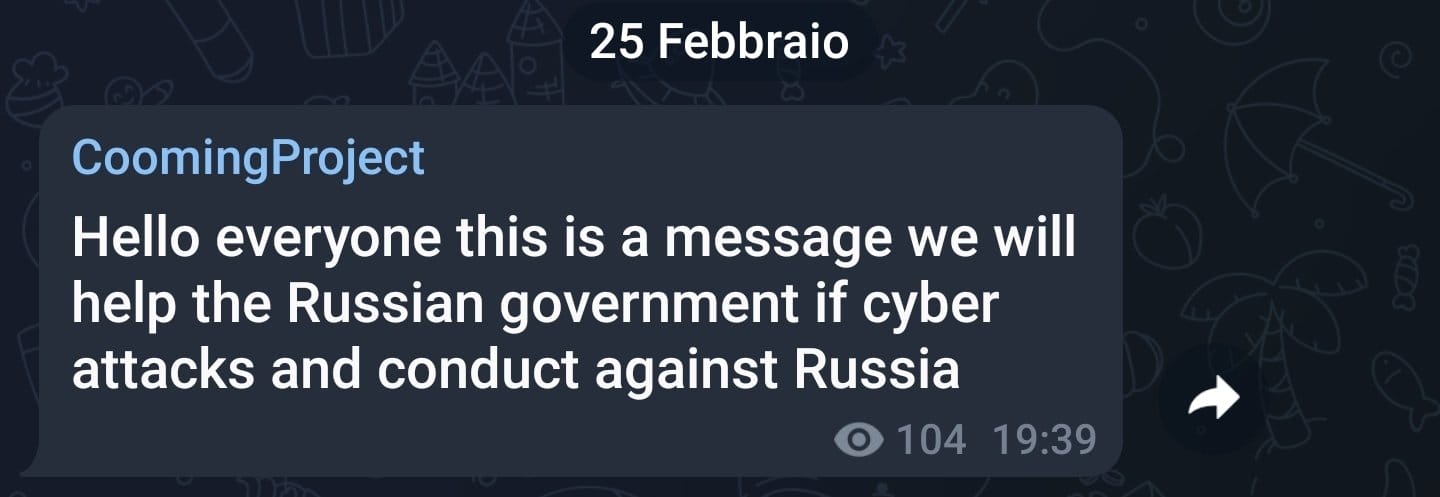
Their position is clear enough and has shown itself through unequivocal messages. CoomingProject clearly wrote:
Hello everyone this is a message we will help the Russian government if cyber attacks are conducted against Russia
A clear and also quite predictable position of affiliation. Without Russia, the hacker collectives would certainly have a harder life. Then there is the Conti collective, which published two rather conflicting communiqués.

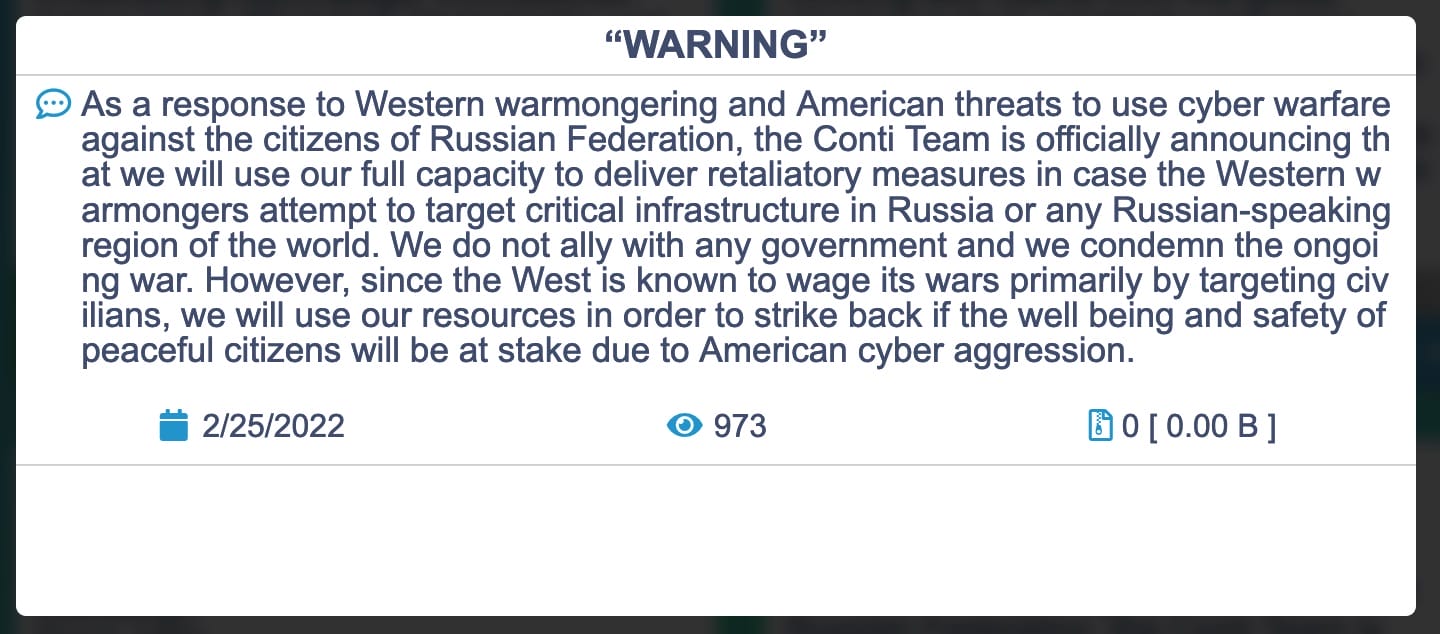
The former expressed ‘full support for the Russian government’ while in the latter the position was mitigated with the phrase ‘We do not ally with and government and we condemn the ongoing war’. A ‘comfortable’ position for a team that has always entrenched itself behind the support and cover of the Russian government.
The position of Anonymous
Then there are those who, like Anonymous, wage a battle almost as if to balance the sides: on 25 February, the collective managed to hit a number of Russian government sites, as well as perform a data breach exposing the data of some Russian military personnel.
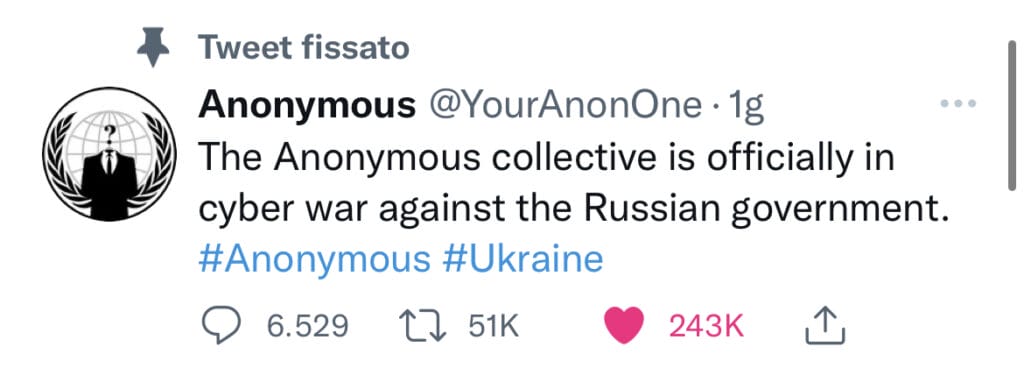
The participation of hackers in war conflicts is, to some extent, a novelty in this century. Mainly because these groups do not belong directly to state organs such as, for example, spies or intelligence groups. Instead, they are independent parties who, for social or profit reasons, choose a side and carry out their battle. It is certainly a new way of conducting warfare that deserves to be explored in depth.
26 February 2022 – (3rd day)
Hacking of radio communications by Anonymous
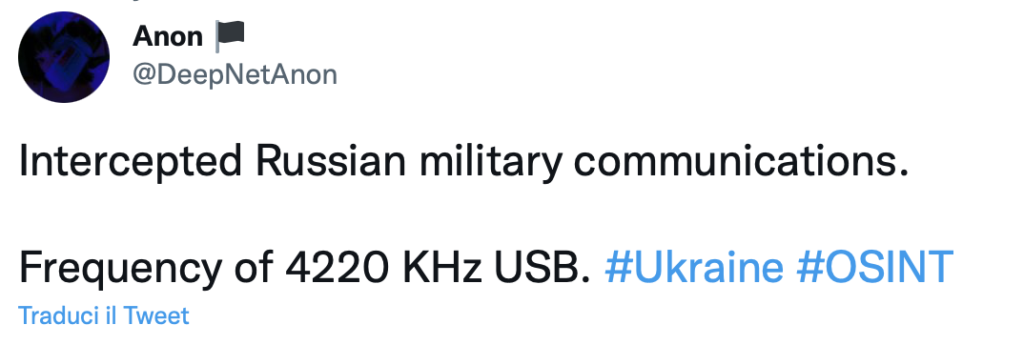
At 5.48 am on 26 February 2022, Anonymous publishes a news item: some radio communications of the Russian military were intercepted. A video is published.
Ukraine’s recruitment of hackers
In the meantime, Ukraine regularly proceeds with the creation of a ‘cyber army’ and posts a public announcement on Twitter.
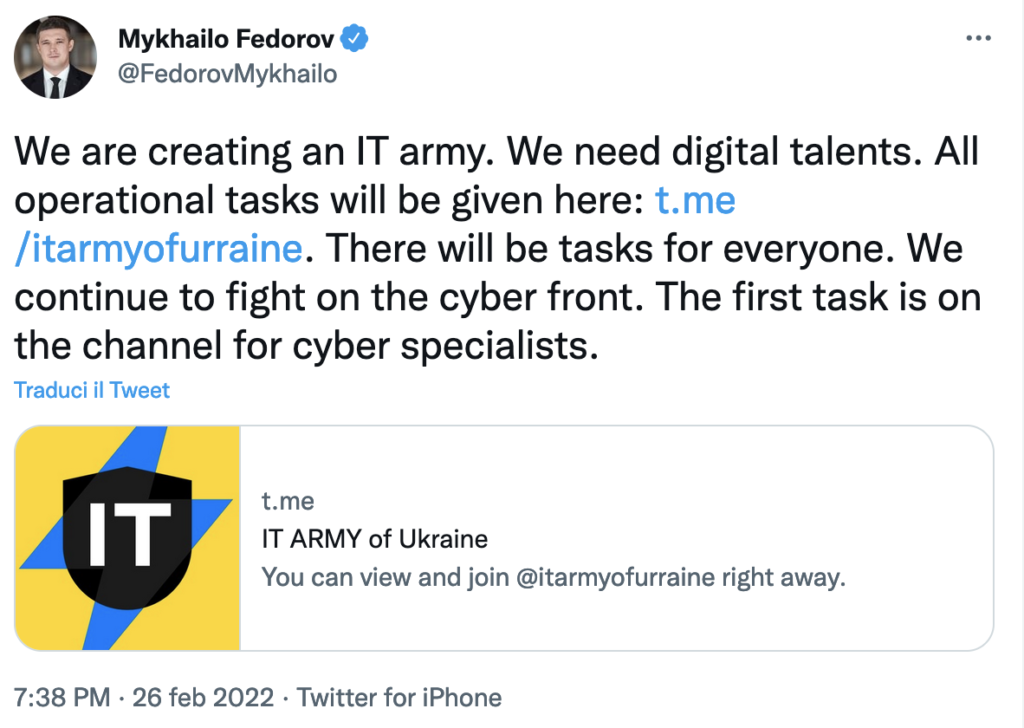
This is done by Mykhailo Fedorov, Deputy Prime Minister of Ukraine and Minister of Digital Transformation of Ukraine. The choice of online recruitment is a novelty that confirms the above.

The Telegram group of which Fedorov posted the link already had over 82,000 members at 21:38 on 26 February 2022. Fedorov’s request aims to use DoS against some of Russia’s most popular portals, and the fact that it is public favours a larger number of potential contributors.
Fedorov himself, in the middle of the day (13:31) had posted addresses to which donations could be made to support the Ukrainian cause by sending cryptocurrencies. In the evening (21:49), he broke the news that YouTube had disabled the monetisation of the Russia Today channel. Elon Musk’s response comes a few hours later and is, objectively speaking, exciting.
