On 15 August 2023, the Medusa Group published a ransom note on its website demanding payment of $500,000 from Postel SpA for not publishing the data. At the time of writing this article, the situation is in flux.
About Postel S.p.A.
Postel S.p.A. is the company that is part of the Poste Italiane Group specialising in printing services, document management and data-driven marketing communications for businesses and public administration. At the time of writing of this article the main offices are occupied by the following names:
Chairman: Giovanni Ialongo
CEO: Giovanni Fantasia
Directors: Maria Elena Bisogni; Enrica Fabrizio; Guido Crozzoli
The statutes of Postel S.p.A. can be found by clicking on the file below.
What allegedly happened and the inconsistencies
Postel SpA was allegedly the subject of a data breach following a ransomware infection by the Medusa gang; this is essentially what can be deduced from the announcement officially published on the portal of the hacker collective. However, there are inconsistencies between the material published by the Medusa gang and the information reported.
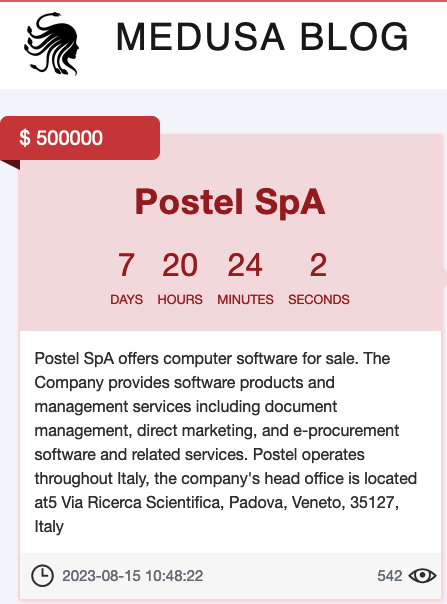
The location-related inconsistency
The Medusa Group’s official announcement claims to have hit Postel SpA with its head office in Padua, but this cannot be true: the company Postel SpA has its head office in Rome, while the address of Via Ricerca Scientifica 5, Padua corresponds to an office of Poste Italiane.

For the sake of completeness, it should be pointed out that the Postel SpA group has two locations:
- Registered Office: Viale Europa, 175 – 00144 Rome (RM)
- Branch Office: Via Pionieri ed Aviatori d’Italia, 111-16154 Genova
The inconsistency in the location is important to understand who was really affected by the data breach.
Portal unavailability but no official announcement
On 15 August, the Postel SpA portal was not reachable for a few hours, and many users on Twitter reported this. The Red Hot Cyber portal published an article (by Chiara Nardini) which we recommend you read. Nardini carried out a check on the availability of the postel.it site, which was reported to be unreachable.
At the time of writing, Postel’s site – as we reported at the beginning of the article – is unreachable, as reported by the analysis carried out via checkhost at 22:45 on 15/08/2023.
Source: Red Hot Cyber
The portal became available again on 16 August 2023 at around 15:00 hours, but without any official warning about the possible hacker attack.
AgID’s confirmation
A number of users tweeted the news, including security researcher Claudio Sono, who obtained a response to his tweet from AgID.
