A few days ago, on Telegram, the group NoName057 (known in Italy and worldwide for DDoS attacks) posted a message about biometrics that deserves to be analysed.
Biometrics according to NoName057
On 15/03/2023 at 18:00:40 CET, the hacker group NoName057 published a post that deserves reflection and that concerns the use of biometrics as a means of security to access portals, systems, services, etc.. Here is the message in the original language and, below, the Italian translation made with Google Translate.

Biometrics has recently been used in financial transactions as an additional way to protect data and a trivial security measure. However, nothing is perfect. And the imperfections of this technology have naturally attracted the attention of attackers. Fraudsters look for photos, videos and audio recordings of their victims to trick the biometric systems with their help. In most cases, the data needed for the scam is stolen by the fraudsters through phone calls (in which the attackers want to obtain clear recordings of a series of phrases they need) and through the theft of photos from your social network pages. How to avoid it? It is categorically impossible to use biometrics as your main method of identification. At most, do what has been said many times before: do not disperse your photos, audio recordings and other materials useful to criminals.
Source: NoName057
What is biometrics
Biometrics is the‘discipline that studies biophysical quantities in order to identify their mechanisms of operation, measure their value and induce desired behaviour in specific technological systems‘. In a more exemplified way, we have to consider that our bodies have individual characteristics that are unique compared to those of all other human beings on the planet. Some of these characteristics are:
- The fingerprint
- The conformation of the skull
- Venous conformation
- The voice (timbre and tonality)
In the case of the voice, for example, what makes timbre and pitch unique is the conformation of our internal organs that allow the air to vibrate the vocal cords and the oral and nasal cavities to bring out the sound in a unique way. The problem is that some biometric elements are, as of today, in the public domain and could be used to force security systems using these parameters. One must therefore question how true NoName057’s assertion is.
At most, do what has been said many times before: do not disperse your photos, audio recordings and other materials useful to criminals.
The concept of security
The sentence of NoName057 is fundamentally correct. However, an important concept must be considered: a complex password, in itself, is only secure if it is kept confidential. If a password, no matter how complex, were made public and disclosed, its integrity would be compromised. If the password were the voice, one would need to protect it from being shared without control. A sentence in the article‘Biometric Recognition: Challenges and Opportunities‘ published by the National Library of Medicine is very interesting:
Biometric systems assume and require an intimate relationship between people and the technologies that collect and record the biological and behavioural characteristics of their bodies.
Source: Biometric Recognition: Challenges and Opportunities
The choice of the term‘intimate‘ is interesting, as it represents something particularly confidential and personal. Certainly biometric systems are based on extremely complex processing: it should not be possible to unlock a facial recognition by framing a printed photo, but there are many cases of concern about an illicit use of biometrics. It is worth mentioning at this point the ICO’s intervention on fingerprints acquired from photos.
For example, it is possible to use high resolution cameras to capture fingerprints remotely.
Source: ‘Biometric Insight’, ICO, 2022, Pg. 6
Fingerprints and forgeries
The most striking example of this is the experiment carried out by security researcher Jan Krissler who, starting with a photo of President Ursula von der Leyen’s fingerprint, managed to reconstruct the entire fingerprint. There is an interesting article in The Guardian:
A speaker at the Chaos Communication Congress, an annual meeting of hackers in Germany, demonstrated his method for forging fingerprints using only a few high-definition photographs of his target, German Defence Minister Ursula von der Leyen […] used commercial software called VeriFinger and several close-up photos of von der Leyen, including one taken from a press release issued by his own office and another taken by himself at a distance of three metres, to reverse-engineer the fingerprint.
Source: The Guardian

Below is an animation explaining, in broad terms, how fingerprint recognition takes place.
Starting with a scan of the finger, the image is reduced to greyscale and the infrared locates the characteristic cavities of the veins. A skeleton map of the ‘vein network’ is then created and minutiae are identified as characterising elements of the network.