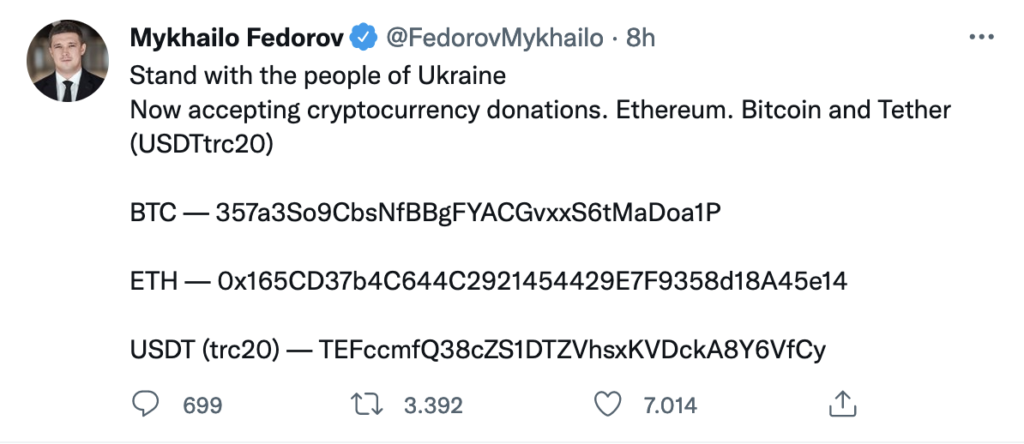
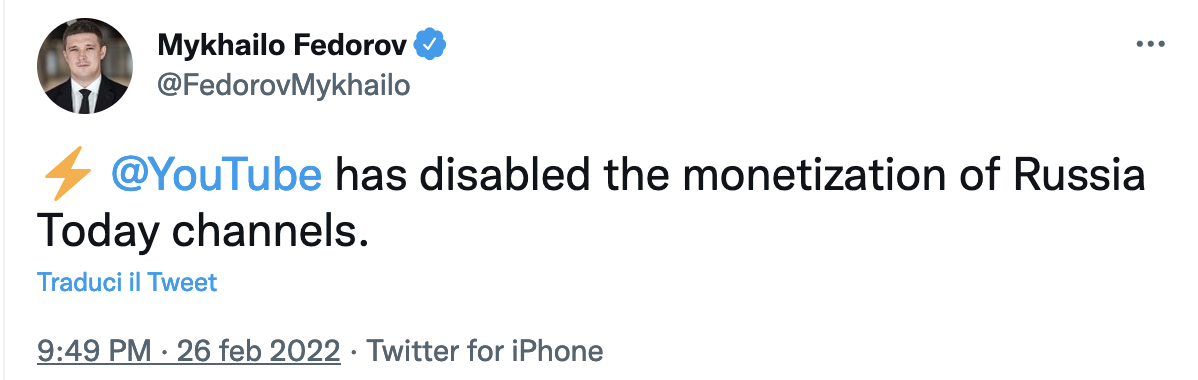
The back-and-forth with Elon Musk
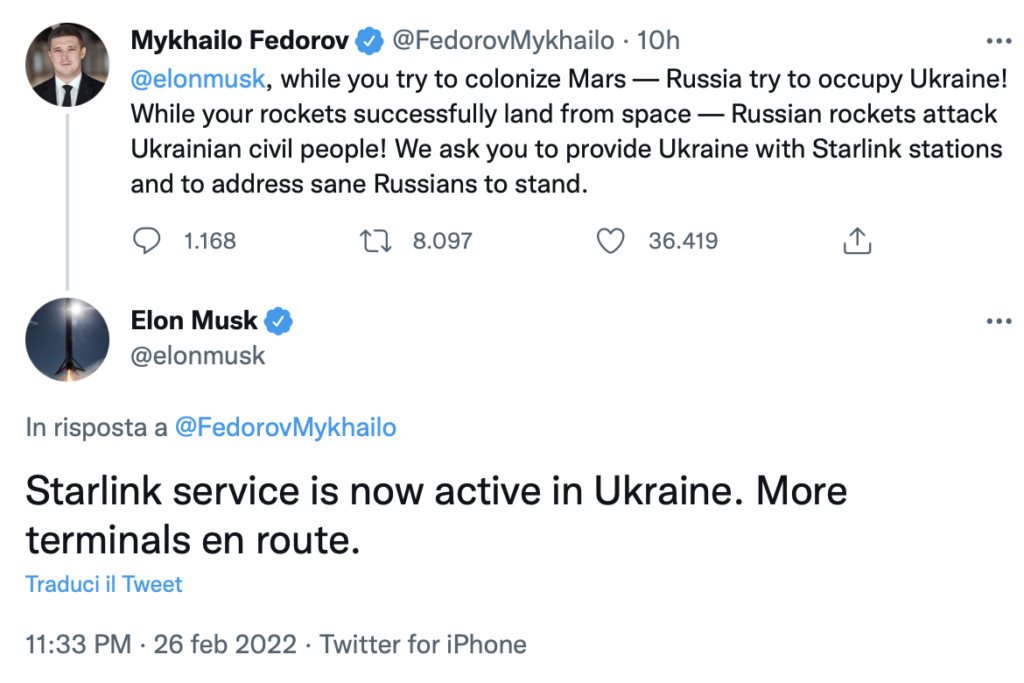
In addition, Fedorov appealed directly to Elon Musk to support the Ukraine via Starlink, the system with which the earth’s suborbital satellite network can be exploited to obtain internet. The request is a clever one: while the wired network can be interrupted by tampering with the various communication centres on the ground, the satellite network is more complicated to hinder.
Hacking of some Russian TV channels
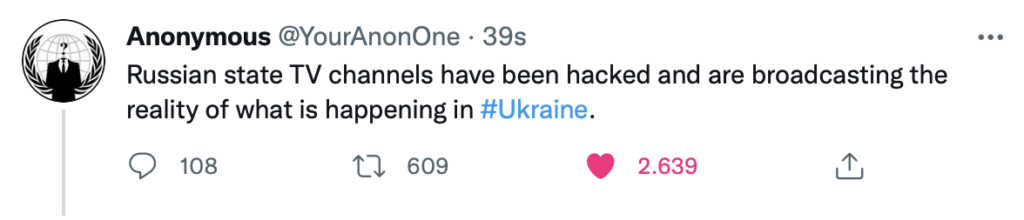
At 10:20PM, the Anonymous collective published a tweet in which it confirmed that some Russian TV channels had been hacked.
The action of Anonymous is also aimed at mitigating the effects of the censorship that Russia allegedly applies on its communication channels. Press and television, in fact, are allegedly subject to constant censorship aimed at severely limiting the dissemination of news on the progress of the war, and in particular on the outcome and the number of victims.
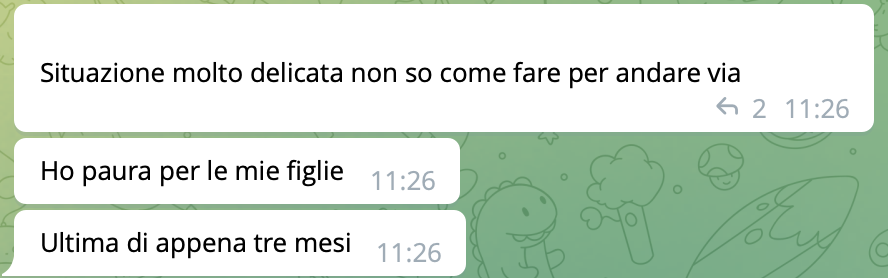
Telegram and the Italians in Kiev
Meanwhile, there is a debate on Telegram to help an Italian who, having remained in Kiev, is wondering what is best to do: flee or find refuge. His brother, in an attempt to find a solution, is urged to stay as calm as possible.
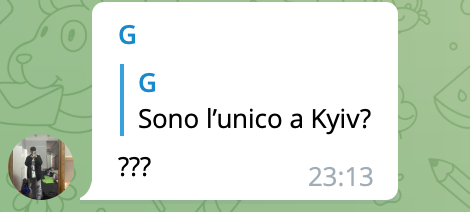

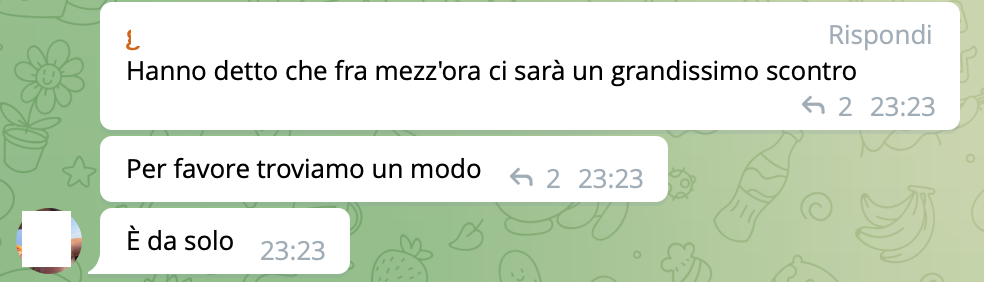
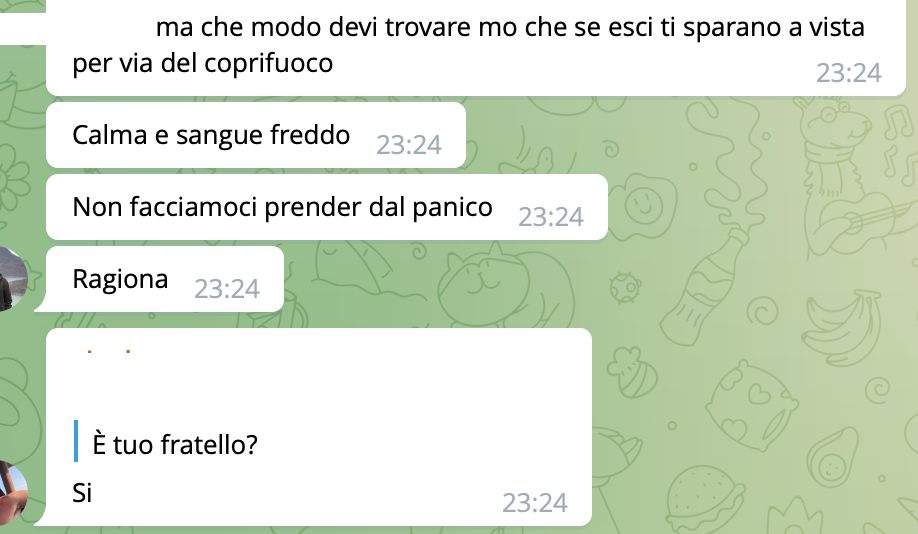
The conversation goes on to recommend contacting the embassy:
The embassy is open in the capital and there is staff
No we called and they are closed. They only said to stay sheltered
The Italian in the group responds by providing the area where he is located: Voskresenka, which is a district of the city of Kyiv as shown on the map below.