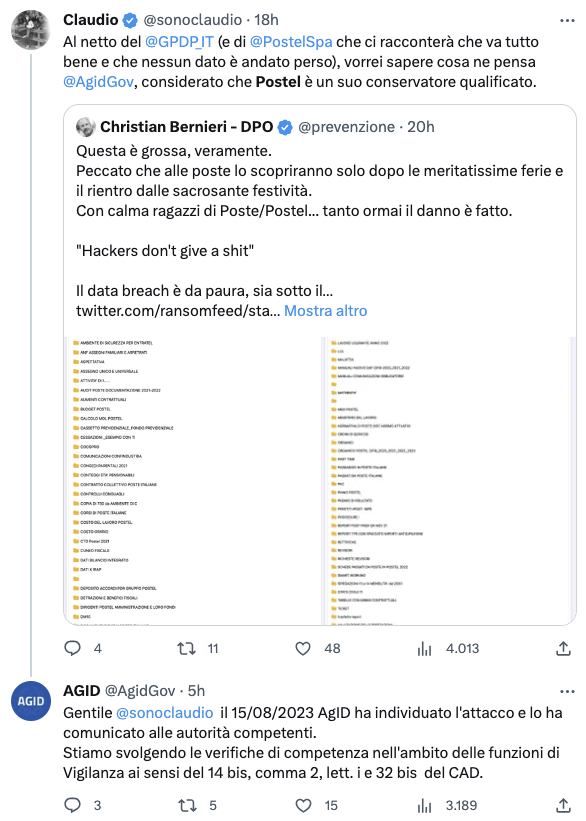
AgID’s response is important and provides further confirmation of the event, however, Postel’s official blog, as of the current date (16 August 2023 at 17:30), does not report any information on the matter.
Stolen documents
In the stolen material can be found:
- identity documents (identity cards, passports),
- certificates of competence,
- purchase receipts,
- emails with internal communications,
- documents on legal disputes,
- files containing PEC and portal passwords,
- disability certificates required for the employment of disabled employees,
- registration certificates for motorbikes,
- medical certificates and much more,
- complaints (for mobbing, accidents, etc.),
- training material (including cybersecurity material).
There is also the opportunity to get an insight into some of the group’s customers and the commercial offers they have received.
In some cases, personal data of employees that could be of interest to persons outside Postel were stored: for example, birth and residence certificates as well as histological examinations and documents related to tax returns. Personal documents often concern employees’ family members. Below is an example of files appropriately changed to maintain the anonymity of those concerned:
\Personal Identity Documents/Mom Front.jpg \Personal Identity Documents Mum back.jpg \Personal Identity Documents: IMU deposit payment.pdf \Personal Documents Taxes F24 copy.pdf \Medical Examination and Histological Examination.pdf
With regard to the presence of personal data on company systems, it should be explained that it is almost physiological. In offices one normally works 8 hours during the day, during which one also has to solve some personal problems. For this reason it is not surprising that employees have left non-work-related documents on the systems of Postel SpA. Incidentally, there is often a perception that workplace computer systems are more secure than home systems.
File Origin Considerations
Many documents come from the archives of Postel employees, e.g. an employee of the Legal Affairs area of the Genoa head office, but also an employee of the E-procurement Services Management also of the Genoa head office, but also archives of ‘decommissioned’ users, as can be seen from the list of stolen files.
The file path in the list deserves some thought. Generally, a databreach affecting one or more users has, as a path, username/folder/… for example the path could be:
Users\name.surname\Download\2022\nomedelfile.docx
However, the structure of this file list is slightly different, which raises the question as to which system was attacked and, consequently, what the access credentials of the person who was the victim of the ransomware were. The structure is as follows:
Main_Group\Finance\subfolders... Main_Group/Fiscal... Main_Users\surname.surname\subfolder...
However, the following path appears in the list at some point
Main_Users\Disconnected Users\First Name
The fact that one had access to all folders could indicate (but this is in the realm of hypothesis) that there was no access segmentation for users accessing the data repository: this means that anyone accessing the repository could indiscriminately go to the Main_Group part, as well as the Main_Users part, and read everyone’s files. This should not normally be possible.
Another possibility (but again, we are in the realm of hypotheses) is that the infection was transmitted from a domain client to a server domain controller that was not properly configured and protected, and that this allowed information to be exfiltrated from the systems.
Conclusions
On the surface, the Postel case is yet another successful data breach, but to classify it in this way would be to overlook certain aspects that instead deserve reflection and, for this reason, it is important (and right) to detail these conclusions a little more. The data breach at Postel is a story of failure in external and internal communication: there were delays, inaccuracies, approximations that should not have been there.