The issue of biometric data retention
Firstly, biometric data are often stored by third-party providers. The point here is that a third party is, in effect, an individual or a company in charge of providing consumer services on behalf of another organisation. This means that biometric data may be stored by many different organisations and, in some cases, their security may have a weakness that is an invitation for hackers.
Source: ElectroPages
Some of these third parties, inter alia, may be in possession of some biometric data without treating them as such.
The question of the immutability of security
ElectroPages makes a well-known but important point: when a password is thought to be compromised, the first thing that is done is to change it to a new, more complex version. In biometrics, this is impossible in certain situations. Take the case of the human eye and the fingerprint: the iris has 250 unique recognition points, compared to 45 for the fingerprint. Nevertheless, if it were compromised, it would not be possible to change this mapping because it would be unthinkable to change the conformation of the eye. This should make one think about the concept of preserving such important information.
Voice recognition and fakes
Biometrics offers undoubted advantages over other security mechanisms: in many cases reduced costs and better levels of protection. Voice biometric recognition is not without its problems, although it has a very high reliability: in an article by Paul Korzeniowski entitled ‘Voice Biometrics Are Not 100 Percent Foolproof, but Steadily Improving’ there is a quote from Brett Beranek, vice president and general manager of Nuance Communications. Nuance Communications has been one of the leaders in the voice recognition industry for years and was one of the first companies to tackle the most common problems in the voice identification process.
If a person has laryngitis, the voice biometric system will have trouble matching the voiceprint.
Source: Brett Beranek
Obviously, we are talking about problems that will be refined over time until they almost disappear, reducing false negatives and providing increasingly precise answers, but as precision technologies evolve, so will the corruption of information.
OCTAVE Project
In 2015, a project under the European Horizon 2020 projects started under the title‘Objective Controlof TAlker VErification‘, hence the acronym O.C.TA.VE. The duration of the project was about 26 months and among the documents produced was one of particular interest, namely D54 ‘Suitability of existing voice biometric engines’. The document can be downloaded directly from the European site by clicking here.
As part of that project, many elements of vocal imprint corruption/alteration were examined, including ageing(aging). The phenomenon is interesting because it is physiological and is unstoppable: ageing, in fact, radically changes the conformation of the body, the organs, and thus constantly affects the vocal imprint. As the subject’s age increases, the fundamental vocal frequency decreases.
False audio and artificial intelligence
The most discussed case is, of course, that of audio deepfakes. These are audio messages produced through the use of artificial intelligence and the subject’s original audio files. Artificial intelligence is able to acquire voice characteristics from audio files and resample this voice so that the subject can say concepts that he or she has never actually expressed. Audio deepfakes are particularly reliable but not infallible and their detection depends very much on the reliability of the voice recognition system. In voice sampling, in fact, there is a process called ‘vocal tract analysis’ that is able to return essential information such as the shape of the vocal cords and mouth. Vocal tract refers to that part of our apparatus that includes the throat from the larynx (where sound is generated), the nose and the mouth (where sound takes shape and is amplified). This is a particularly complex process that makes use of very high quality microphones, together with specialised software. It is this software that provides the most relevant physical characteristics such as the length and shape of the vocal cords, the position and shape of the tongue and the shape of the mouth. For example, if an individual has a larger tongue, there may be variations in the pronunciation of certain words that the speech recognition software can detect.
Related techniques such as the one reported by Cambridge University and entitled‘Advances in real-time magnetic resonance imaging of the vocal tract for speech science and technology research‘ are also recommended for further investigation. It is therefore not so easy to carry out false audio as long as the voice recognition system has the right quality to guarantee the right reliability. On the Internet, there is a lot of software (for commercial use but also free of charge) for carrying out vocal tract recognition:
- Praat: is a free and open-source software for acoustic sound analysis, including vocal tract analysis. It was developed by Paul Boersma and David Weenink.
- Wavesurfer: another free and open-source sound analysis software that includes vocal tract analysis capabilities.
- Vocalize.ai: a commercial voice analysis software that uses vocal tract analysis to create speech recognition models.