27 February 2022 – (4th day)
YouTube channel reporting mobilisation and DoS extension
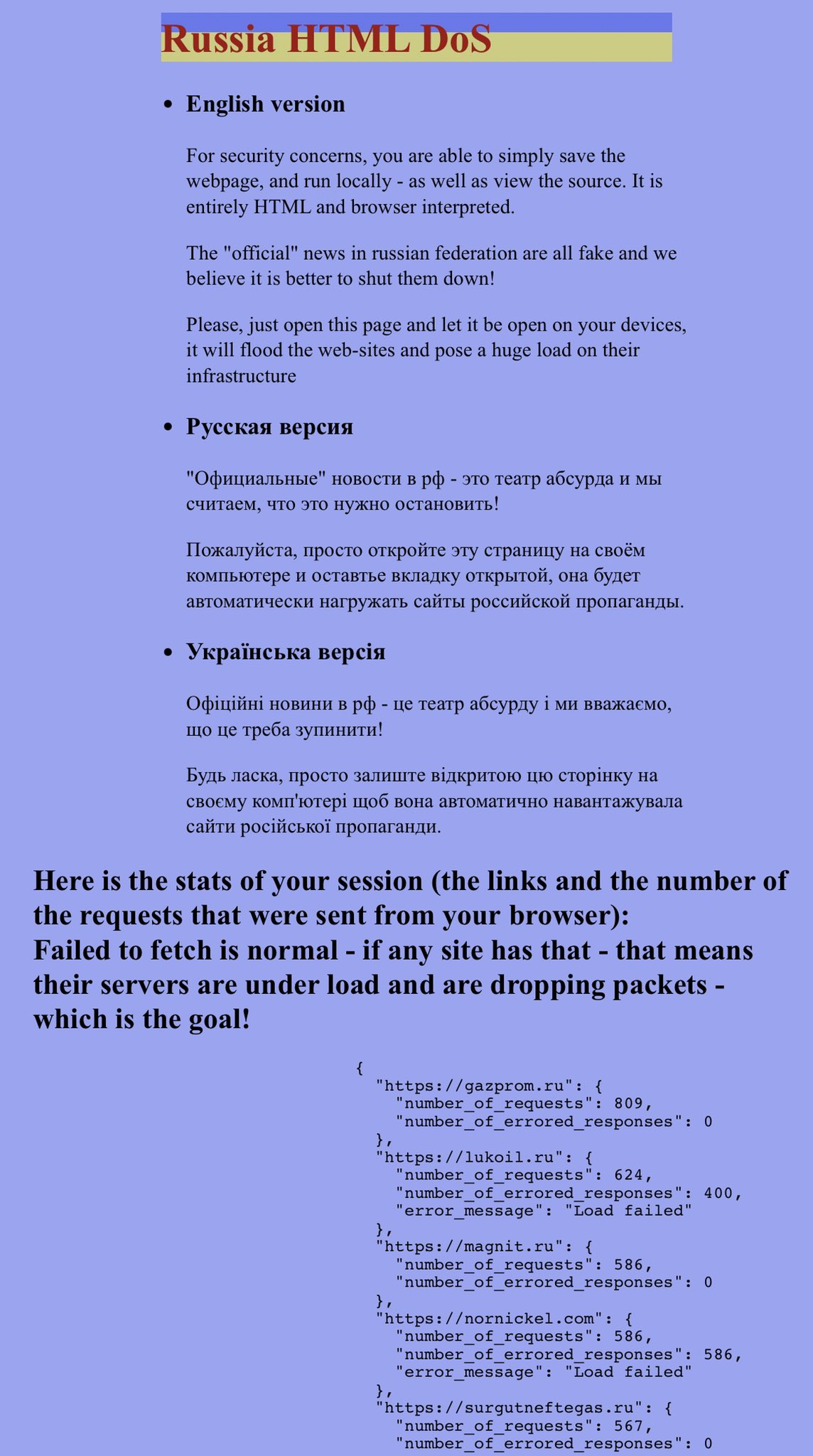
Fedorov’s YouTube action extended to individual users around the world who, on the basis of a list of links provided by Ukraine, began reporting them to YouTube as illicit. Some pentesters provided html files capable of launching DoS attacks on Russian domains believed to be Russian propaganda targets. Clearly, some of these domains were unavailable except for internal Russian traffic.
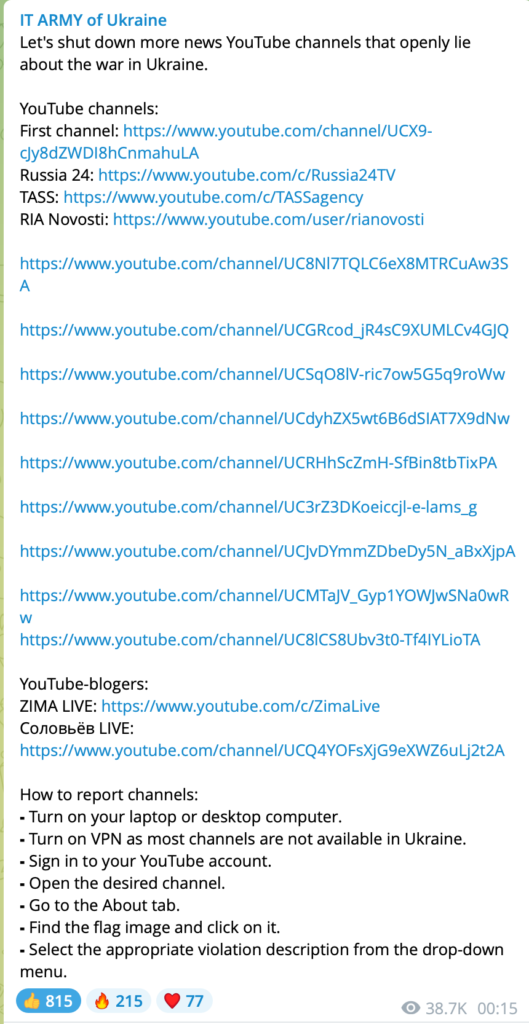
Request for the blocking of Meta, Rakuten and PayPal services by Ukraine
It is 1:08 a.m. on 27 February and Fedorov tweets a message officially requesting Rakuten and PayPal to suspend their services to Russia.



The development of Telegram channels
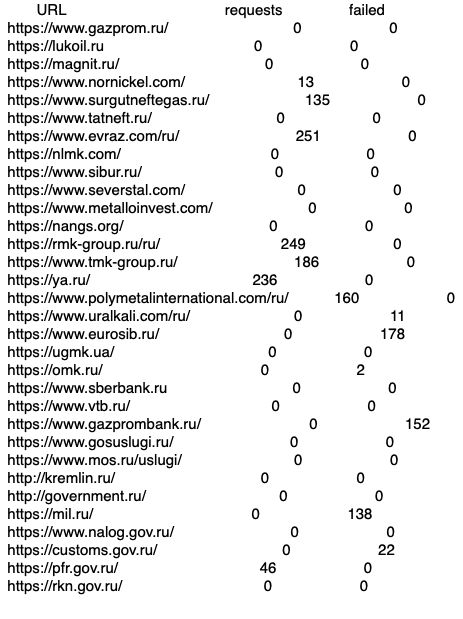
In the morning at 08:00 on 27 February, Kiev still resists the Russian invasion attempt. Fedorof’s Twitter channel still stands by the request made to Meta, but in Telegram chats, requests to participate in DoS attacks from anywhere in the world, even from Mexico, persist. It doesn’t look like Ukraine’s war, it looks like the world’s war against a statesman whom everyone considers insane, if not murderous. The number of subscribers on the official cyber-force recruitment channel now numbers over 140,000. In addition, there are ‘pirate’ chats with a large number of participants. The status of DoS attacks, according to Kaspersky, places Russia as the first nation under attack, however Kaspersky is deemed ‘biased’.
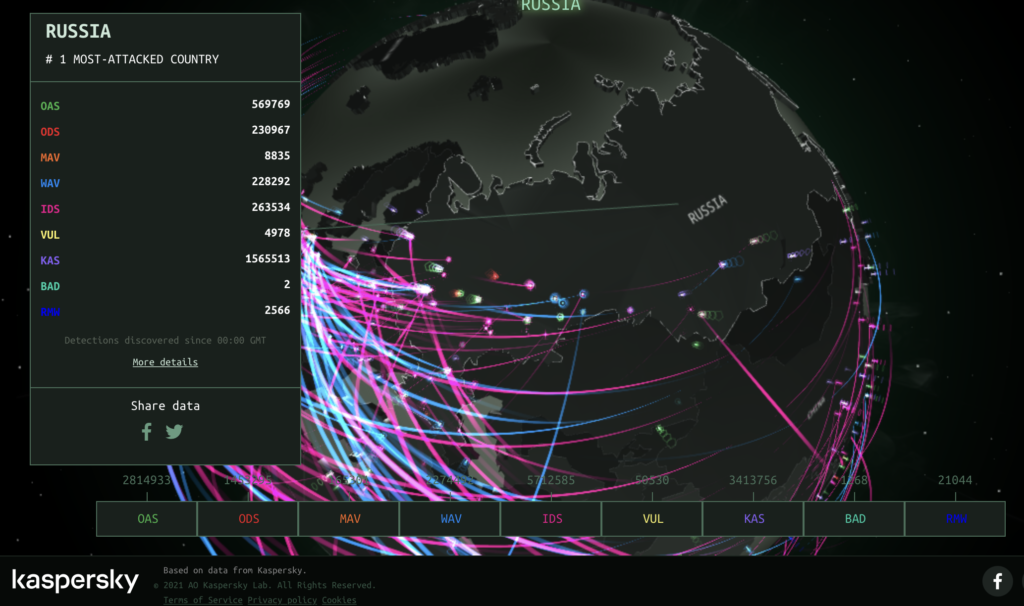
TheA10 Research Group ‘s map would seem to indicate the same thing in the face of a massive and numerous attack against Europe, Russia has a concentration of DDoS attacks on Moscow and beyond.
Problems with the mobile network in Kiev, GPS deactivation and brand concealment
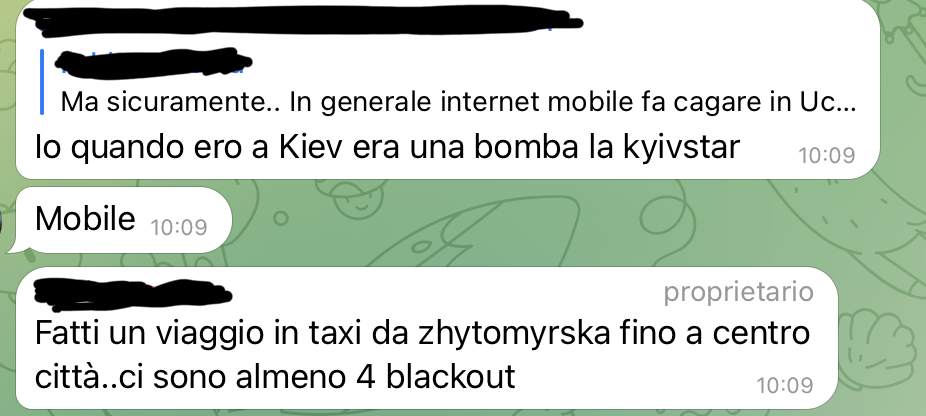
Meanwhile, there were also some mobile network blackouts, documented by the Italians in Kiev. The mobile network, during the night, was essential for exchanging information on the shelters, the health condition of the participants and for getting updates.
In the meantime, a very important campaign has started to deactivate GPS on the phones of those in Ukraine. The signal can provide useful indications for the Russian military and, from what we also hear from Italians on the ground, the Ministry has reportedly requested that the signal be deactivated.
According to reports, the Ministry also requested the possible concealment of marks made with the spray can to disorient the Russian advance.
Information campaign for Belarus

At 10:05 a.m., a message arrives on the Ukrainian government’s Telegram channel calling for information actions in Belarus. The Belarusian government is providing support to Russia and the hope is to repeat the information campaign that took place yesterday (26 February 2022) but specifically dedicated to Belarus. The information campaign is supported by the huge number of participants in DDoS attacks, which are also spread through social, instant messaging and GitHub pages
Fedorov calls for suspension of Visa and Mastercard and cryptocurrencies
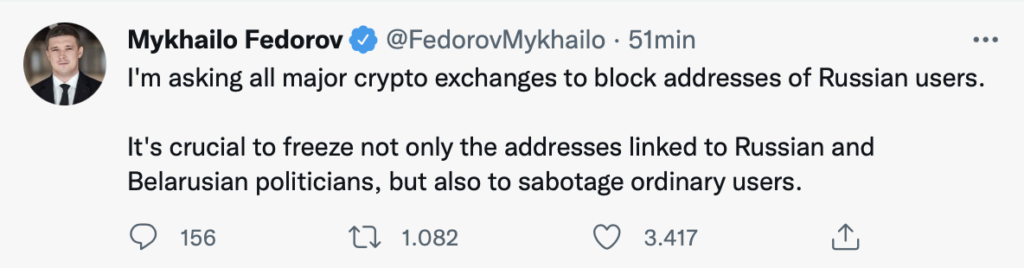
While the war is being fought on the battlefield and is certainly a war of position, i.e. of resistance to the Russian invasion, Fedorov insists on blockades of Russia’s essential services. Today it is the turn of Visa and Mastercard, as well as cryptocurrency services.