The data breach at Postel is a partial success story, because the stolen data were rendered inaccessible but were also restored, which means that the damage was not completely devastating. One must objectively recognise that it could have been even worse, and if it did not go that way, it is because ‘someone’ designed ‘something’ that worked, even if not entirely. The data breach at Postel is an employee story about which little has been said, and perhaps badly: with approximation. Someone merely wrote that they should not keep personal files on company systems as if that were the problem.
Certainly there was a problem with internal and external communication: communication is essential. One must be clear, not dramatise or exaggerate. Do not engage in psychological terrorism in press releases, but this does not only apply to Postel, it applies to everyone and it applies especially to editorials written with the aim of getting clicks and selling advertising. Articles with sensationalist headlines written irresponsibly without thinking about the consequences they might have on customers and employees. Communication is important: choosing the right sources of communication is crucial and it is the responsibility of us outside professionals to avoid giving in to controversy or dramatisation of facts.
Then there is the problem with social networks that have become a concentrate of everything and nothing: where a perfect stranger, who does something else in life, goes from being the ultimate expert on football, to being the ultimate expert on computer security. He writes nonsensical tweets about attack techniques that are neither in heaven nor on earth, and while experts ignore him, other less experienced people convince themselves that he may even be right.
There are several conclusions that can be drawn in this matter:
- Organisations must learn to truly communicate both internally and externally. Understand that employees are the strength of the company and deserve proper respect with complete and truly transparent communication.
- Sources of information should be chosen carefully, neglecting sensationalist headlines and choosing the most aseptic and correct ones. Communication is essential in times of crisis; it can make the difference between a good reaction and a negative one.
- Infallibility in life does not exist, let alone in IT: it is important to learn to act in a timely and organised manner, because the consequences could spiral out of control. Staff training is essential.
To Postel S.p.A. the wish to rise from this situation as soon as possible, learning from its mistakes. To us outsiders the wish to continue to do our work better and better and in an ever more punctual and respectful manner, remembering a phrase by Henry Ford: only he who does not dare, does not err.
Updates
16/08/2023-Portal unreachable
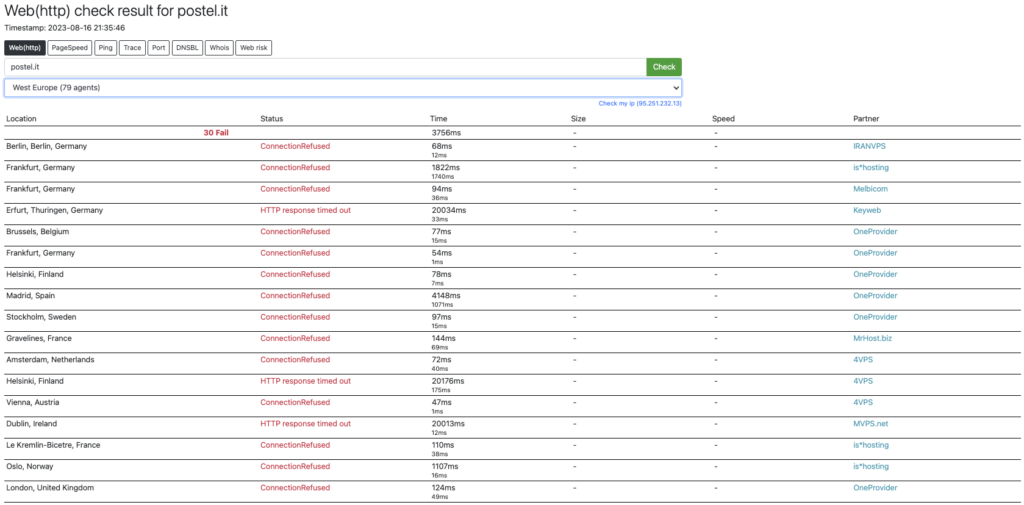
At 9.35 p.m., www.postel.it was not reachable either from Italy or from other countries.
17/08/2023-Portal reachable again
At 08:40, the portal postel.it became reachable again after more than 10 hours of unavailability, although not for all countries. However, despite the resumption of service, there were several moments when the portal was unreachable.