Iris and blood system: the multimodal approach
In many case studies, biometric aspects are adopted following a multimodal approach: this is the case, for example, of the iris, accompanied by the scanning of finger veins or the palm of the hand. An important clarification must be made at this point: in the human body, the position of the veins is known but is not identical in all living beings. The vein network follows a macro-path but extends seemingly randomly from individual to individual, following tissue morphology and creating a unique ‘map’.
The multi-modal approach consists of combining two highly reliable biometric recognition systems such as iris and palm, both based on complexity. There is an interesting article in the ‘International Journal of Intelligent Computing and Information Science’ in which the following sentence is quoted that can clarify this phenomenon very well:
Finger veins are subcutaneous structures that randomly develop into a network and spread a long a
finger.
The multi-modal approach is necessary to drastically reduce false-positives without sacrificing the analytical complexity required and desired by biometrics systems. Furthermore, the use of the venous system of the hands or fingers is considered an optimal means of verification because it is minimally invasive and even less falsifiable. One must bear in mind that the palm of the hand has a limited thickness and when the infrared rays pass through the surface of the skin, they do not encounter large bony or muscular masses to disturb the signal. The map will therefore be sharp and adequately complex.
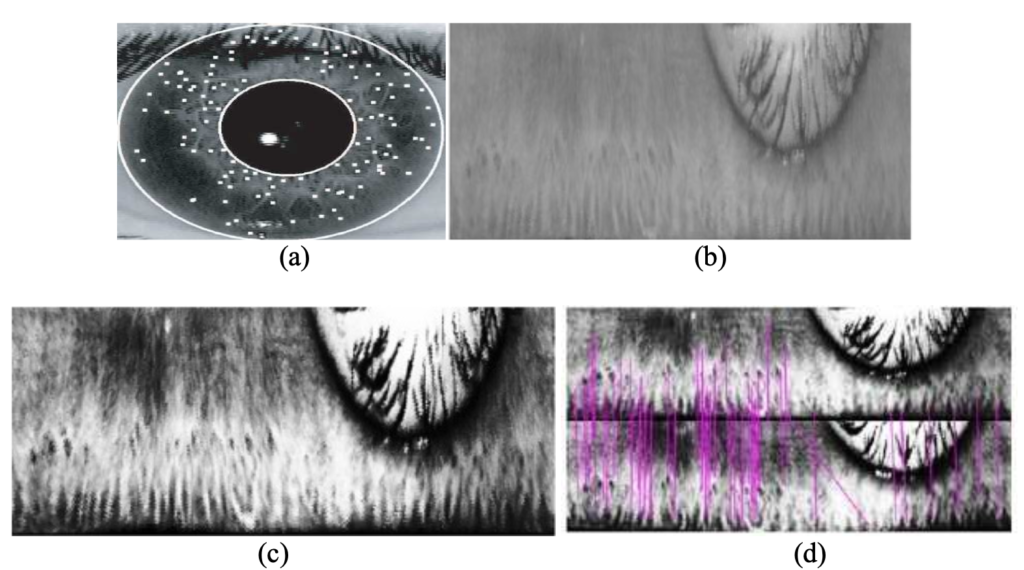
As far as the iris is concerned, however, the model proposed in the above-mentioned article has four basic stages:
(a) identification of the pupil, dilation state and iris.
(b) normalisation of the image to be acquired.
(c) contrast enhancement of the acquired image to bring out the venous pattern.
(d) comparison of the acquired image with the one originally recorded.
Conclusions
Starting from the sentence published by the hacker group NoName057, an attempt was made to demonstrate how sharing information related to biometrics can affect the reliability of biometrics. Examples and references to academic texts have been given that can help the reader to better understand the advantages and disadvantages of biometrics. However, one essential concept remains well understood: everything related to security should have a very limited sharing. This is precisely to avoid a paradoxical phenomenon whereby the key needed to unlock information is actually available to everyone. In the age of mass sharing, this could represent one of the most serious problems to the adoption of such systems and is primarily a problem of both cultural and technological origin.