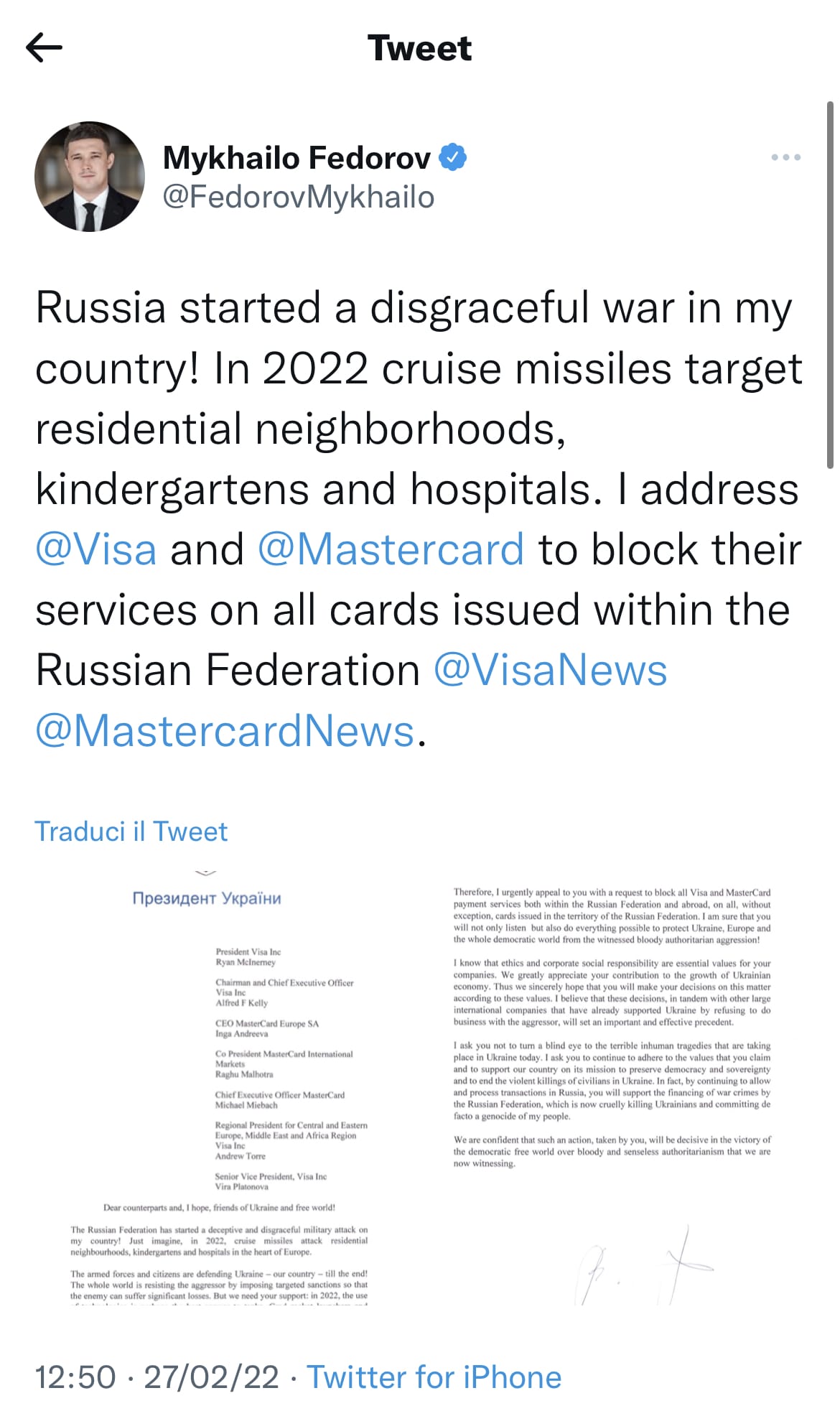


Fedorov and the strange case of the $4.5 MLN from Dmarket
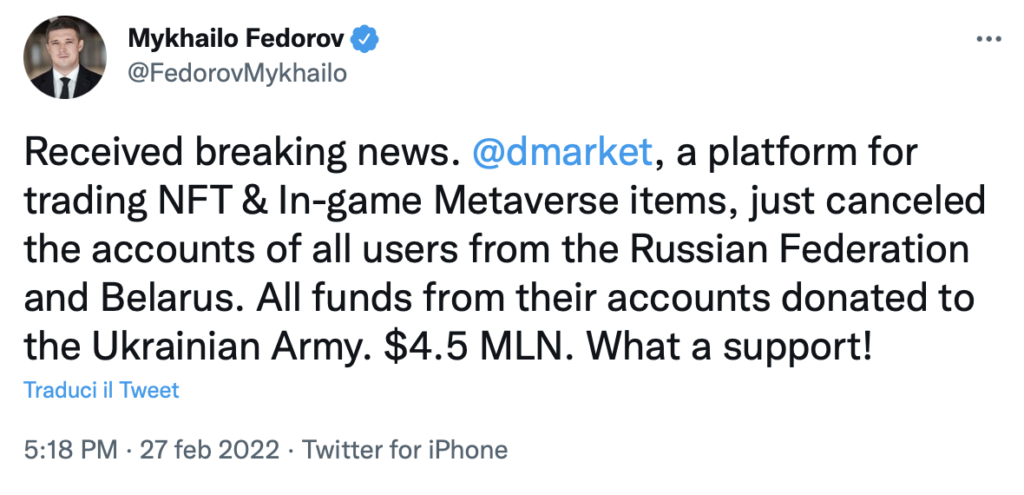
At 17:18, Fedorov published a tweet in which he stated that the online gaming platform DMarket (a Ukrainian start-up) had deleted the accounts of Russian players and had proceeded to transfer the economic resources of these accounts (the money would be used to buy NFT and in-game items) to the Ukrainian army. The news was strange from the outset: it would have been an excessively coercive action against Russian users who had no responsibility for the war, and the sum of 4.5 MLN would have been very substantial. However, DMarket’s response was not long in coming and, as expected, contained a partial denial.
Anonymous takes control of a pipeline and threatens to change the pressure
At 17:33, the hacker collective Anonymous claimed to have taken control of a Russian gas pipeline remotely and to have been able to raise the pressure until it exploded. The gas pipeline in question is in the Nogir and the news is particularly relevant.
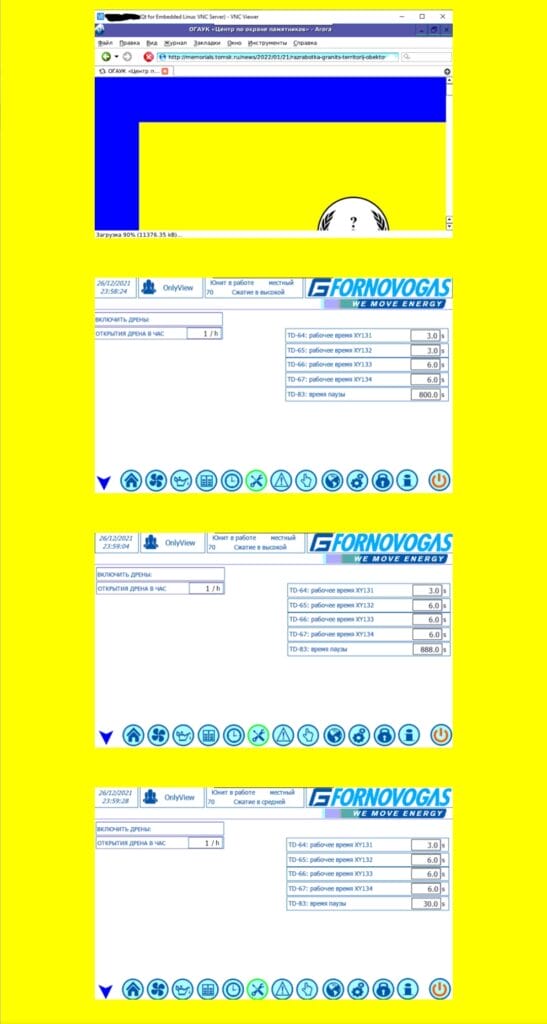
Fornovogas, as the name suggests, is an Italian company in the municipality of Traversetolo, in the province of Parma. It is a company that produces gas compressors as well as other components.
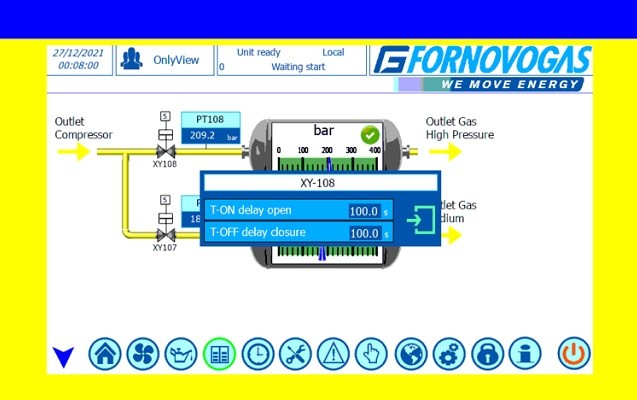
The screenshots that Anonymous posted do, in fact, refer to pressure management, but they have dates that do not coincide with the current one. During the raid, in their style, Anonymous changed some parameters as shown in the image below. They also radically changed the time.
The GhostSec collective broke into the server of the Russian Department of Information Projects
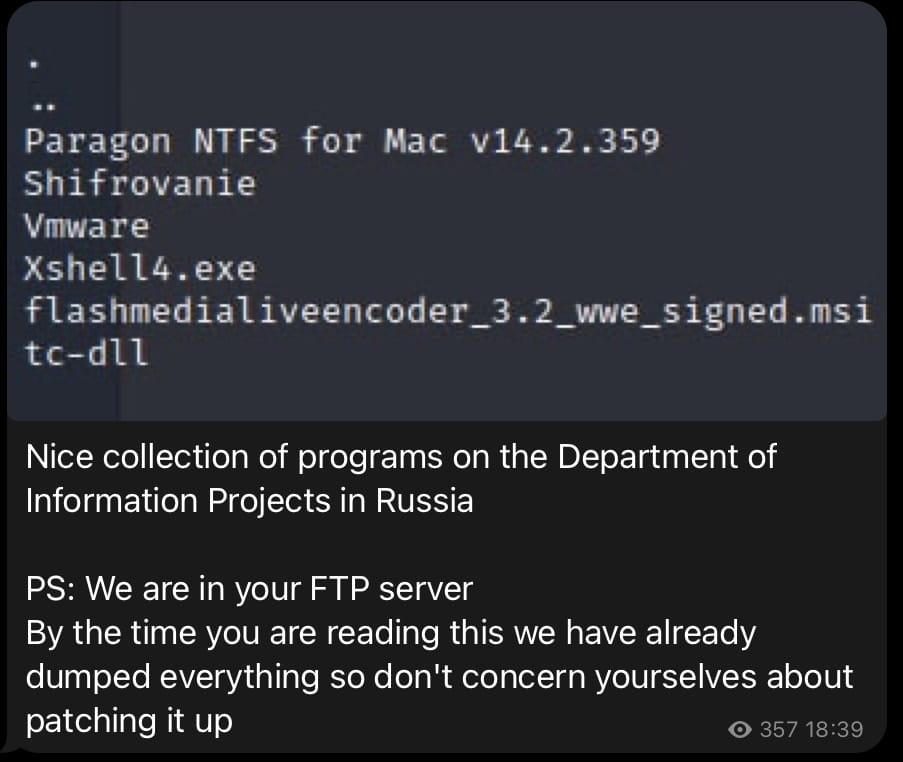
It had been requested yesterday by Fedorov himself and today the GhostSec collective managed to get in via FTP, inside the Russian Department of Information Projects.
44 official hackers and a boundless community
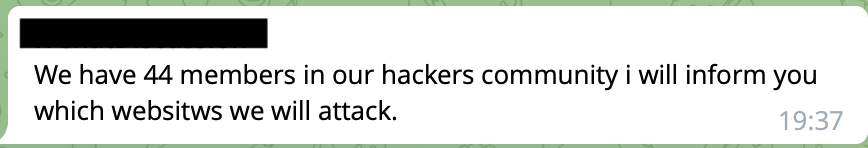
The Ukrainian government has organised several hacker groups, which are joined by various collectives such as Anonymous or GhostSec, but also a very large number of volunteers. One certainly major problem is the proper coordination of all this mass of people who, with varying experience, try to contribute to the Ukrainian cause. Not everyone, in fact, has adequate experience and it is not always easy to bring large groups of users together.