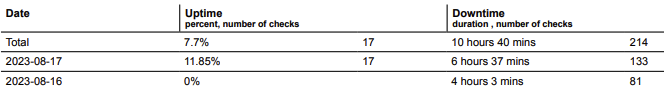
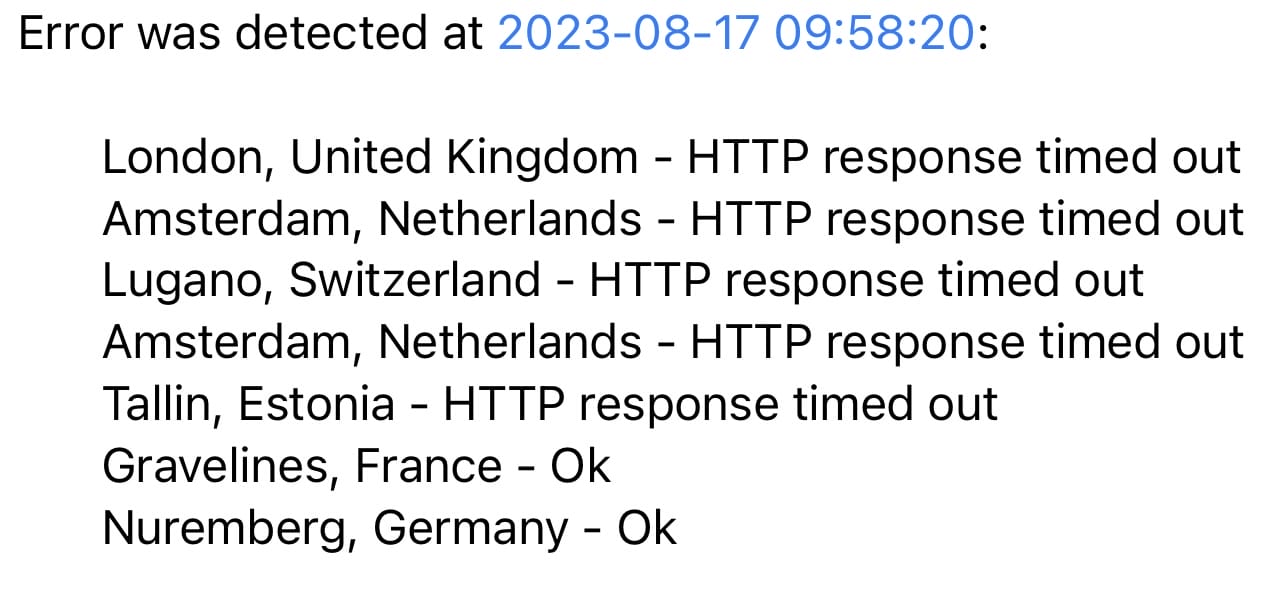
There is still no information about the hacker attack on the portal, neither on the home page, nor on the blog, nor on Twitter.

18/08/2023-The press release of Postel S.p.A.
Today, the Postel S.p.A. Group published a much-discussed communiqué on the Internet. The text is reproduced in full below.

The company Postel S.p.A. identified anomalous activity on its systems, which could be attributed to an unauthorised external actor. The company therefore precautionarily stopped production activities and the operation of some servers, as well as some workstations distributed throughout the country. In the face of the anomalous activities, the necessary verification activities were promptly started, in order to identify the potential impacts on the systems and undertake the appropriate and consequent mitigation and restoration of operations. On 15 August 2023, the criminal group Medusa claimed these activities, publishing on its blog the news of a ransomware attack carried out on Postel S.p.A.’s systems. At present, only internal company data appear to have been affected. The company has already partially restored services and is working to quickly complete the full restoration of systems. In addition, the complete availability of the systems’ backup archives has already been verified, which will allow a complete recovery action. It should be noted that, at present, some systems have been partially restored, in particular business-critical systems. The removal of the malicious actor from Postel’s systems took place promptly close to the detection of the anomalous activities themselves. If there are further updates, we will keep all stakeholders informed of the information needed to protect their interests.
