It is a term little known to the uninitiated, but dwell time is perhaps one of the most important elements to know for those working in cybersecurity.
What is dwell time in cybersecurity
The English term dwell time literally means dwell time or more correctly dwell time (the word dwell means to stay). It is therefore a generic term that can be used in various operational fields such as, for example, in marketing strategies and cybersecurity.
In the field of cybersecurity (or cybersecurity as per EU Directive 2022/2555), the term dwell time is fundamental and identifies the time interval between the infection of a system by a threat, to its actual detection. The security company Checkpoint has provided a useful definition of dwell time, describing it as follows:
Attack dwell time, the interval between an initial breach and its detection, is a crucial metric in cybersecurity. The longer attackers go undetected, the more damage they can inflict.
Attack dwell time, the interval between an initial breach and its detection, is a crucial metric in cybersecurity. The longer attackers go undetected, the more damage they can inflict.
Why dwell time is important
The dwell time is important for a number of reasons: first of all, it represents a critical moment in the infection cycle in a multi-staging attack. It is an ‘unguarded’ moment, when security systems often fail to perceive the threat. Checkpoint itself explains very clearly that Security Orchestration, Automation and Response (SOAR) platforms, which are responsible for organising and responding to incidents, often remain inert because they do not detect the threat at this very early stage.
During these early moments, the threat begins to compose itself and thus begins to assume what will later be the most threatening and devastating configuration expressed by the malicious programme. The reason why SOAR platforms fail, according to Checkpoint, is because‘these systems often operate within isolated data silos, leading to fragmented visibility and delayed responses‘. Then there are other issues related to the volume of alerts that, even captiously, could lead SOC team experts to underestimate or ignore those that are actually real.
Checkpoint also emphasises the usefulness of artificial intelligence support in managing these phenomena and supporting SOC teams as it“enables faster and more accurate detection and response, harnessing the power of AI and automation to improve TDIR (Threat Detection and Incident Response)processes “. This was the subject of a lecture at MEDDLE held in Milan and an article you can read here.
Dwell Time and Attack Phases
To get a good understanding of where dwell time fits into a data breach, please refer to the diagram below. Imagine a normal ransomware attack:
- Step 1: The hacker starts the exploitation and installation phases of the malicious applications.
- Step 2: The hacker gains control over the system and starts the exfiltration phase.
- Step 3: The hacker starts the data encryption/deletion activity.
Dwell time corresponds to the entire phase two, which is why the more correct translation is dwell time. The hacker remains inside the system throughout phase two by implementing the command and control policies necessary to manage it and exfiltrate files; during this phase, his activity is silent, often invisible but constant.
In phase 3, however, there is evidence of the attack: the files are rendered inaccessible and this is noticed by all the operators and not just the members of the SOC team. One could say that ‘it’s too late now’, the hacker has already got everything he needed (control of the system and the files).
Managing dwell time
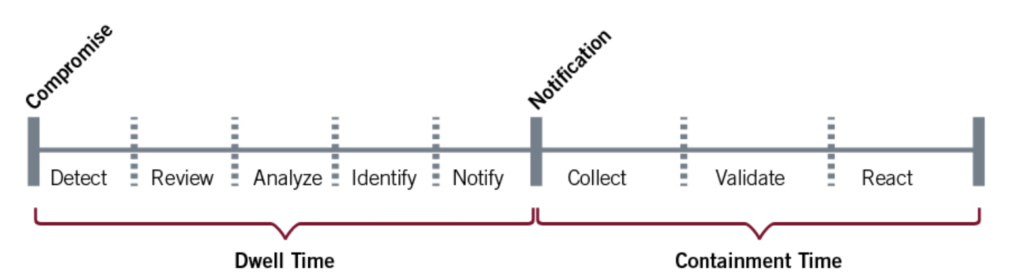
The National Institute of Standards and Technology (NIST) has published an interesting document created by the company Mandiant and entitled ‘Using Metrics to Mature Incident Response Capabilities’(link). It is worth noting that the document is not up-to-date, in fact it is rather dated (09 April 2014), but it does contain interesting information to think about and answers one question: is it possible to parameterise using the DRAIN CVR model. This is an acronym that means:
- Detect
- Review
- Analyze
- Identify
- Notify
- Collect
- Validate
- React
According to Mandiant, dwell time management must be realised through specific activities aimed at performing the actions described above. The diagram below can help to better understand the methodology proposed by Mandiant.
In Italian, we could adapt the DRAIN CVR model as follows:
| ENGLISH | ITALIAN |
|---|---|
| Detect | Determination |
| Review | See |
| Analyze | Analyses |
| Identify | Identify |
| Notify | Notification |
| Collect | Collect |
| Validate | Valid |
| React | React |
It is also important to note that Mandiant divided the DRAIN moment from the CVR moment: the former is composed of investigation and reporting actions that belong to the dwell time. The second involves containment activities.
How long can a dwell time last?
There are very interesting cases of extremely long-lived data breaches, and those who claim that the dwell time only lasts a few days or even hours are simply wrong. In the article‘Breach Detection | Controlling Dwell Time Is About Much More Than Compliance‘ by R. MacMillan it is written‘according to the latest M-Trend reports , the average global dwell time is 99 days. The EMEA and Asia-Pacific regions fare even worse, averaging 106 days for Europe, the Middle East and Africa, rising to 172 days in Asia.”
The class action brought against Noodles & Co last year was based in part on the company’s liability for allowing malware to persist undetected for such a long period of time, in which case the dwell time was about five months.
Source: ‘Breach Detection | Controlling Dwell Time Is About Much More Than Compliance’ by R. MacMillan
It is therefore important to realise that thedwell time is a critical issue in cybersecurity management.
Configuration inconsistencies
If, therefore, on the one hand there is a need to intervene on the platforms, adopting the most advanced, sophisticated and responsive ones, on the other hand there is an obligation to ask oneself some questions regarding configuration control. The recent measures of the Data Protection Authority (e.g. 10002324 on the company LazioCrea S.p.A., or the 10002287 on the Lazio Region, or the 9941232 on the ASL Napoli 3 Sud) show how little attention is paid to the basic rules of computer security. Traffic filtering rather than network segmentation is the basis for any IT infrastructure and its absence will not make the work of security systems any easier.
Not to mention that, very often, the aforementioned security systems are installed in ecosystems that are dated, outdated or even already compromised by threats present on the servers. Under such conditions, it therefore becomes difficult, if not impossible, to obtain results that are at least appreciable. There is therefore a basic inconsistency: I cannot guarantee the security of systems if they are badly configured or operate at too low or insufficient security.
Conclusions
Dwell time is a problem, especially since the actions carried out by the hacker during this period are not always such as to prompt the activation of security measures. It is therefore essential to have, on the one hand, well-functioning systems and, on the other hand, correct control mechanisms (both on a technical and operational-methodological level) without which it is almost impossible to achieve satisfactory results. Artificial intelligence is undoubtedly able to support monitoring and identification activities, not so much of the individual behaviours carried out by the hacker, but of the results from these that could be problematic.