The Putin yacht affair
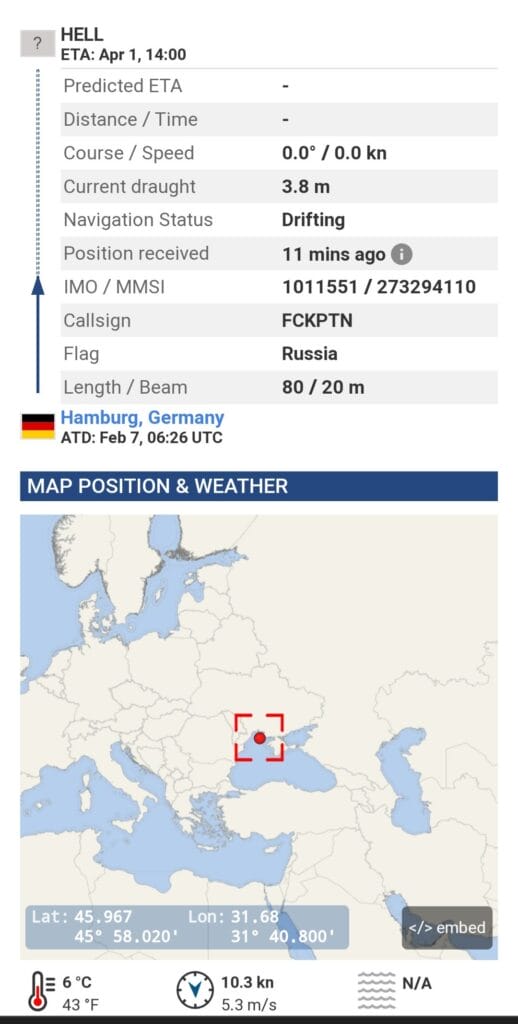
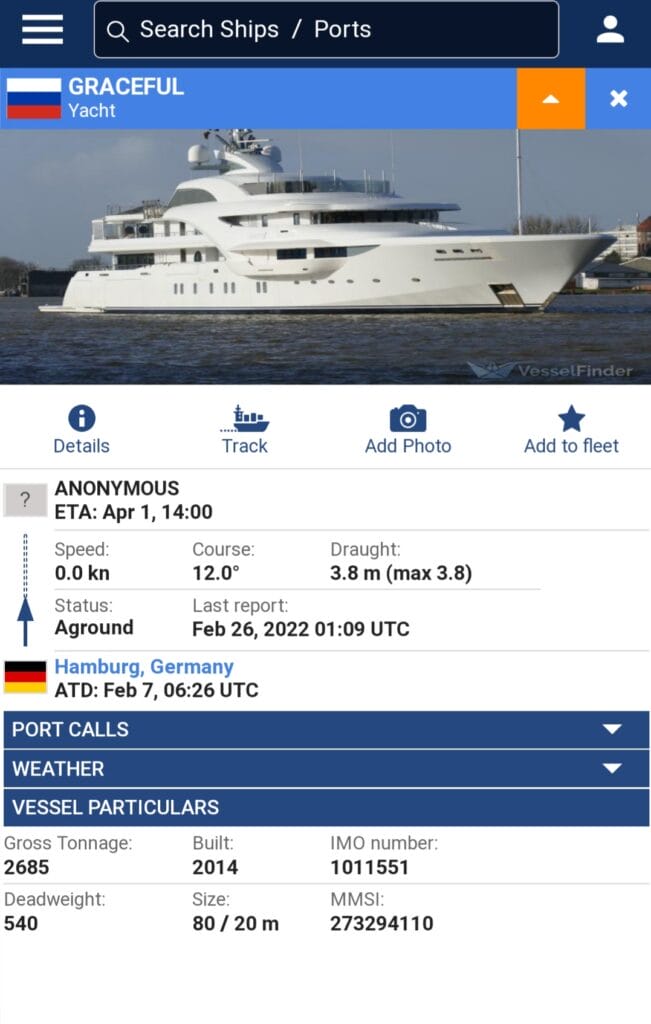
Putin’s yacht ‘Graceful’ was hacked by a group from the Anonymous collective and sent against some rocks. The rather amusing thing is that the yacht’s maritime data has been altered, making it appear that the yacht is destined to literally go to hell, with scheduled arrival on 1 April at 2pm.
28 February 2022 – (5th day)
Anonymous attacks Belarus
At 2:05 a.m., the Anonymous collective published an important tweet: a DoS attack against Belarus has rendered some of the country’s targets unusable.
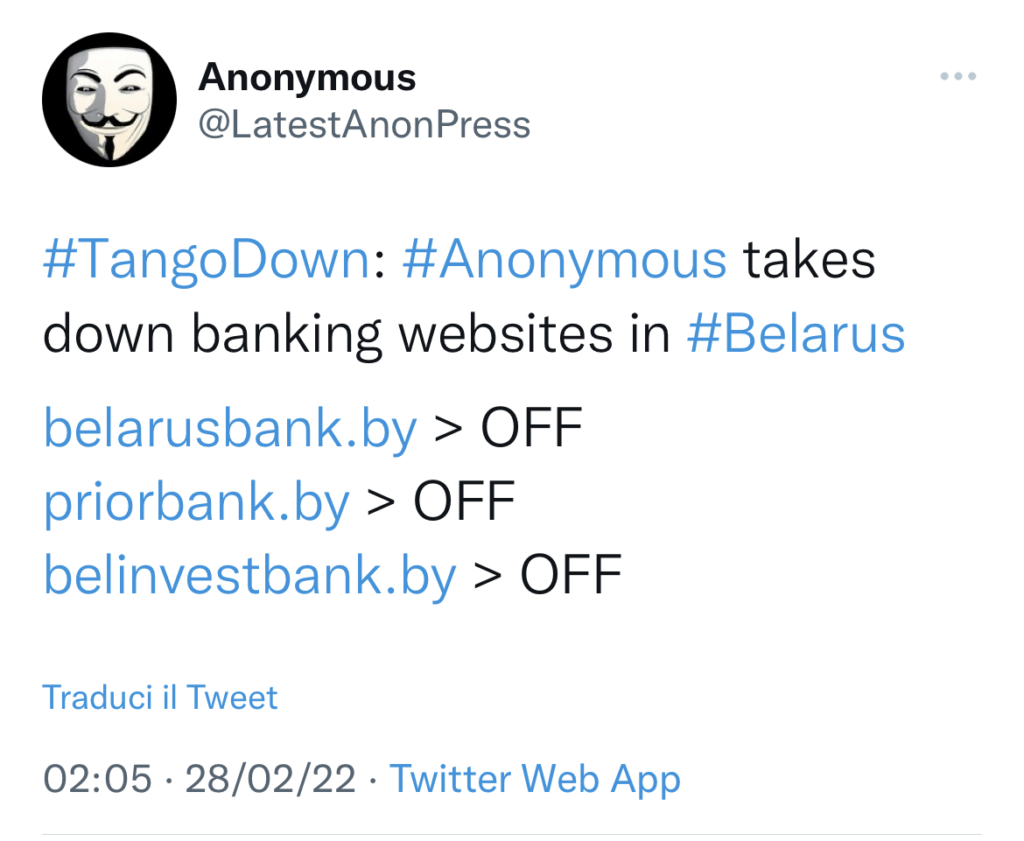
The list includes three banks: Belarus Bank, Prior Bank and BelInvestment Bank. Meanwhile, Anonymous Brazil has produced a ‘guide’ to Russian censorship with the aim of raising awareness and informing citizens about Putin’s ‘unspoken’.
The database of Russian oligarchs
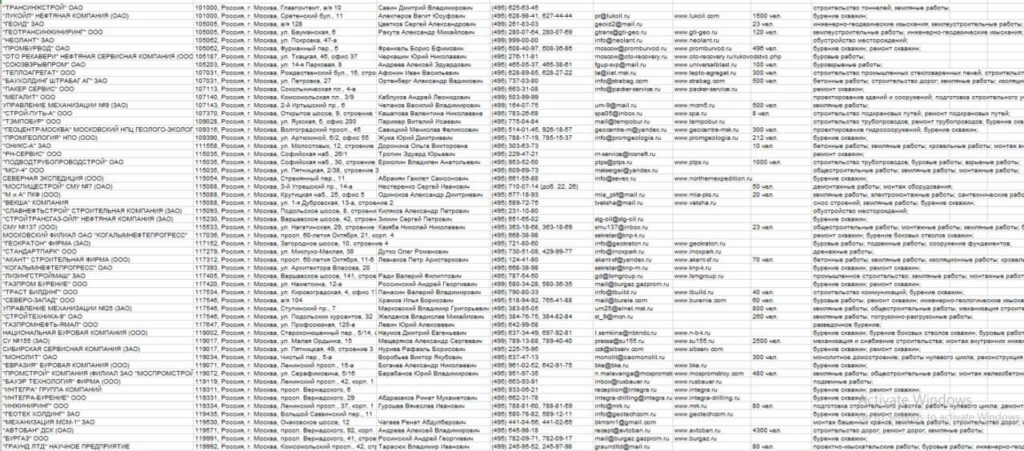
In the past few hours, there has been much discussion that some Russian oligarchs have allegedly left Russia to expatriate. A list of these oligarchs appeared within the Ukrainian internal channels dedicated to cyber attacks. The data have been analysed (as far as possible) and indeed show references to companies and people in the Moscow area.
The Gamaredon Group
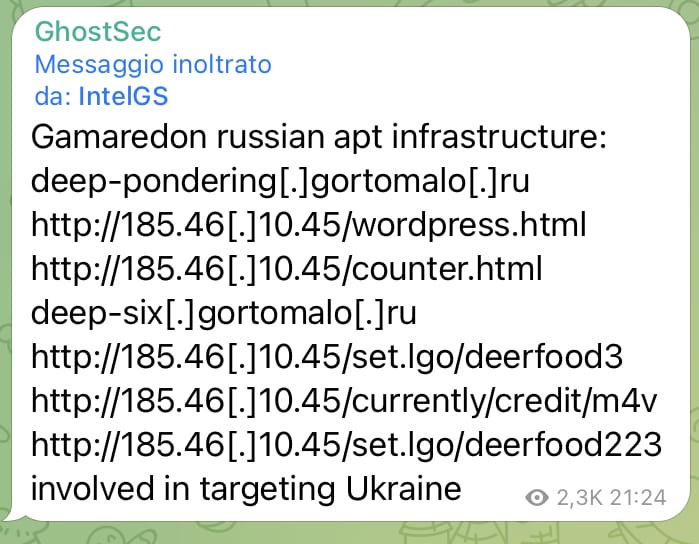
Gamaredon is a hacker group based in Russia that has started to threaten Ukraine with a series of not inconsiderable attacks. The group on Malpedia is known as this:
Unit 42 threat researchers have recently observed a threat group distributing new, custom developed malware. We have labelled this threat group the Gamaredon Group and our research shows that the Gamaredon Group has been active since at least 2013. In the past, the Gamaredon Group has relied heavily on off-the-shelf tools. Our new research shows the Gamaredon Group have made a shift to custom-developed malware. We believe this shift indicates the Gamaredon Group have improved their technical capabilities.
Source: Malpedia
Today, the GhostSec collective reportedly intercepted the IPs of the APT (Advanced Persistent Threat), an appellation used to define those actors who ‘persistently and continuously’ pose a threat to cybersecurity.
Italian CSIRT raises security measures further
The Italian CSIRT published at 16:50 on its website new security measures to mitigate threats from the conflict between Russia and Ukraine. The information can be found at this website address.
StarLink antennas arrived successfully in Ukraine
It was at 9.19 p.m. that Fedorov’s Tweet announced the delivery of the StarLink antennas, transported on a military truck and packed tightly.