The communiqué has been the subject of much criticism, one of the most interesting being that of DPO Christian Bernieri on Twitter. Bernieri writes something important in his Tweet:
The real problem, which is not even mentioned, is the fact that THE DATA WERE COPIED, THAT THEY ARE NOW IN THE FULL AVAILABILITY OF CRIMINALS AND THAT THEY WILL CERTAINLY BE PUBLISHED AND FREELY ACCESSIBLE WITHIN A FEW DAYS. Usually something else happens as well. That data will be used directly by the same criminals who stole it for targeted, highly personalised and effective activities: attacks, scams, identity theft, extortion and whatever else the worst human mind can come up with.
Bernieri is right: the problem is that the data has been copied, that there is probably more than just employee data among them, and that the nature of this data includes special category data. It is serious that there is no clear mention of this in the communiqué.
22/08/2023 – Possible presence of corrupted files in archives
There is about one day and 18 hours to go before the data is published, and it is important to note that some files in the CSV list may have been corrupted during the exfiltration. Looking at the list, there are files that do not have the size, and going through the folders published by the hackers, such files would appear to weigh 0 KB. An example is given below.
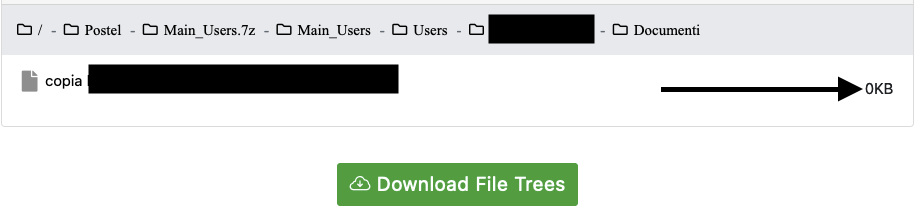
It should be noted that in order to be completely sure of this figure, a sample check of those files would have to be carried out: there would be 6646 files with no indication of space and which could be corrupt.
22/08/2023 – Internal communication from Postel to employees
On 22 August, the internal communication to the employees of Postel S.p.A. was published. The communication came in for a lot of criticism because it was considered too general, possibilistic and not very clear.


Without prejudice to the intention not to create controversy on a delicate subject on which there are already many discussions going on(I would like to point out the one on Twitter byLawyer Bernieri), it is necessary to clarify a few things regarding this way of communicating: it is good to say that the employees of an organisation must be fully and simply aware of what happened and analysing the text it is possible to note a few phrases that it would have been better to avoid or correct.
Unfortunately, it turned out that the criminal group responsible for the incident itself had allegedly managed to steal computer documents containing personal data relating to employees and collaborators of the company.
This information is not presumed(probable), it is as certain as the lists of files and folders published on the portal are certain: the data related to activities with customers also concern them and customers are not employees of the company; suppliers may be, but not customers.
In any case, the Company has already taken steps to mitigate the consequences of the event, promptly removing the malicious actor from its information systems, as well as implementing organisational and technical measures to isolate the incident and restore the systems’ functionality.
There was no prompt ouster. The infection occurred, the data was exfiltrated and made unavailable through encryption by the hacker collective Medusa. Prompt exfiltration would have prevented the occurrence. Prompt exfiltration would have prevented the exfiltration of the files, and more generally the occurrence of the data breach.
Therefore, it is best to avoid providing personal data, especially banking data, through such channels; if you receive suspicious messages, do not click on the links they contain and do not open any attachments, which could contain viruses or Trojan horses capable of taking control of PCs and smartphones. Often, links to unsafe content are hidden behind the names of apparently safe sites.
This phrase may be exaggerated and the risk is to make less experienced users overly concerned. It is also worth mentioning that in the GDPR there is Article 12 that deals with ‘Transparent information, communication and modalities for the exercise of the data subject’s rights’.
24/08/2023 – Publication of data
Today, 24 August 2023, is the day of Medusa’s data release. This blog will not publish documents about the evidence but will merely confirm its actual public release. In the meantime, an interesting thing is noted. In the course of these days, Medusa has made a correction to Postel’s description. The differences are reported.

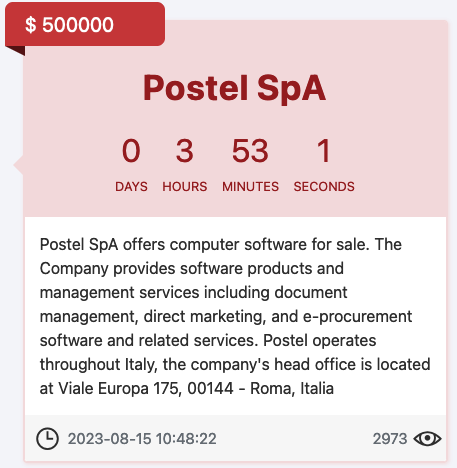
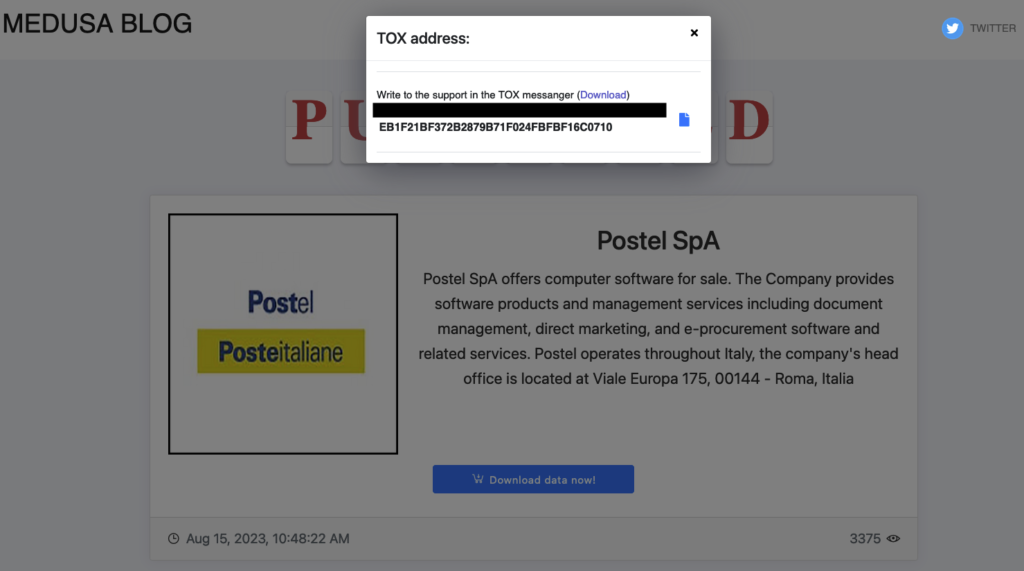
At 14:09, Postel S.p.A.’s files are theoretically free but, in fact, it is necessary to acquire Tox Chat and enter the identifier that the hackers provide. Tox is an encrypted messaging system for secure communications.