NameCheap terminates services for Russians
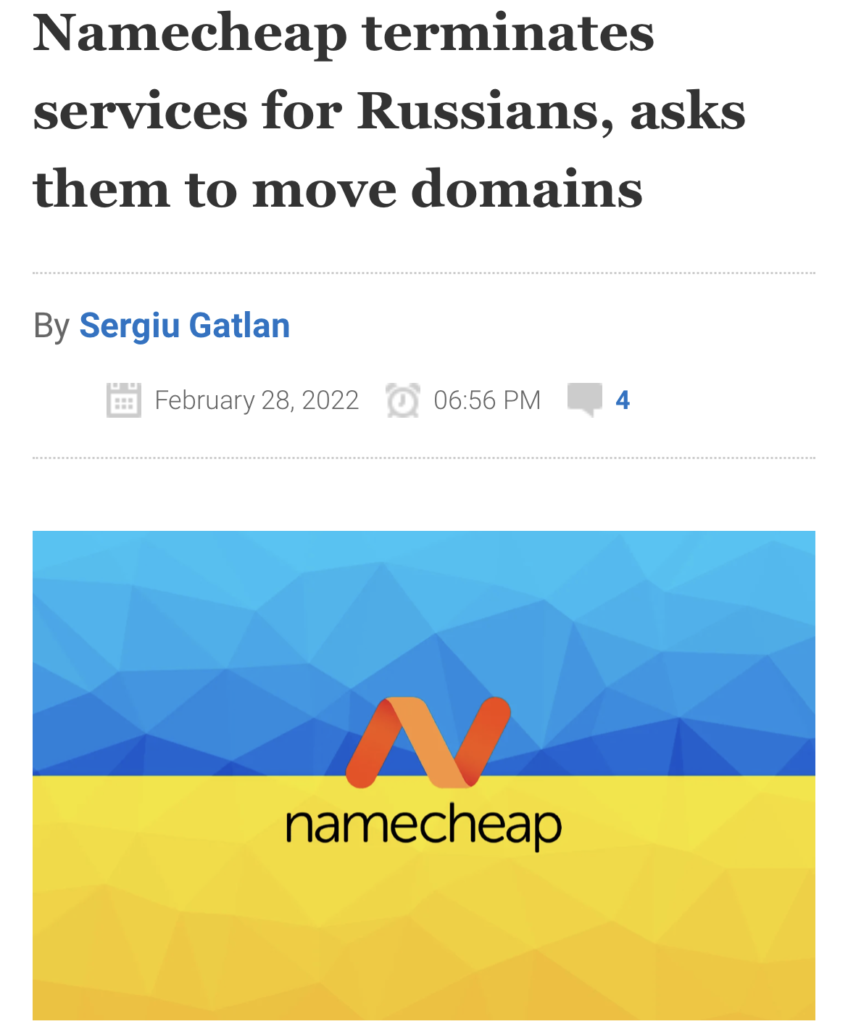
The internationally known hosting and web services provider NameCheap has decided not to support the Russian population on its platform, calling for domains to be moved to other providers. The news affects thousands of users and is another of the actions taken by companies outside the conflict in an attempt to pressure and undermine Putin’s war strategy.
GhostSec publishes diagrams on the NICA Booster
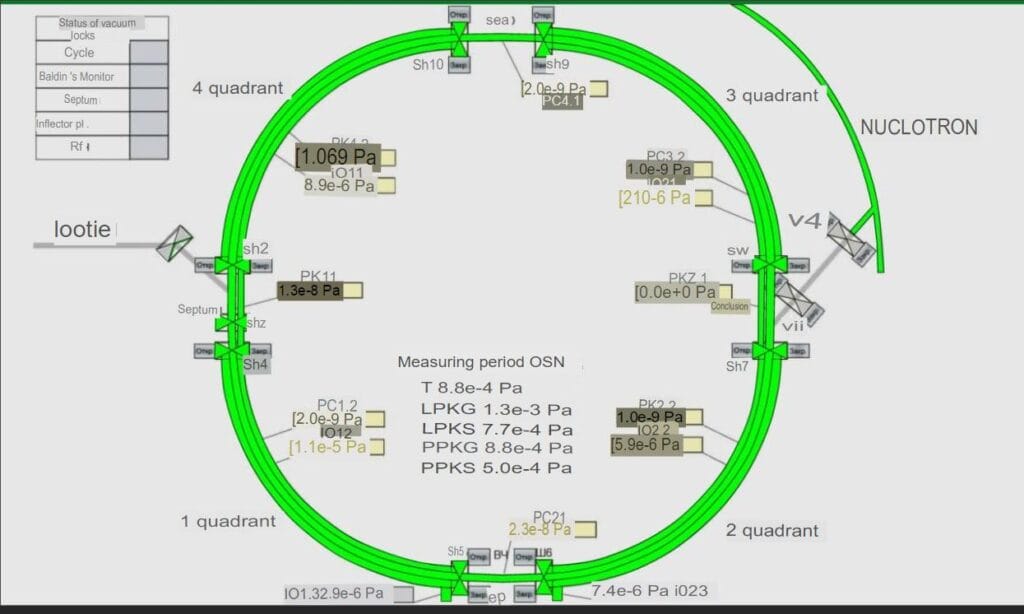
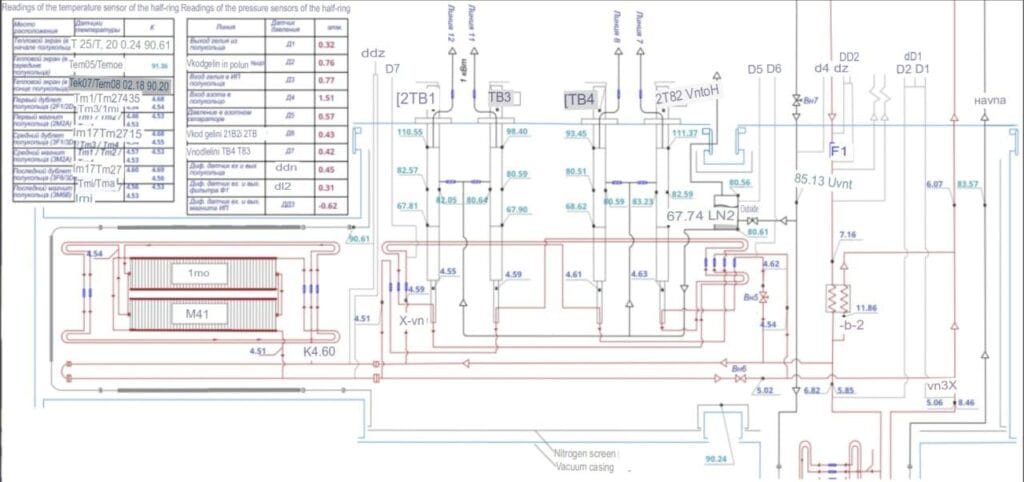
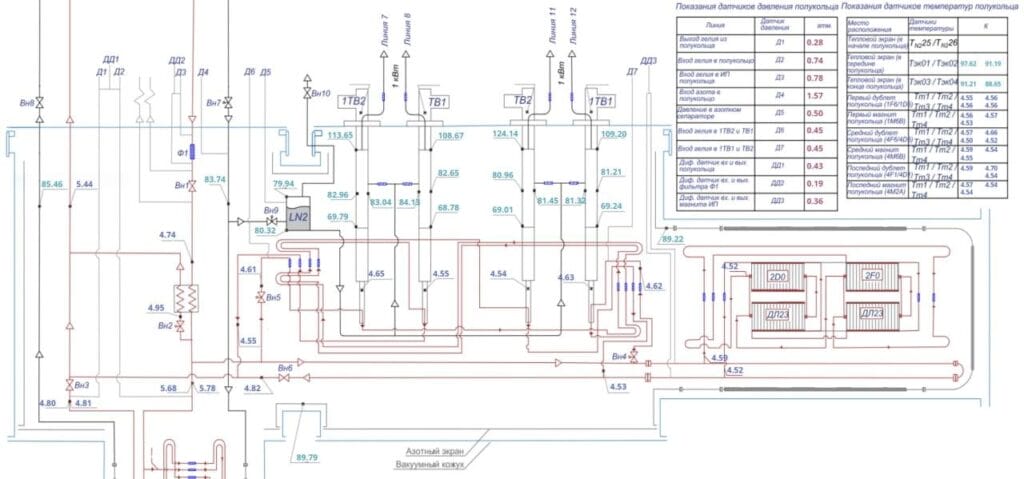
The GhostSec collective publishes screenshots of the NICA Booster control system’s nuclotron-based ion collider facility at 20:56. The facility is located in Russia and the schematics were pulled from one of the hacked institutional portals the Joint Institute for Nuclear Research. The official portal of the facility is: https://nica.jinr.ru/projects/booster.php
1 March 2022 – (6th day)
Compromise of Russian satellites by the NB65 collective
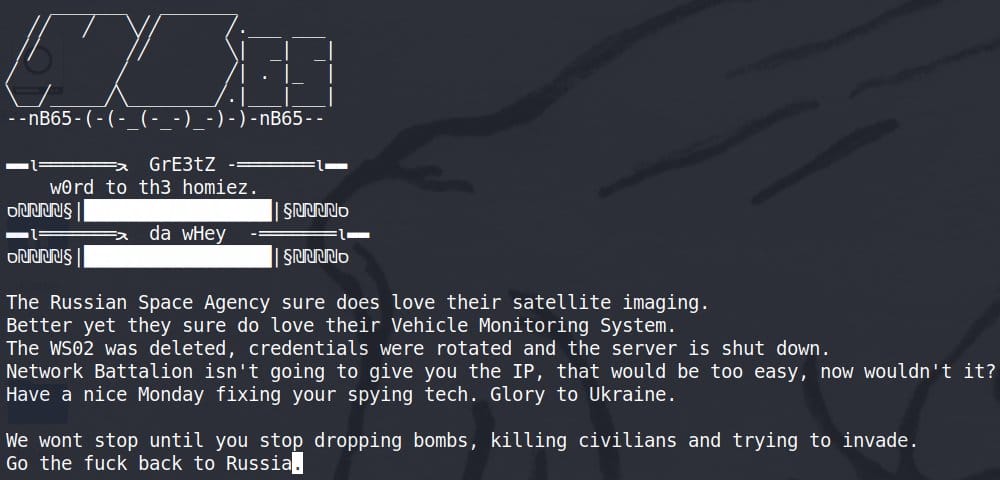
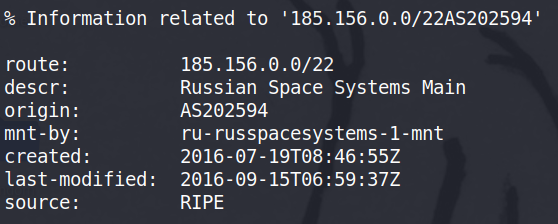
Russian Space Agency was hacked by the NB65 group, which published important findings concerning the remote control of satellites. The situation is rather bizarre because such a delicate system should not be manoeuvrable without high security measures and instead it seems that everything could be done without any particular rigidity.
The situation of the Italians

Within the social groups, there were tense moments for the Russian convoy on its way to Kiev: some parents argued about the inefficiency of the group members, forgetting that these are social groups of volunteers that have nothing to do with the activities carried out by the embassy or other institutions. These groups, in fact, existed well before the conflict between Russia and Ukraine and were used as information exchange points for anyone wishing to visit or live in Ukraine. The anxiety of the conflict, unfortunately, also generates these tensions.
Fedorov’s request to Apple Music and Spotify
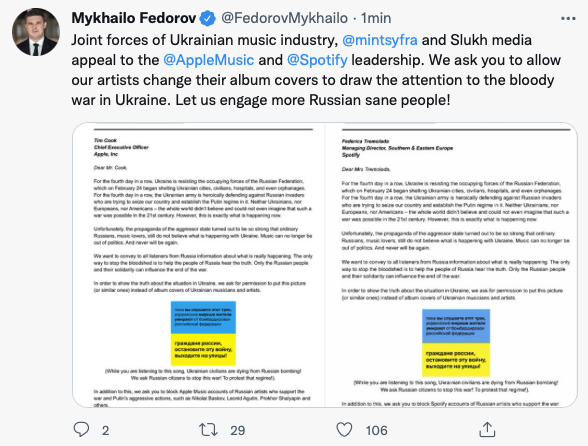
Fedorov is making himself heard again, this time involving Apple and Spotify, to whom he asks to publish an image on the Ukrainian artists and music pages. The official statement follows.


Risk of Internet connection blackout
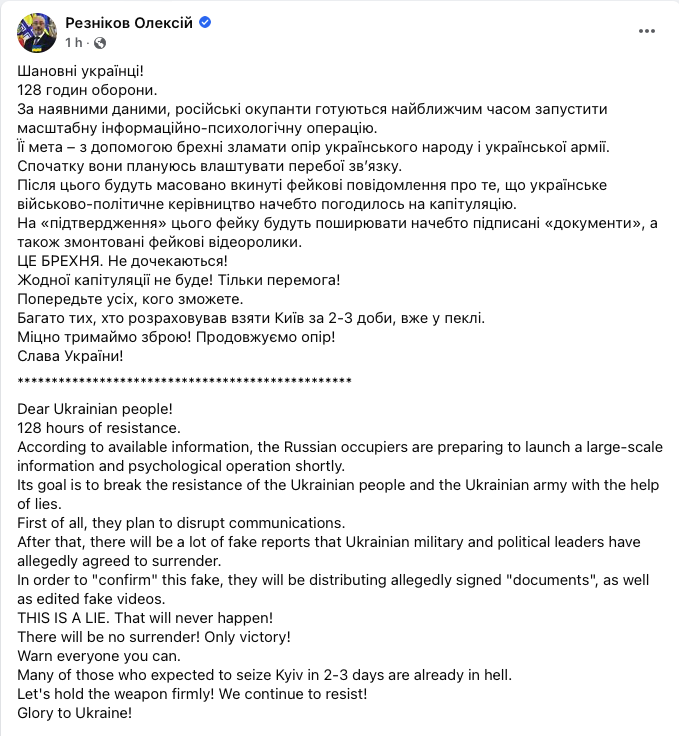
At 13:55 on 28 February 2022, on the ‘Italians in Ukraine’ group, news arrives of a potential mobile internet blackout. The news is not certain and the source comes from Ukrainian Defence Minister Oleksiy Reznikov. The blackout of mobile communications would intensify a pro-Russian propaganda activity on Ukrainian territory and the intensification of psychological operations aimed at destabilising the Ukrainian resistance.
Fedorov’s request to YouTube bloggers
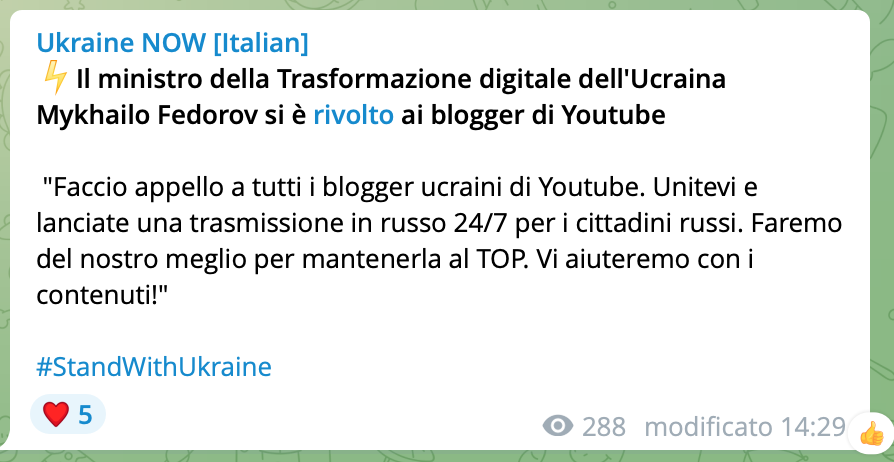
I appeal to all Ukrainian YouTube bloggers. Come together and launch a 24/7 Russian broadcast for Russian citizens. We will do our best to keep it at the TOP. We will help you with content!
The news was reported by the newspaper Ukraine NOW, which, in order to cope with the crisis, has also opened many channels in Italian.
Russian soldiers’ messages to their parents
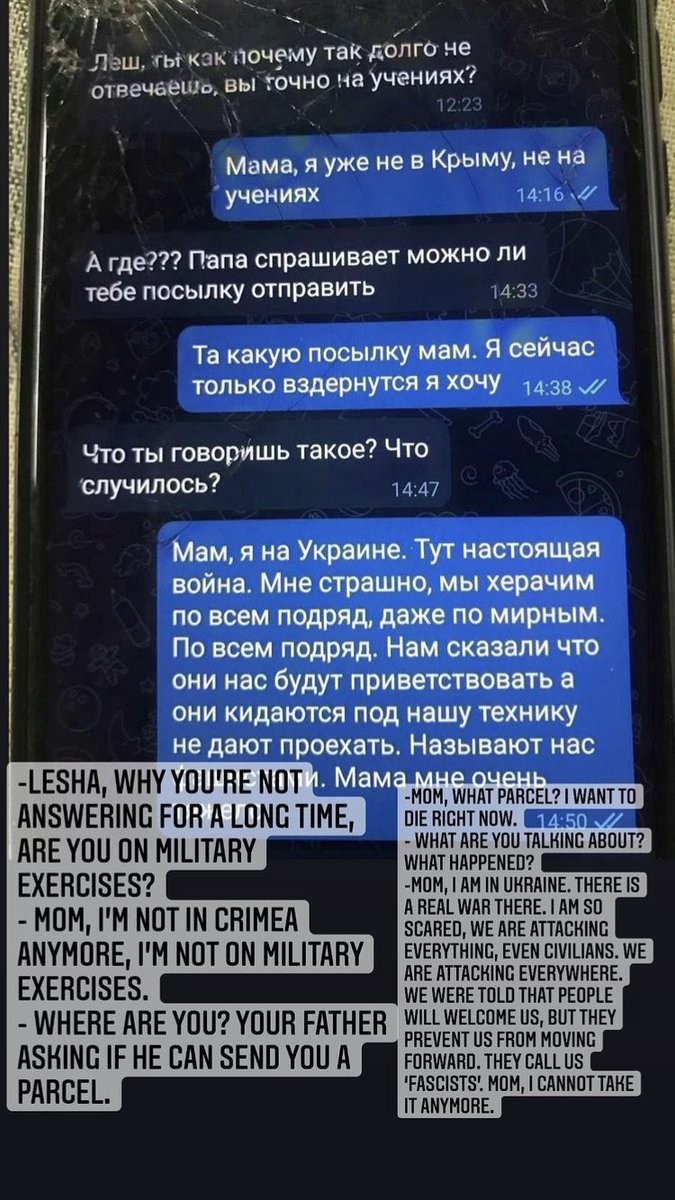
Anonymous has published screenshots of messages found on the mobile phones of Russian soldiers. These are really touching messages that would show the campaign of manipulation and disinformation carried out by Russia against these boys.
Russian armed forces hit the Kiev TV tower
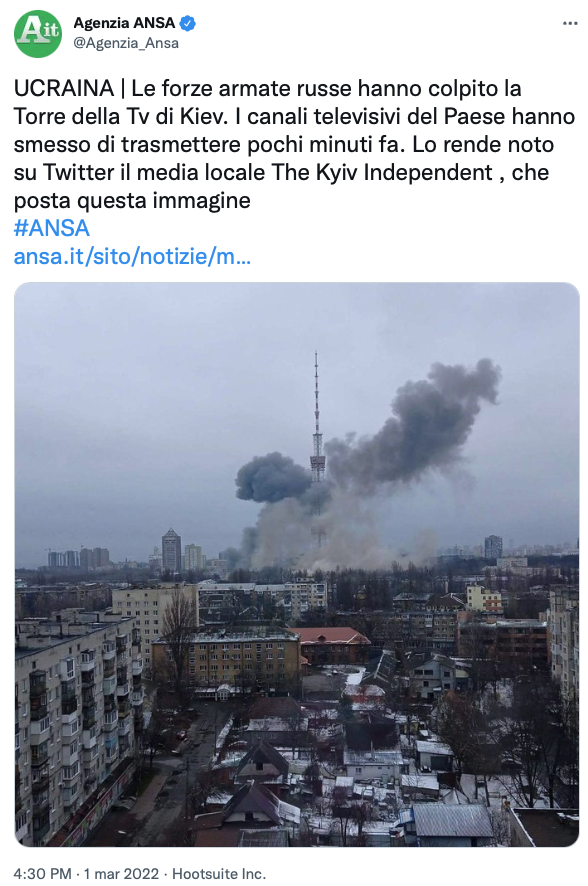
At 4:30 p.m., ANSA breaks the news of the destruction of the TV tower in Kiev, with the consequent loss of the ability to communicate to Ukrainians. This could be the beginning of that communication blackout we mentioned a few hours ago. The attack is said to have caused five deaths.
Leak Accounts
During the conflict, a news item bounced around that was later confirmed and described in a beautiful article by Raffaele Angius
A Ukrainian researcher, who infiltrated the pro-Russian cyber crime collective, leaked more than 16,000 internal and confidential messages of the gang. Meanwhile, Belarusian partisan hackers hit their country’s railway infrastructure
I highly recommend reading the article on this page.
2 March 2022 – (7th day)
The digital offensive is proceeding, but there is now a greater perceived disconnect between it and the military movements. The activities conducted by Anonymous, as well as those conducted by GhostSec, are creating not too significant problems for the Russian military troops, which are experiencing internal difficulties. The ‘DoS bombings’ carried out by the numerous volunteers registered on the IT ARMY OF UKRAINE channels continue, but the targets hit are often not up-to-date and, in general, there is a lack of more methodical coordination. Instructions on how to launch these attacks are crowded out, which, however, are not followed with potential legal consequences for users. On the other hand, the requirements needed to launch them are often beyond the reach of most. Minister Fedorov is continuing his battle on social media, demonstrating its importance and applying a strategy that is proving to be rewarding: numerous international players (of the magnitude of Sony, Apple, Google, Meta, Warner Bros, BMW, Audi) are suspending their activities, leaving Russia in a tangible commercial isolation that is damaging to the Russian economy and population. Finally, there is the propaganda that, on both sides, tries to pull the population. The Russian one based on the drawing of a completely different reality: there is no war, it is exercises, etc.. This is documented by messages on Russian mobile phones, interrogations of prisoners. On the other hand, Ukraine is appealing to a sense of freedom and national pride.
The situation of the Italians

The plight of Italians is as follows: numerous compatriots have remained in Kiev due to the impossibility of boarding trains, BlaBlaCar, Uber or other means of travel. The war is advancing day by day inside Kiev and those left behind are finding it increasingly difficult to leave the city. The embassy has been moved to Lviv and the last trips back seem to have ended yesterday. It is therefore a very complicated situation because in the next few hours fewer and fewer vehicles will be on the streets and the war will increasingly take on the appearance of a ‘door-to-door’ conflict.
Anonymous publishes Russian military address book
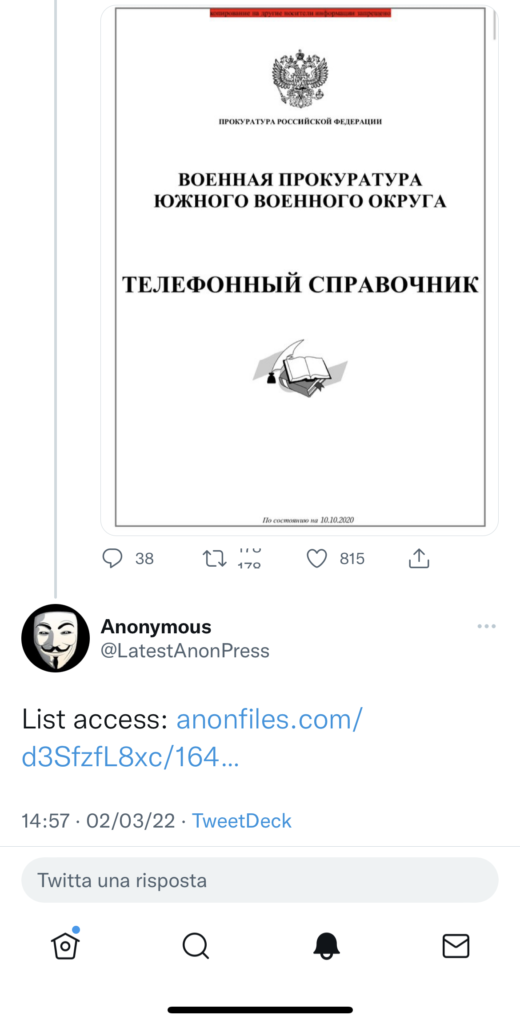
At 2.57 p.m., Anonymous publishes the Russian military address book, including all telephone numbers of the offices of the military apparatus and their extensions. The action, apparently of little value, is of particular relevance for acts of disruption and sabotage.
3 March 2022 (8th day)
The situation for Kiev is becoming more and more difficult, the cities around the capital are now subject to continuous bombardment even by thermobaric missiles. There has been an escalation of force and violence in the attacks despite some difficulties encountered by the Russian army.