30/08/2023-Disclosure of data via Telegram
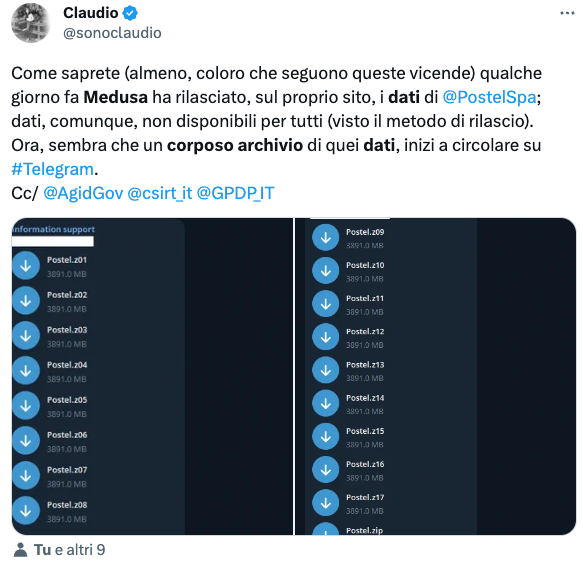
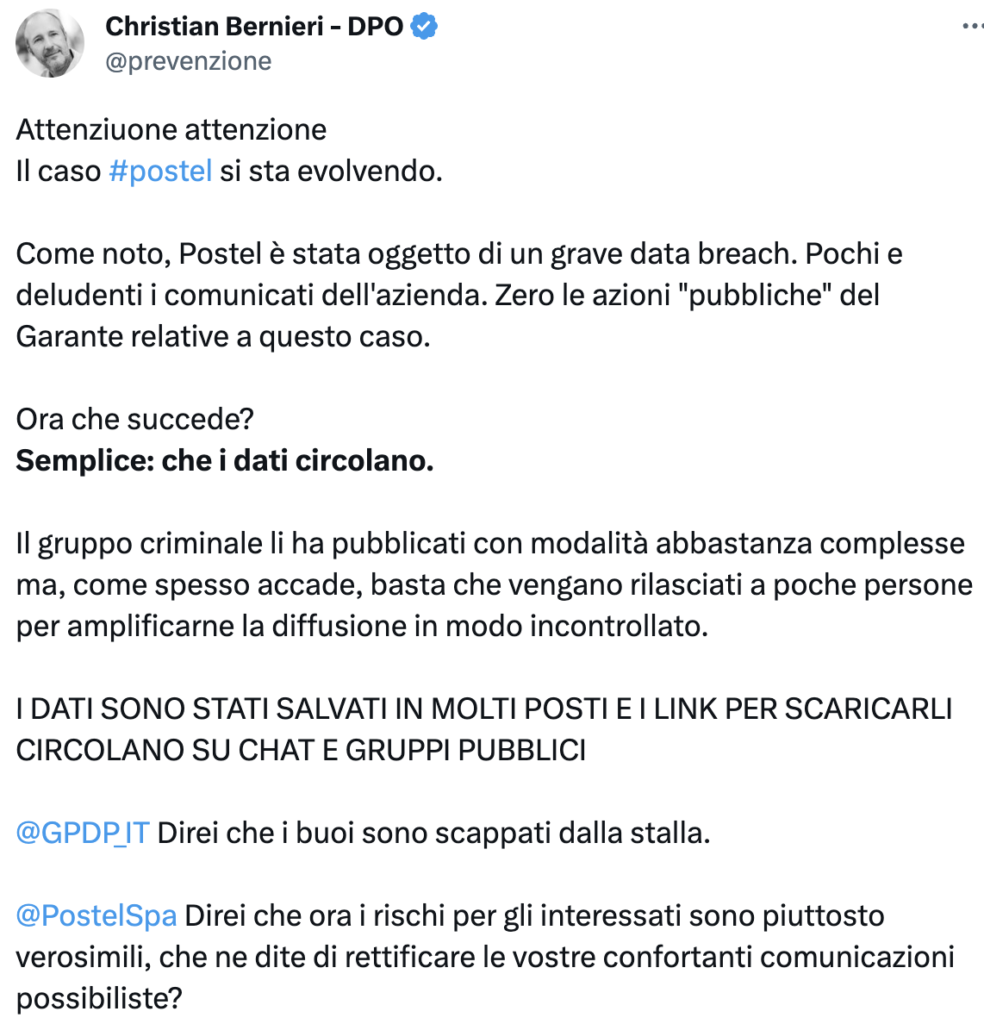
From a tweet by Claudio Sono we learn that the archives that the Medusa collective released ‘in a controlled manner’ could be circulating within Telegram groups. Rightly so, as DPO Christian Bernieri also points out on Twitter, the company should update the communication previously made to employees.