Intercepted communication channels AEROFLOT, ROSGUARD and more…
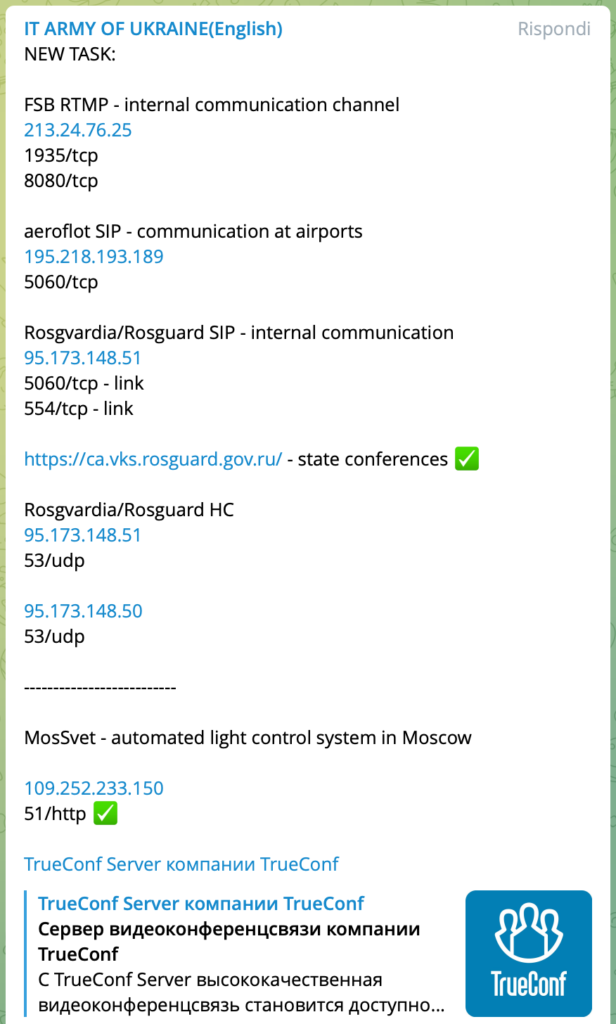
At 14:57 on 3 March, the official IT ARMY OF UKRAINE group published the addresses of some sensitive targets, such as the internal communication system of ROSGUARD’s AEROFLOT and the automated light system in Moscow. The targets, which will not be reported in this blog for obvious reasons, denote the methods and types of attack.
Elon Musk modifies StarLink to run on low power and facilitate vehicular deployment
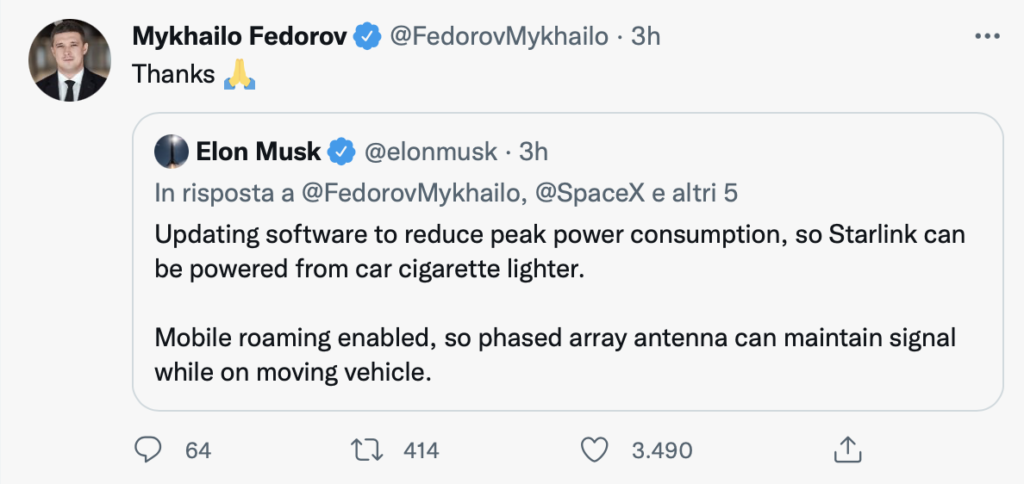
The news has some relevance. Elon Musk confirmed that changes have been made to the StarLink software to allow the antennas to operate on the voltage of a cigarette lighter socket. These sockets, which exist in all cars/jeeps/trucks, will allow Ukraine to install antennas directly on military vehicles, powering them and providing advanced connectivity. Projects of this type allow military troops to have greater control in theatre and a not inconsiderable tactical advantage.
15 May 2022
DDoS attack rejected at the Eurovision Song Contest
The group Legion attempted to attack the Eurovision Song Contest portal in order to disrupt the final competition. The postal police rejected the attack. The event was analysed in this article.
Part of the chronicle of the subsequent attacks on Italy are contained in the article.
19 September 2022
Wagner group hacked by Ukrainian technicians
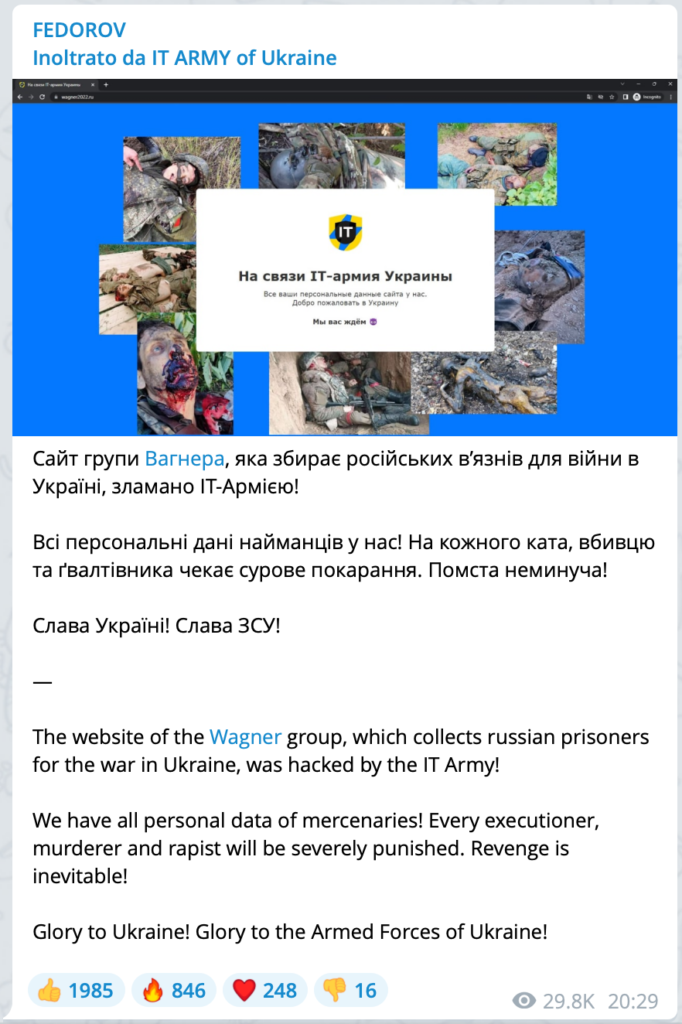
The cyber army of Ukraine obtained all personal data of the mercenaries of the private (Russian) military company Wagner by hacking their website. We have all the personal data of the mercenaries! Every perpetrator, murderer and rapist will face severe punishment. Revenge is inevitable!
Mykhailo Fedorov
21 September 2022
Amazon removes taxes from Ukrainian sellers for one year

Fedorov, this morning, posted a message on Telegram about the fact that Amazon had waived taxes for Ukrainian sellers for a year to help them with their business. The message posted Fedorov was in Ukrainian, the automatically translated content is reproduced.
Amazon cancels commission for Ukrainian entrepreneurs for a year! A few months ago, together with Ukrposhta, Disqover Agency and Startup Ukraine, they appealed to Amazon for the company to ease conditions for Ukrainian companies, which, despite the war, continue to work, supporting the country’s economy. As a result, Amazon cancelled the referral fee for Ukrainian entrepreneurs for a period of 1 year. That is, it completely cancelled the commission for Ukrainian entrepreneurs selling to the EU and Great Britain. Ukrainian entrepreneurs will be able to expand more actively into European and world markets, find new customers there. This will be a powerful boost to popularise Ukraine and our activities abroad. The new conditions for Ukrainian entrepreneurs are a victory on the economic front. Thank you for your constant and consistent support for Ukraine. Amazon, together with Amazon Web Services, provided us with the capacity to store backup logs, provided over $35 million in support, and eventually deservedly received the Peace Prize from President Volodymyr Zelenskyi.
Conclusions
In this chronicle of the first eight days of the war, the scenario that unfolded was terrifying. From a social point of view, Kiev and the cities of Ukraine were plunged in just 48 hours into a nightmare they never thought they would see.
Gone is the illusion that peace is a foregone conclusion
Mario Draghi
From an IT point of view, however, the situation has been widely heralded. Over the past five years, insiders have seen an increasingly shrewd Russia: from the attempted sabotage of the US presidential elections, to the relentless harbouring of the most effective hacker groups. It was clear that these manoeuvres tended towards something and that that ‘something’ would not be peaceful. The frictions that became evident between the U.S. and Russia should have raised the perplexity of Europe, which, somewhat reminiscent of what happened before World War II, stood by and watched. Perhaps energy dependence, perhaps diplomatic agreements, but the effect has been to be faced with a monstrous, inhuman, anti-democratic response that could have been mitigated yesterday and is now being dealt with in all its fury.
As this conclusion is being written, on Telegram groups and on the net, the battle of sabotage, of propaganda and counter-propaganda, of the DoS and the Wiper continues, but unfortunately, above all, the battle of the thermobaric missiles, of the dead, of the children and parents who remain isolated, and the war unfolds in all its madness, a monstrous madness.
Updates
28 June 2023
CyberCat attacks the Italian Ministry of Infrastructure and Transport
After many months in which Italy was the victim (like other countries) of DDoS attacks, there was an attack on the Ministry of Infrastructure and Transport. The attack was carried out using ransomware with an e-mail vector. Wired magazine published an editorial on the incident:
The group, which allegedly acted at the hands of a user calling himself Ekwa23, announced the operation on Telegram
Source: Wired
The attack was successful, documents and e-mails were stolen. A series of messages containing evidence of the attack followed on Telegram, as well as messages mocking the ministry.
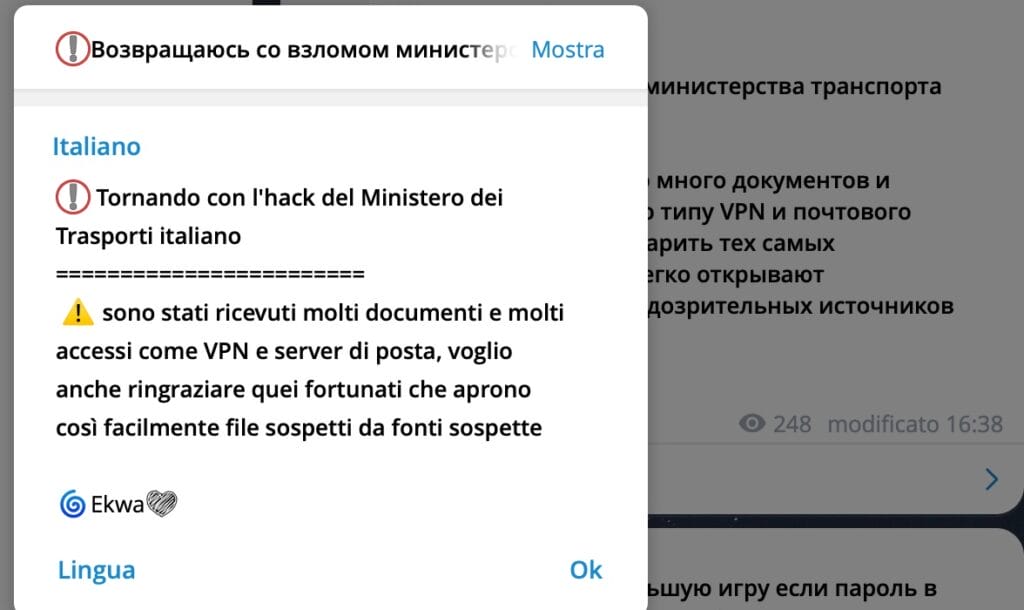
I also want to thank those lucky people who so easily open suspicious files from suspicious sources.
Ekwa
This sentence is at the heart of the main problem of cyber attacks based on corrupt e-mails and attachments.
02 July 2023
CyberCat and EKWA make a video discussing the MIT attack
On 2 July at 15:20, CyberCat published a Telegram message whose text was interesting:
Today our guest is the head of the hacker group CyberCat (https://t.me/CyberCatHack), the hacker Lucky (https://t.me/CyberCatHack) and (https://t.me/CyberCatHack)Ekwa (https://t.me/CyberCatHack) hackers. We discussed their attacks on Italy, the arrest of Russian hackers and also talked about computer security.
Source: CyberCat
Attached to the message is a video which, for reasons of preservation, is uploaded directly.

